Identity Mapping
Identity Mapping¶
Post cluster provisioning, the Identity Mapping feature helps the users to create a static mapping between IAM Users and Roles, and Kubernetes RBAC groups. This allows users/roles to access specified EKS cluster resources in AWS Console.
Create IAM Mapping¶
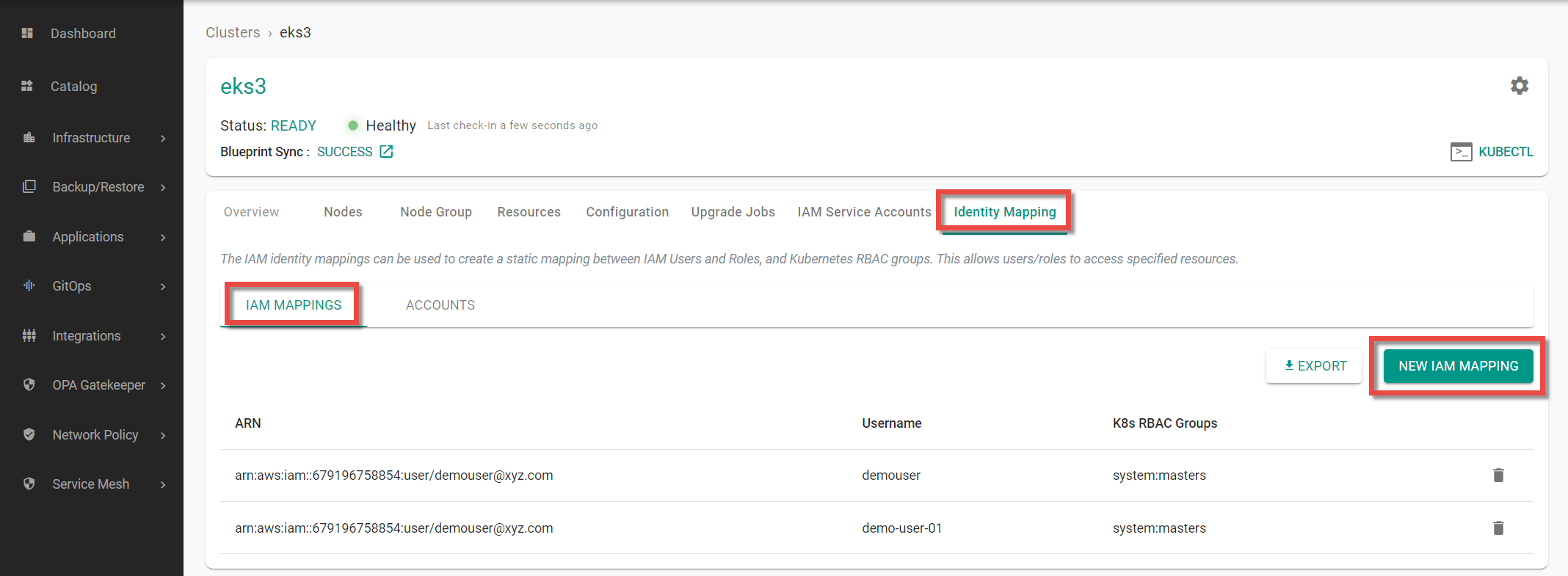
- Login to the controller and click Clusters
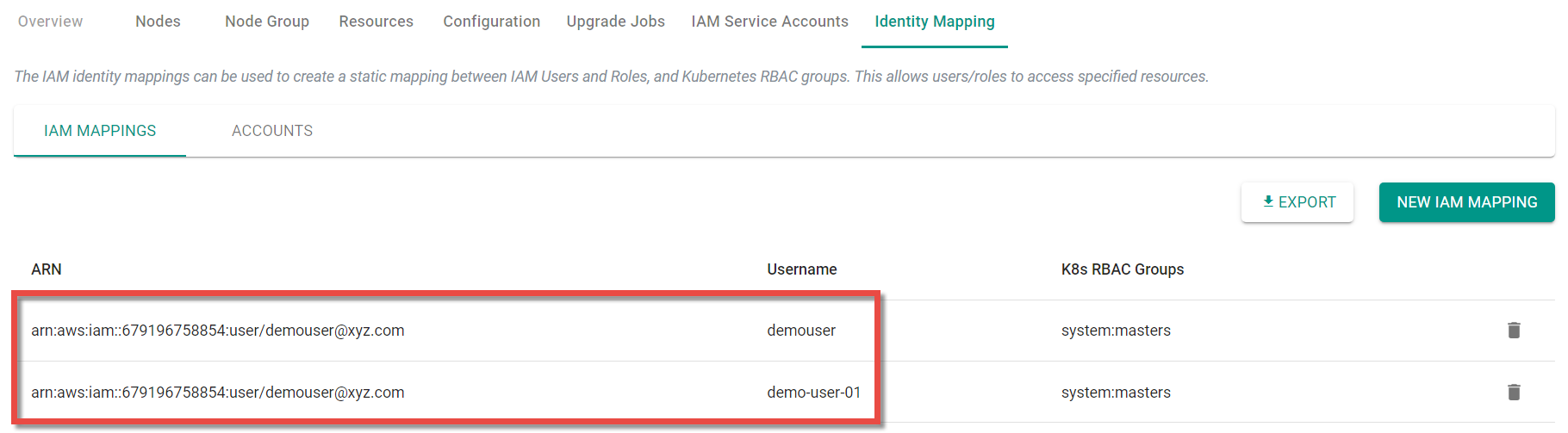
