Configure IRSA
Users must create a ServiceAccount with role arn and use this Service Account in deployment. Perform the below steps to create a service account with role arn.
Important
For Amazon EKS clusters provisioned and managed through the platform, follow the instructions here to create IRSA accounts.
Step 1: Create Identity Provider¶
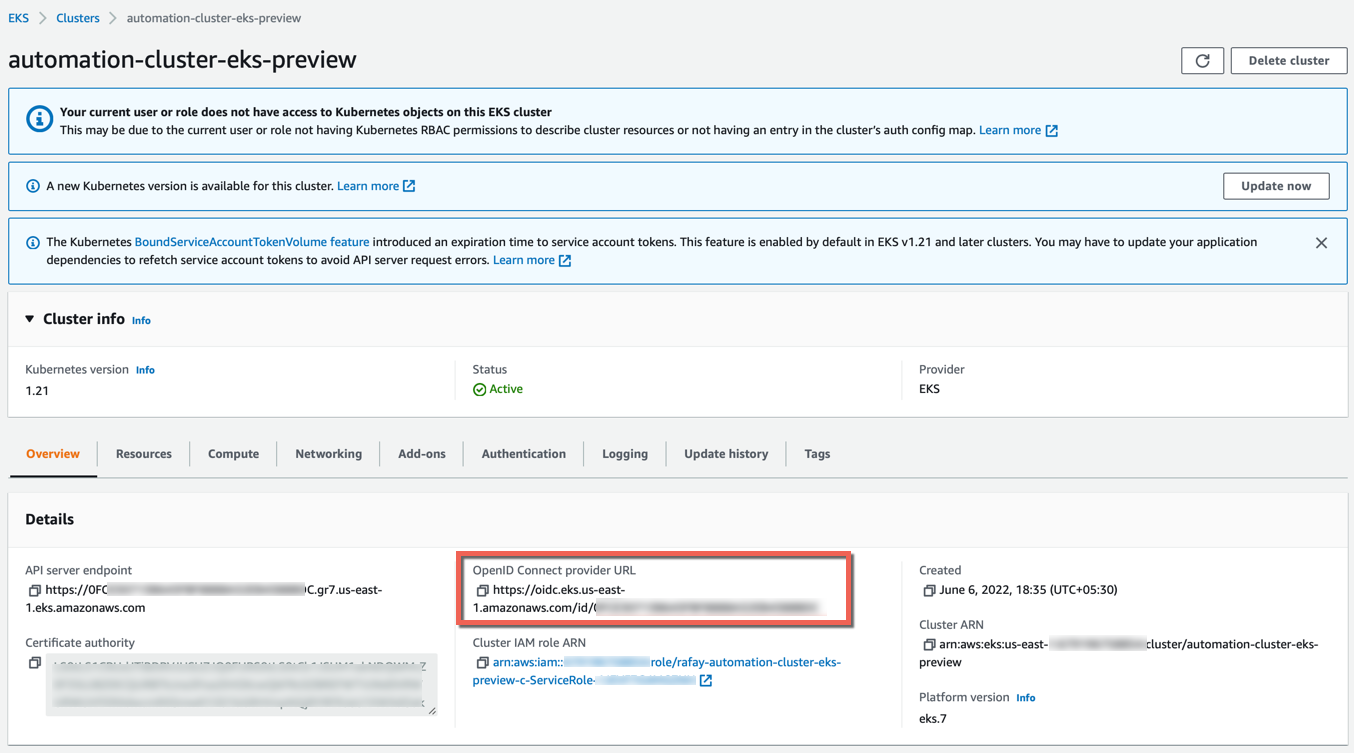
- In the AWS Portal, navigate to EKS Cluster → Configuration → Details. Copy the OpenID Connect Provider URL
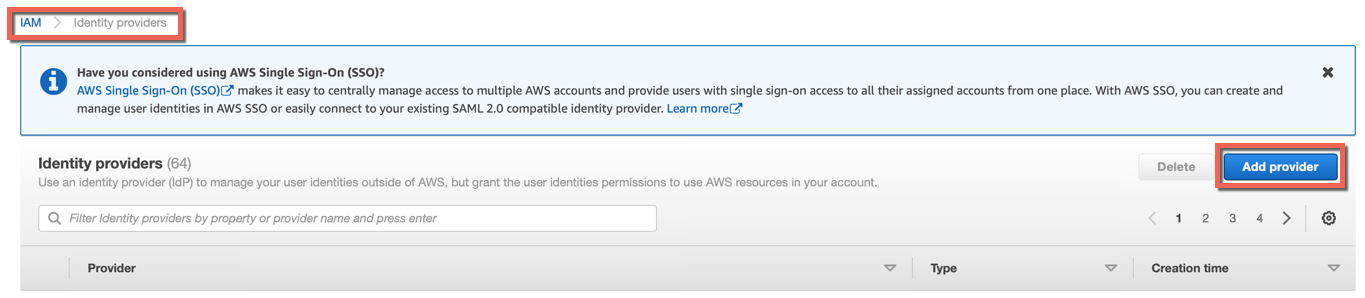
