Releases - July 2023¶
v1.27 - SaaS¶
28 July, 2023
This section below provides a brief description of the new functionality and enhancements in this release.
Amazon EKS¶
Managing Multiple member accounts through one service account¶
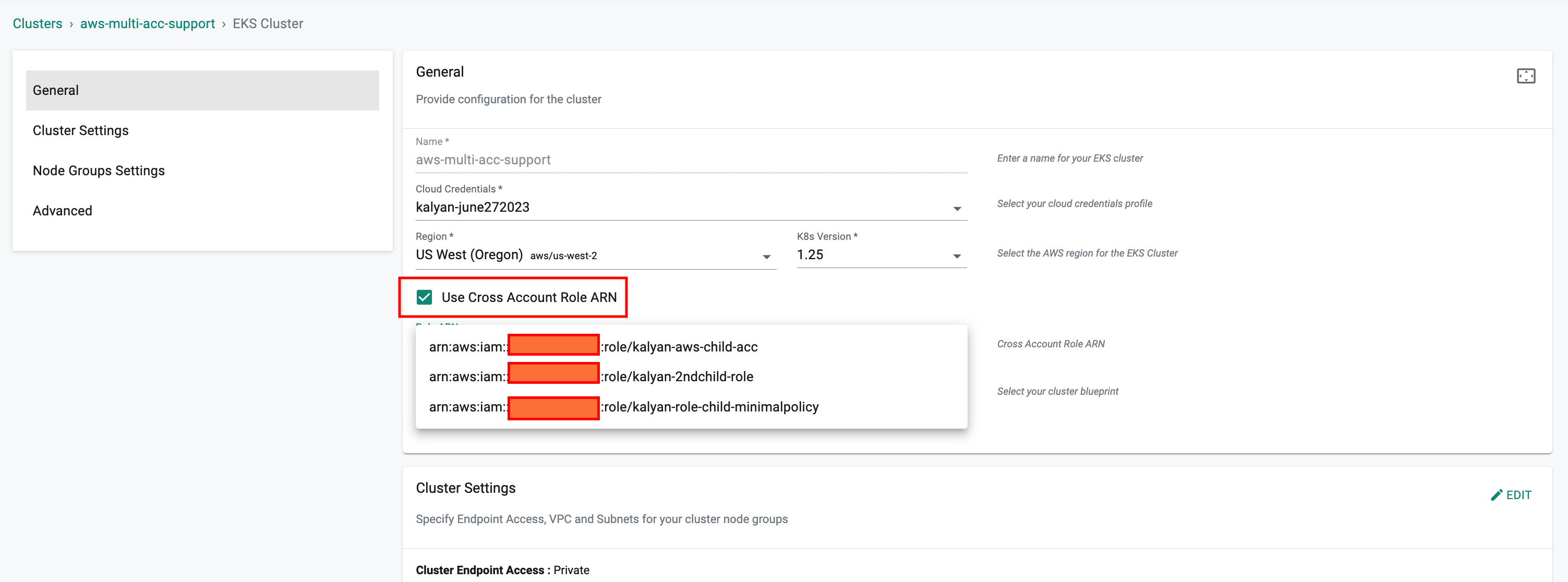
It is possible now to deploy new EKS clusters using multiple AWS accounts with the help of IAM AssumeRole functionality. Instead of sharing AWS credentials from different accounts, IAM roles provide access to AWS resources/APIs across multiple accounts.
When creating an EKS Cluster, an option is available to enable the Use Cross Account Role ARN feature. This feature allows creation of EKS clusters in an AWS account other than the main AWS account.
Kubernetes v1.26¶
A previous release added support for provisioning new EKS clusters based on Kubernetes v1.26. This release adds support to upgrade existing clusters managed by the controller in-place to Kubernetes v1.26.
RCTL enhancements¶
Users can now upgrade node groups in parallel using the RCTL cluster configuration file translating to reduced upgrade time.
Upstream Kubernetes for Bare Metal and VMs¶
Kubernetes v1.27¶
New upstream clusters can be provisioned based on Kubernetes v1.27.x. Existing upstream Kubernetes clusters managed by the controller can be upgraded in-place to Kubernetes v1.27.