- Select the required provisioned cluster and click Identity Mapping tab. IAM Mappings tab is selected by default. You can see a list of ARNs if already created as shown in the below example
- To create a new IAM Mapping, click New IAM Mapping
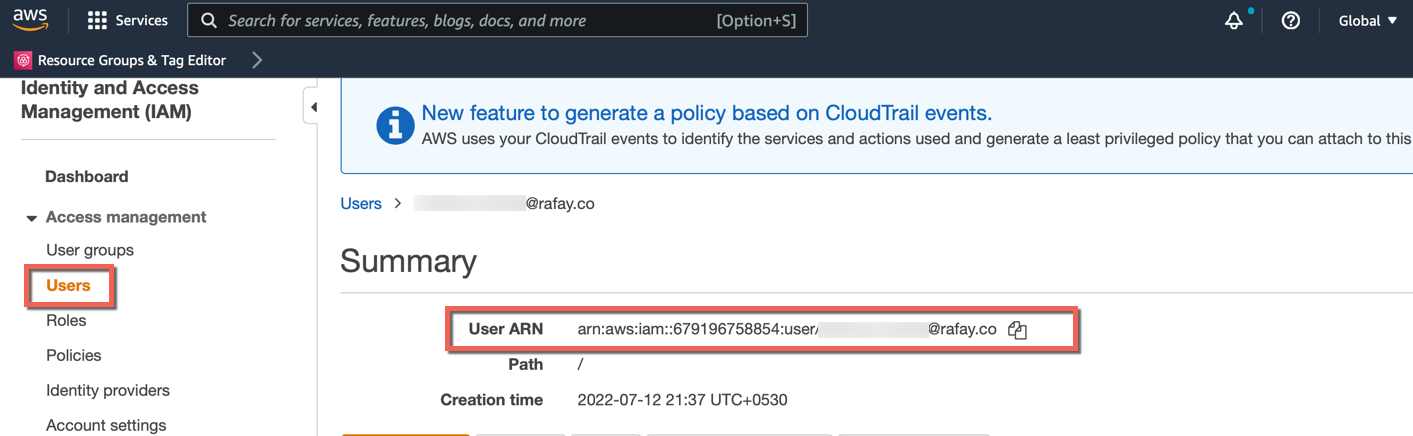
- To allow different users to access specified cluster resources, copy/paste the EKS Cluster Users ARN from AWS portal and provide the user name