- Navigate to IAM → Identity Providers and click Add Provider
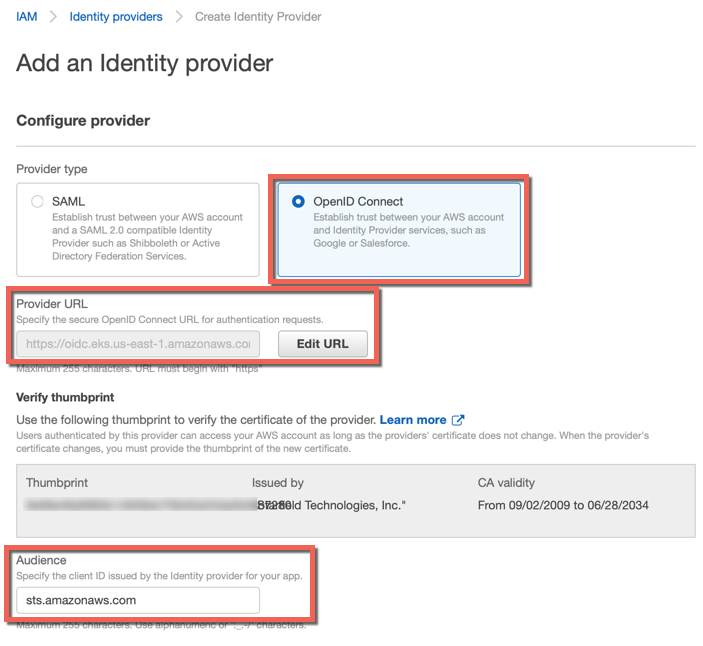
- Select the Provider type OpenID Connect
- Enter the Provider URL (copied from EKS Cluster Config Details page) and click Get thumbprint
- Enter sts.amazonaws.com in the Audience field
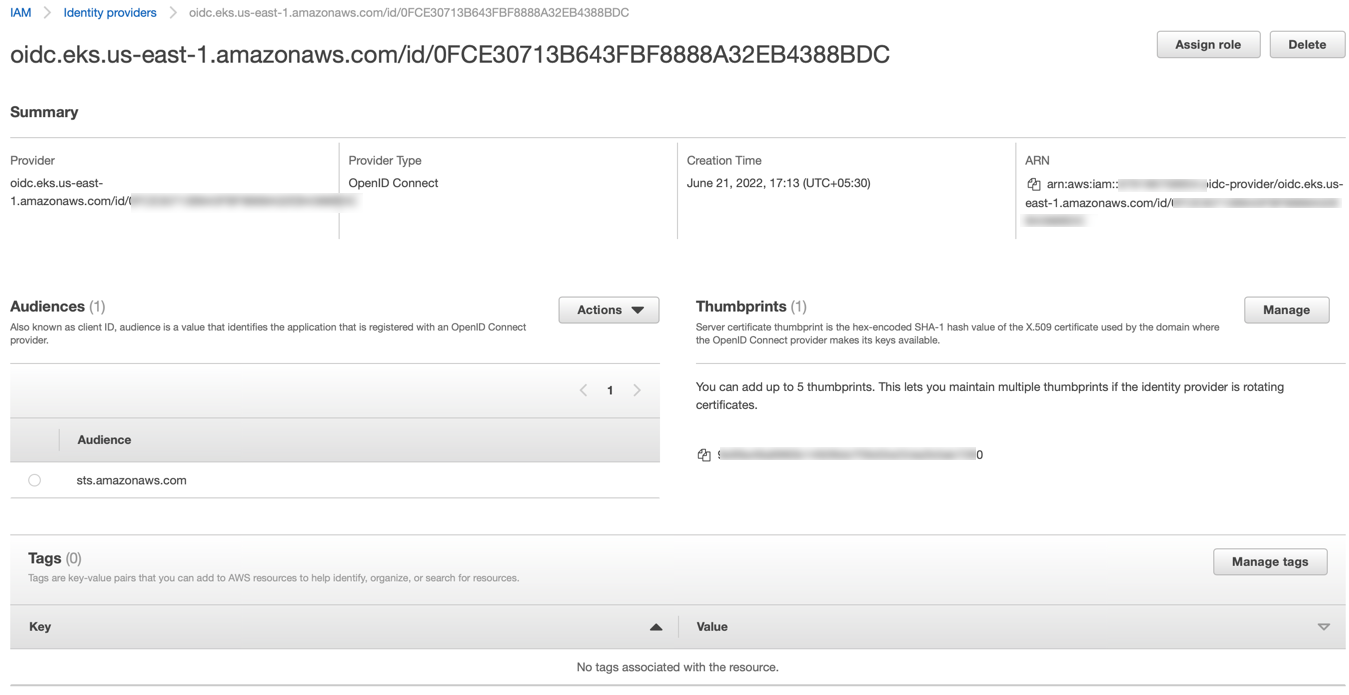
On successful creation, you can view the details as shown below
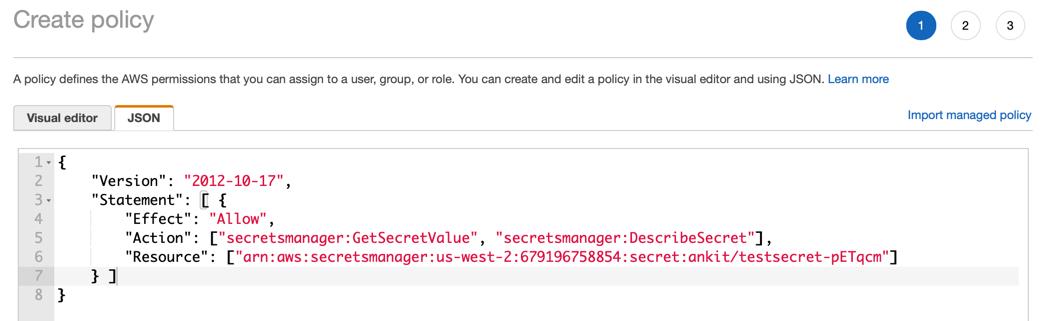
Step 2: Create Policy¶
- Open the Policies page and click Create Policy with the below json code