CNCF Conformance¶
Upstream Kubernetes clusters based on Kubernetes v1.27 (and prior Kubernetes versions) are fully CNCF conformant.
VMware vSphere clusters¶
Kubernetes v1.26¶
New VMware vSphere clusters can be provisioned based on Kubernetes v1.26.x. Existing upstream Kubernetes clusters managed by the controller can be upgraded in-place to Kubernetes v1.26.
Clusters¶
Labels¶
With this release, the parent project name is added as a system label to clusters to make it easier to manage configurations such as cluster overrides.
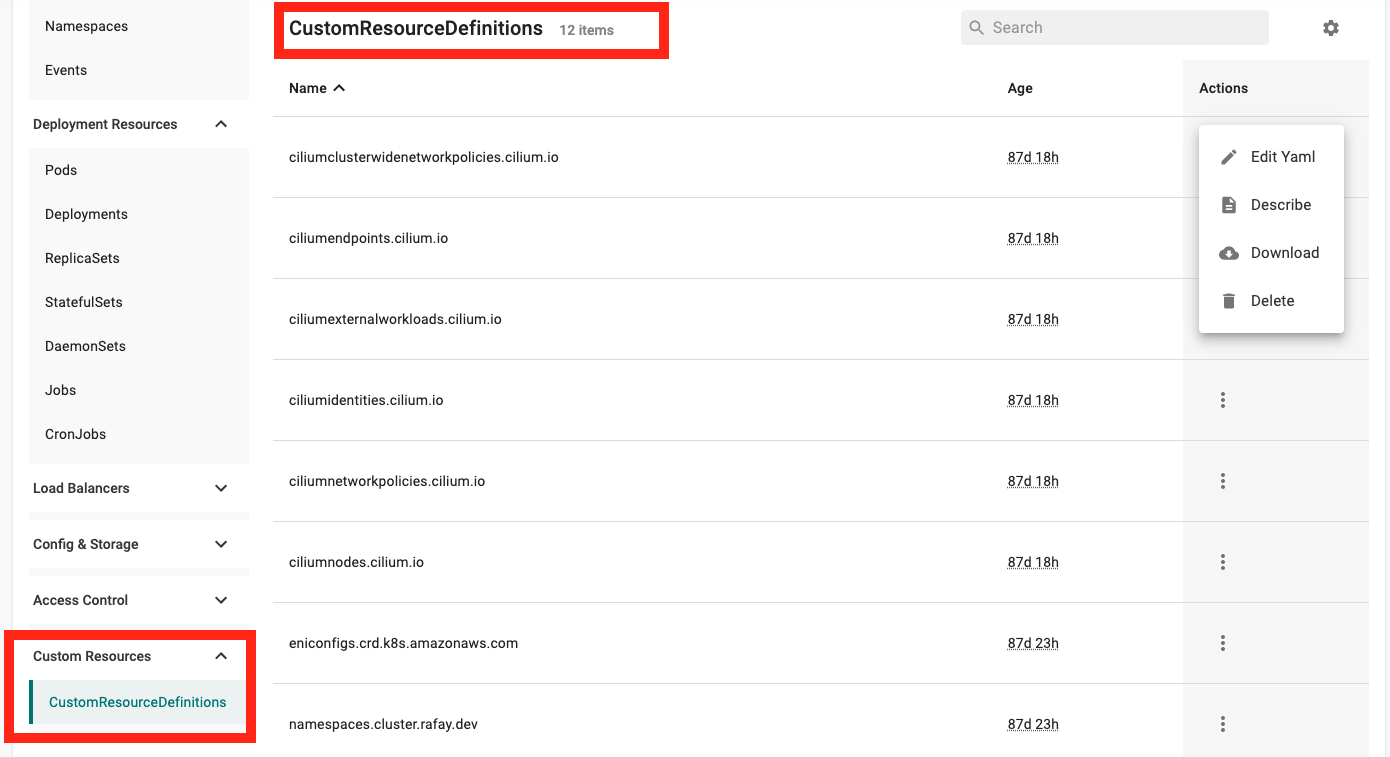
Visibility into K8s Resources¶
Visibility into CRD and HPA resources has been added to the K8s Resources dashboard with this release.