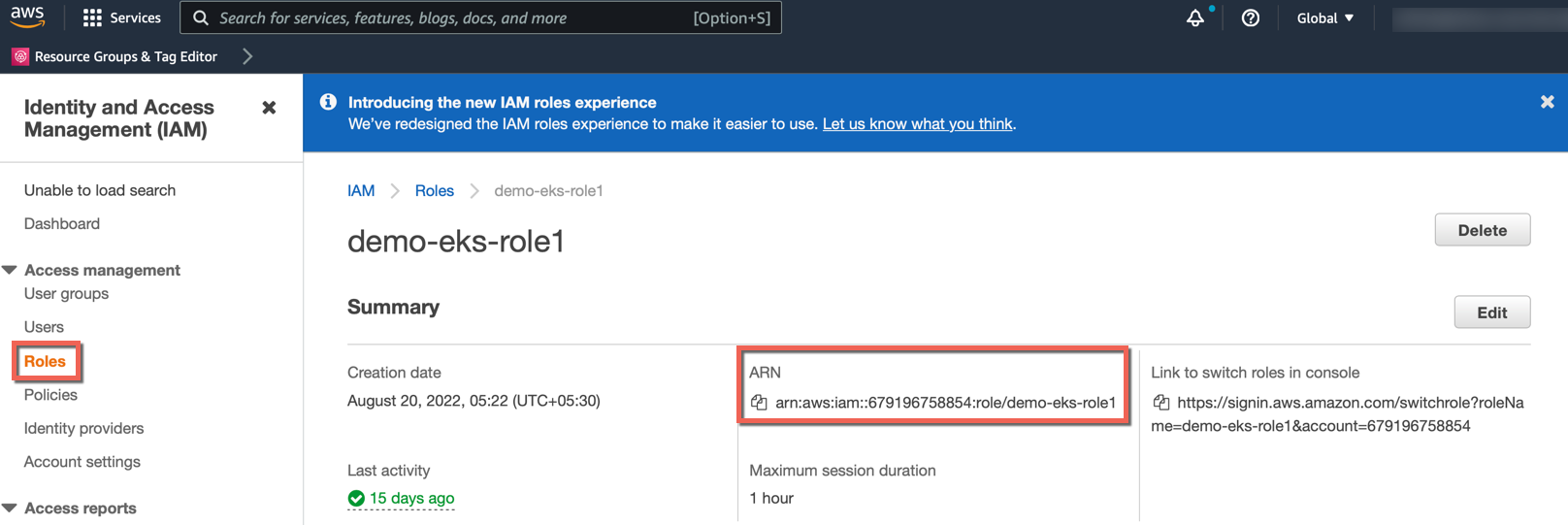
- To allow different roles to access the specified cluster resources, copy/paste the EKS Cluster Role ARN from the AWS portal and provide the user name
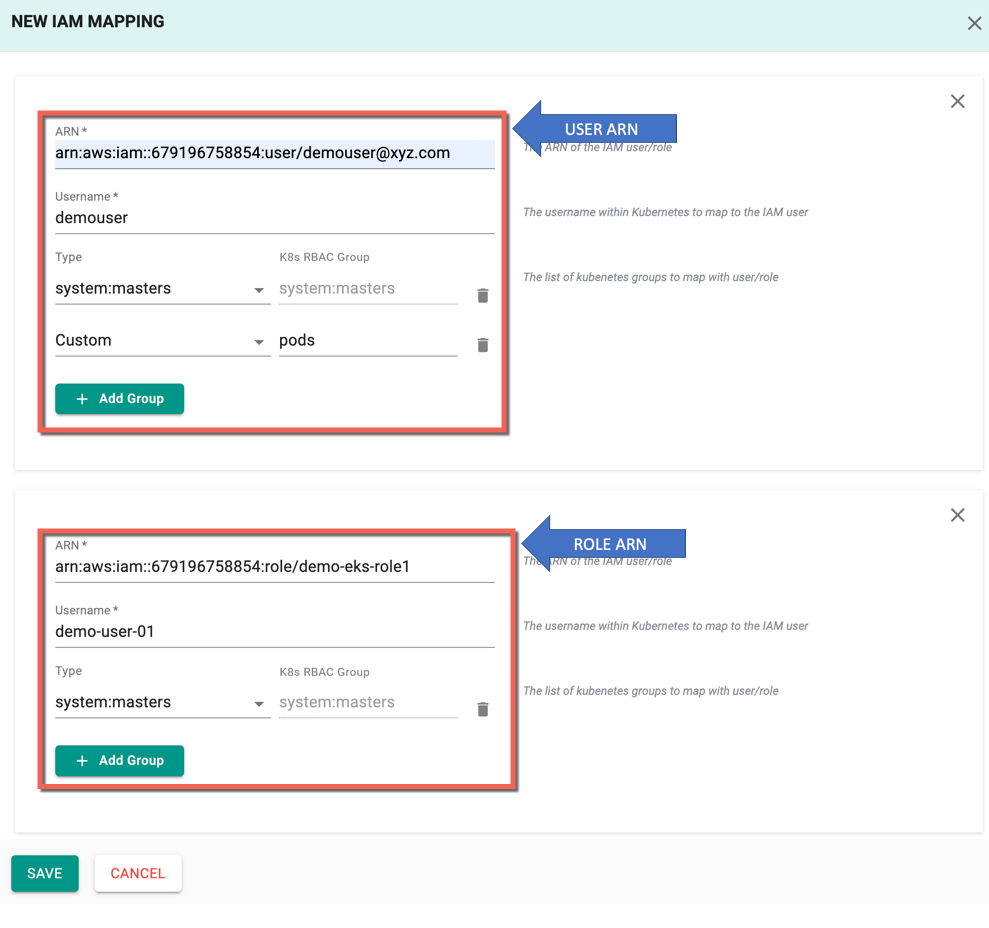
- Select the type system:masters to provide access to all the resources of the cluster (or) select Custom to provide access only