Use Secret Sealer
The secret sealer feature can be used to secure the sensitive data of the resources in the following two ways:
- System to Git Sync: To secure and sync the required resource variables from system to git, set the variable's type to Secure Text through the controller
- Git to System Sync: To secure and sync the resource details from Git to System, use the Kubeseal utility
System to Git Sync¶
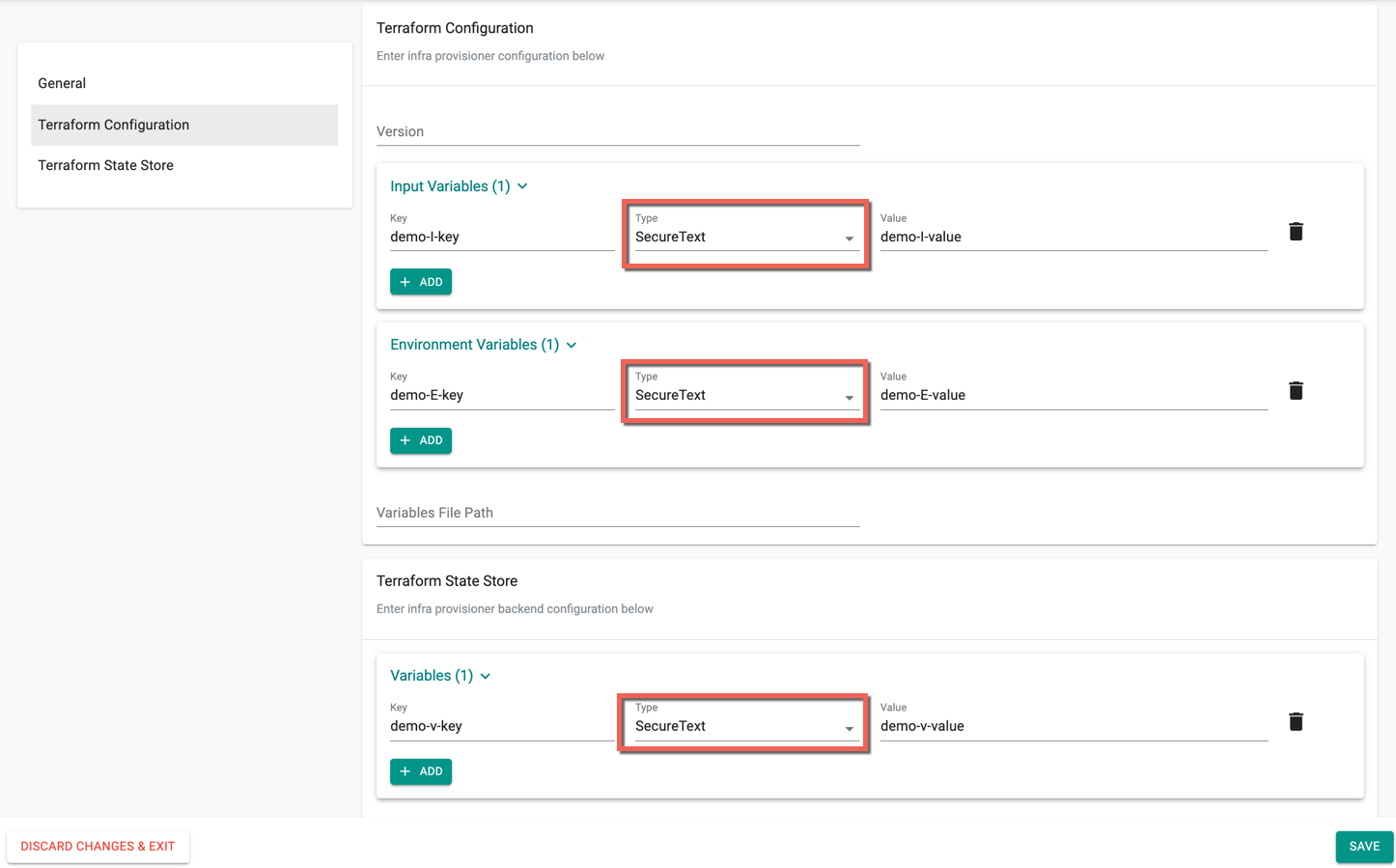
Below is an example to secure the Infrastructure Provisioner resource values and sync the data with Git
- Create a Secret Sealer through the controller in the required project
- To secure the Infrastructure provisioner resource values, select Secure Text for Input Variables, and Environmental Variables from Infrastructure Provisioner Terraform Configuration page
- Click Save
The system automatically applies the secret sealer certificate for this resource and encrypts these values. Similarly, follow the same procedure to secure the pipeline and repository resources
Git to System Sync¶
Pre-requisites
- Install the Kubeseal utility in the system
- Download the Secret Sealer Certificate
- Resource secret yaml file (that contains sensitive data to be encrypted)
Below is an example to secure the resource values in a yaml file before initiating the Git to System sync process.
- Have the Kubernetes secret file named secret.yaml. In this example, the value of the token, password must be encrypted
apiVersion: v1
data:
password: 3332hwX0x5SXZNZmp6VWRrZTdlajJ5TEhYaDFXNGIwdQ==
kind: Secret
metadata:
name: secret_name
- Run the command
kubeseal --cert CERT--format yaml < secret.yaml > sealsecret.yaml where,
- CERT: Certificate downloaded from the Secret Sealer
- secret.yaml: Kubernetes secret file
-
sealsecret.yaml: The generated output file name with encrypted values
-
On successful command execution, users can view the generated output file sealsecret.yaml where the password is encrypted/sealed
apiVersion: bitnami.com/v1alpha1
kind: SealedSecret
metadata:
creationTimestamp: null
name: secret_name
namespace: default
spec:
encryptedData:
password: AQCC0GxGS5d7SW8EDtz52pPjSI6gXvivyTSJ3m7p+3s+Ryn1P54V3avPPm2qXEuTpNPSkYSGpZ1+/11xvr36IpNhcic8liNz9aHeCWRUOzvTuEulAEljkO2uXq3BR+EZcdSJGrq41N209U1EyME/fp6u67+UZTpK+8znJJfXrmaOCuJVenmXKGfzCeia9fc2qcNx8gtd5PCGsOPuWhXd6RWuwhUW76ZTzHzK5gOZiojFpI2RZMQiSXyg0/1iGdQNnT7iByGWfbqpeFA5GkmTbwaKDwt5kgvLpEO2fuRUn5TrA8vkEcqe7N/I2yYMRxi6KZAgMGWTRWa0jn8rIBR0yzMj/qRP9WzySZ22Rbx1j5byZqEd1DRWgGWC8hg4lSkisTsBD9L04pvwB1BHe4pvlemxMXk37601znY=
template:
data: null
metadata:
creationTimestamp: null
name: secret_name
namespace: default
- The sensitive resource values are encrypted. Users can now upload this sealed yaml file to Git and sync with the system