Create K8s Resources¶
Administrators are now provided with intuitive workflows to quickly and efficiently "create" Roles, RoleBindings, HPAs, CRDs and Service Account resources directly from the inline Kubernetes resources dashboard.
API Keys and RCTL Config¶
Configurable expiry¶
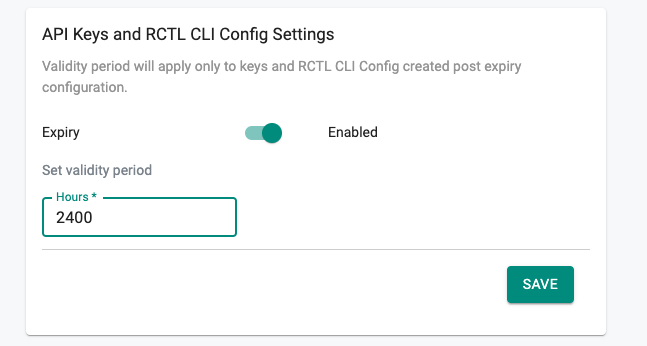
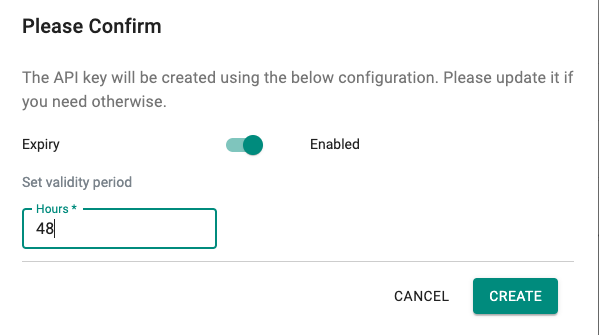
With this release, it is possible to set an expiry period (org wide) for API keys & RCTL Config. It is also possible to configure a different expiry period selectively for users.
When the user generates an API key or downloads a RCTL config, the user is provided an option to select the validity period. The validity period cannot exceed the org wide setting (or the value configured specifically for the user).
An additional column has been added to the API keys page to capture the 'Last Used' time.
Zero-Trust Access¶
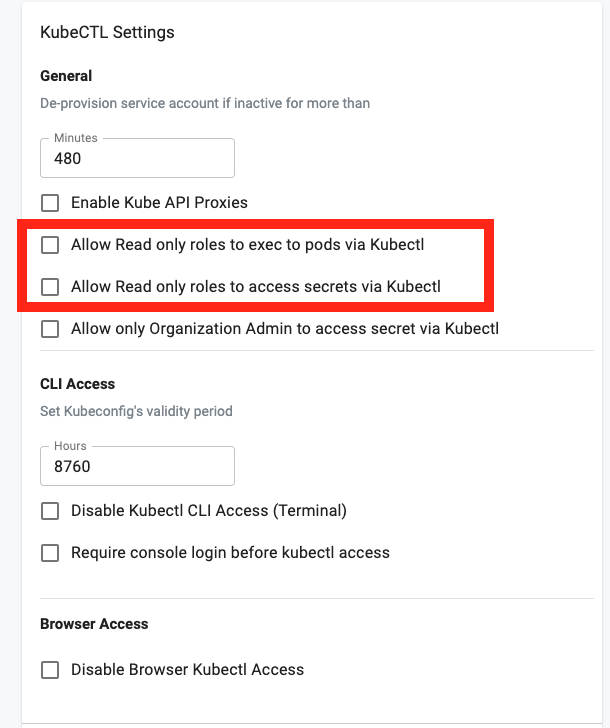
Read Only Roles¶
By default, read only roles are not allowed to access secrets or exec to pods. KubeCTL settings have been enhanced to add these as configurable options to allow Org Admins to optionally enable this if required to provide a streamlined developer experience.