for a group of resources. Users can add one or more groups to an IAM Mapping and also can create multiple IAM mappings
Below is an example of both USER and ROLE IAM Mapping
- Click Save
Once the mapping is successful, you can view the ARNs in the table as shown below
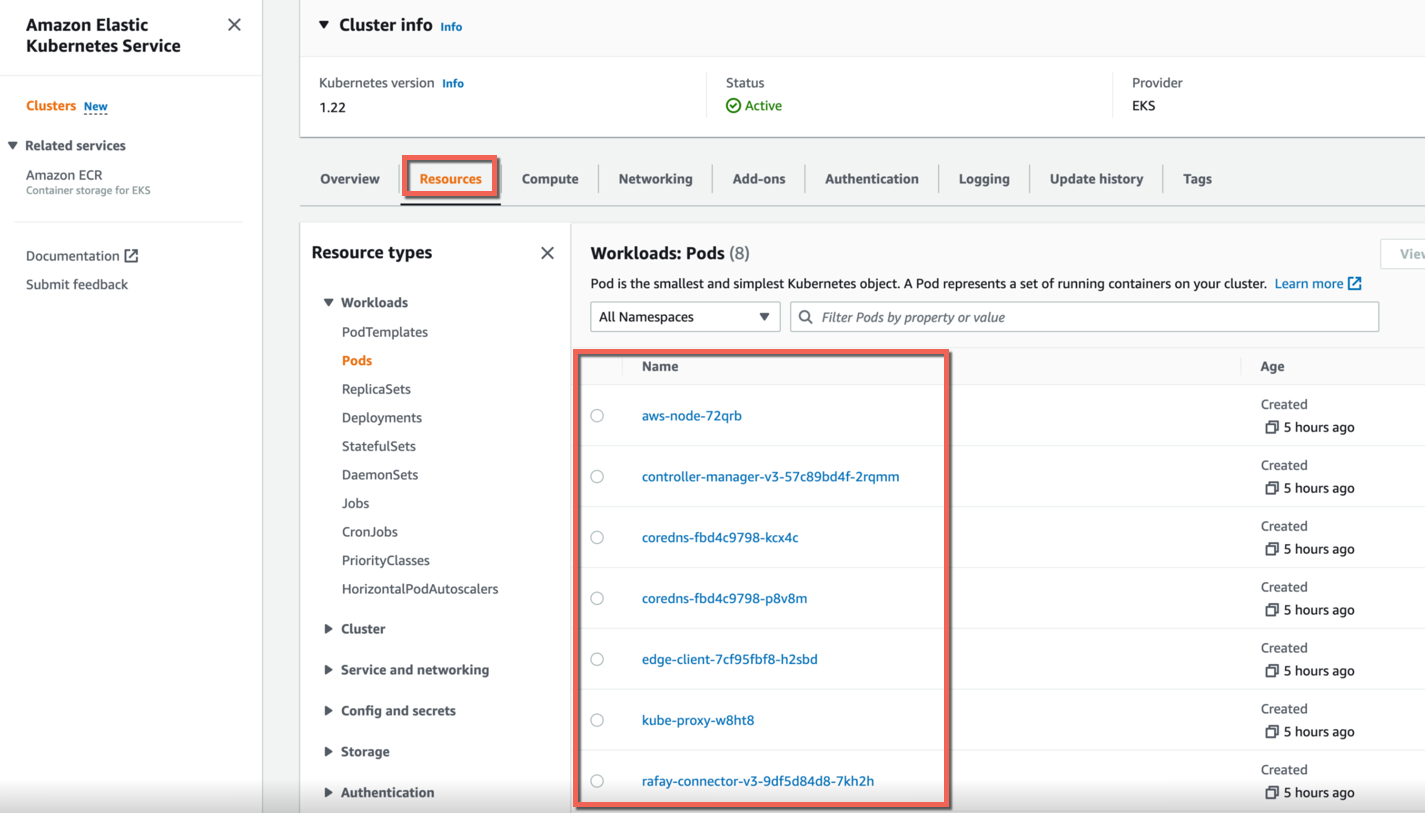
Now the users can access the cluster resources via AWS Console