{
"Version": "2012-10-17",
"Statement": [ {
"Effect": "Allow",
"Action": ["secretsmanager:GetSecretValue", "secretsmanager:DescribeSecret"],
"Resource": ["arn:aws:secretsmanager:us-west-2:999999999999:secret:ankit/testsecret-pETqcm"]
} ]
}
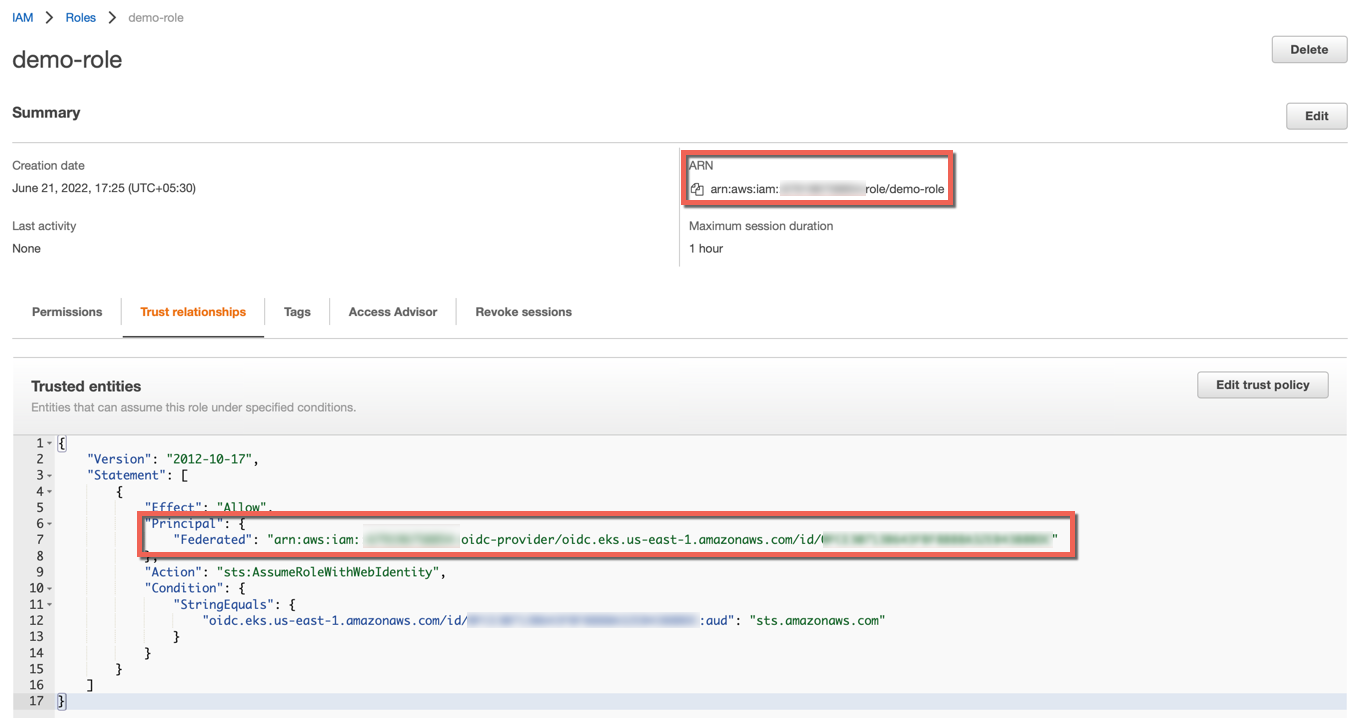
Step 3: Create Role¶
- Create a role and attach the above created policy. The role must have the following Trust Relationship
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::679196758854:oidc-provider/oidc.eks.us-west-2.amazonaws.com/id/885AEC39E08218CEB539793D69F00B58"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"oidc.eks.us-west-2.amazonaws.com/id/556BEB39E97564CEB542613H80G00B61:sub": "system:serviceaccount:newns:test-sa",
"oidc.eks.us-west-2.amazonaws.com/id/556BEB39E97564CEB542613H80G00B61:aud": "sts.amazonaws.com"
}
}
}
]
}
- Replace the Principal parameter with the Identity created in Step 1
Users can now use this Role ARN as part of Annotations to dynamically retrieve secrets from AWS Secrets Manager.