To add IAM Mappings during cluster provisioning, refer IAM Mapping CLI
Delete IAM Mapping¶
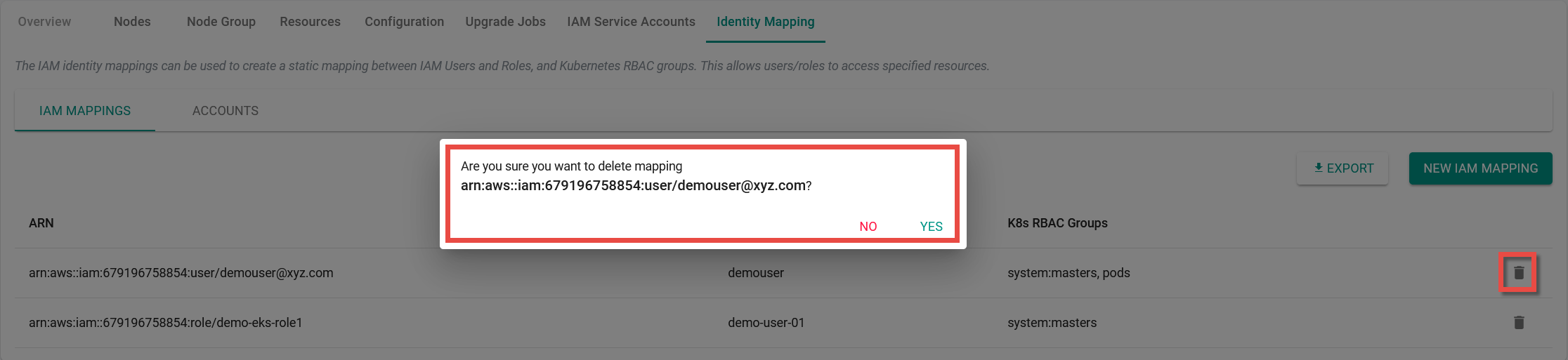
- To delete the IAM Mapping and remove the cluster access from the users/roles, click the delete icon
- Click Yes to complete the deletion
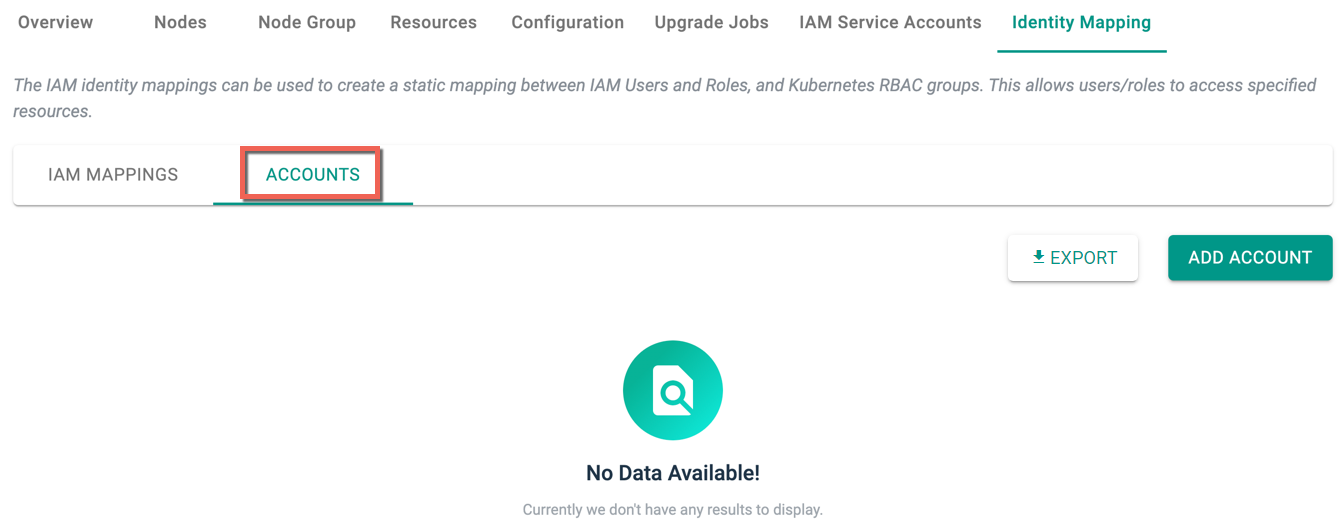
Accounts¶
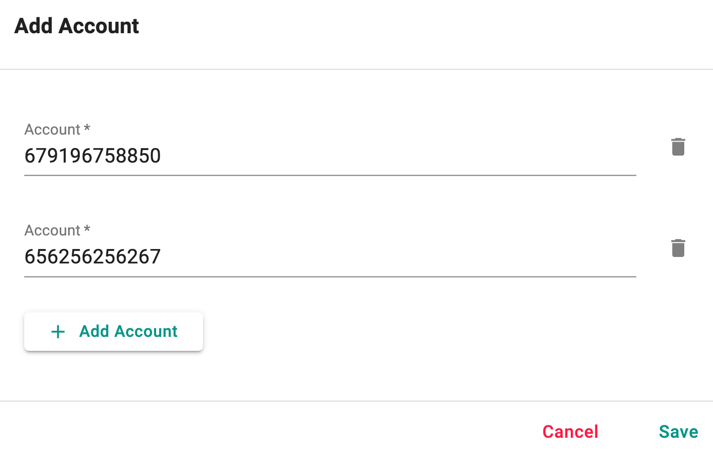
Accounts tab allows the users to add one or more accounts. This helps to provide access to clusters available in different accounts
- Click Add Account to add the required account(s)
- Enter the account(s) and click Save
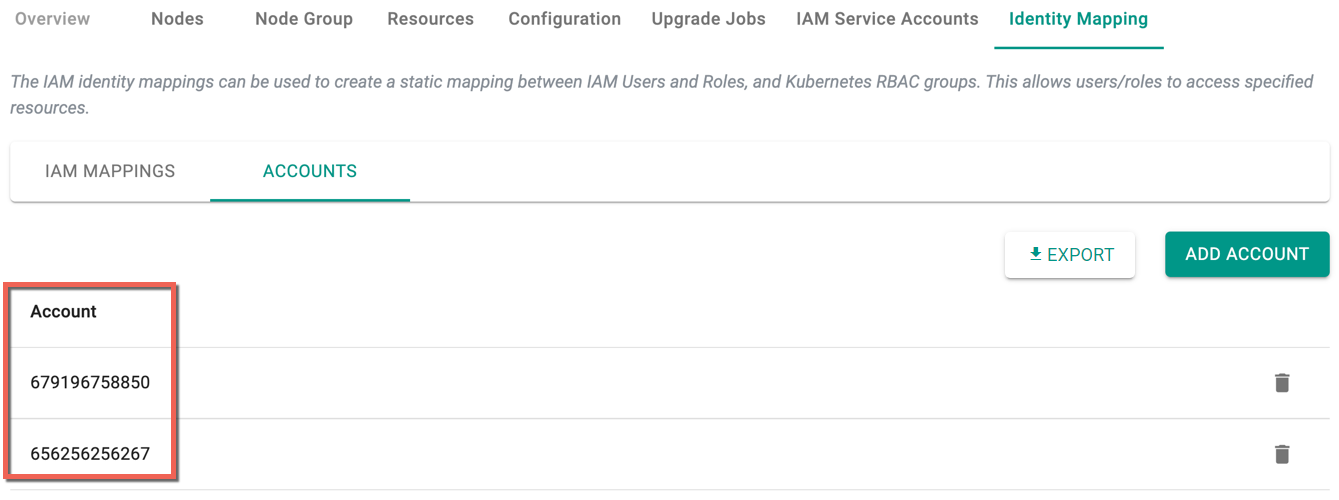
Once the accounts are added, you can view the newly added accounts in the table as shown below
The arn of respective accounts are used to create an IAM Mapping
Use the delete icon to delete one or more account(s)