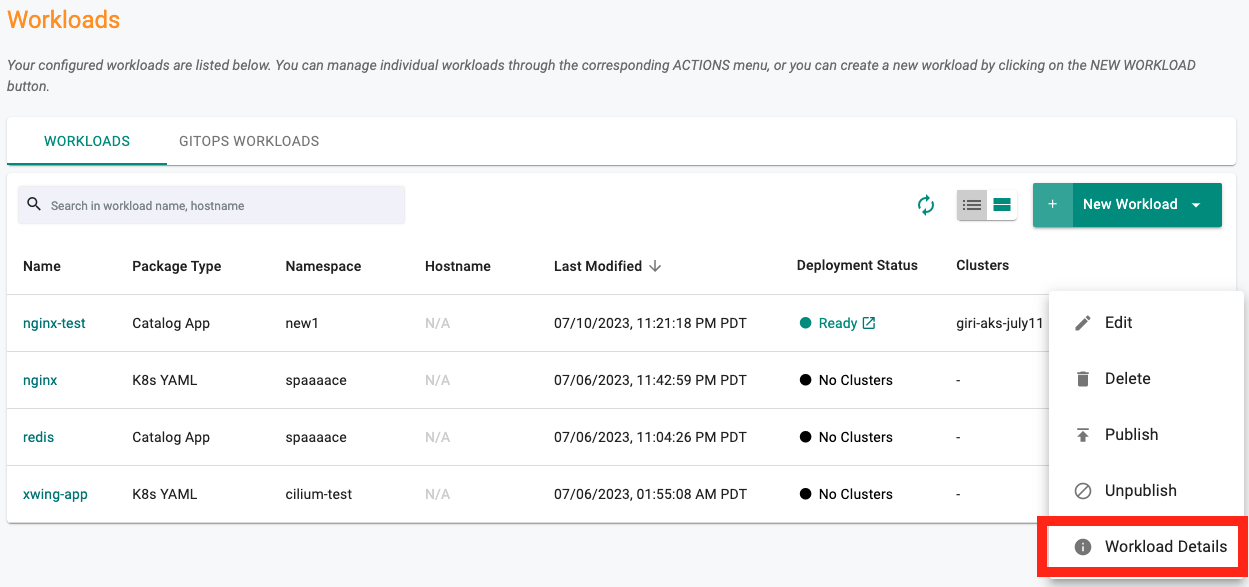
Workloads¶
Details¶
Information on all deployed container names and their respective versions is displayed to enable a better experience for users.
Cost Management¶
Deleted resources¶
With this release, deleted resources (such as clusters, namespaces, projects) will continue to be displayed within the Cost Overview dashboards and will also be available for selection as part of chargeback group configuration.
Catalog¶
Additions to System Catalog¶
The System Catalog has been updated to add support for the following repositories.
| Category | Description |
|---|---|
| App Connectivity | Cloudflare Tunnel |
Bug Fixes¶
| Bug ID | Description |
|---|---|
| RC-26594 | Resources dashboard is not loading for users with namespace admin privileges for namespaces that aren't controller managed |
| RC-27931 | UI: EKS node group is created with the default volume type instead of the selected volume type |
| RC-27383 | UI: Permission Denied error - resources are not listed in the Resources page when the user has both Project Admin and Cluster Admin roles |
| RC-28075 | EKS: eks:kube-proxy-windows is not added to aws-auth role for a Windows managed node group using custom AMI |
| RC-24627 | EKS Control plane endpoint is created as Public and then converted to Private after the provisioning is done with OIDC:True and Cluster endpoint as Private |
| RC-24598 | EKS: aws-node IRSA creation is not decoupled from withOIDC flag (to create OIDC Provider) resulting in cluster provisioning failure |
| RC-26916 | Workload Placement is not Getting updated after a Backup Restore operation |
| RC-25361 | rook-ceph cluster does not get cleaned up properly when managed storage add-on is removed from blueprint |
| RC-28571 | Error when creating an EKS or AKS cluster using a cluster template via RCTL |
| RC-28217 | UI: Cluster Resources page not getting displayed for workspace admin user |
v1.26 Update 1 - SaaS¶
7 July, 2023
This section below provides a brief description of the changes in this release.
Bug Fixes¶
| Bug ID | Description |
|---|---|
| RC-28056 | Export to csv option not working for OPA Gatekeeper violations |
| RC-28140 | Updating tolerations for system components does not update the secret-store-webhook |
| RC-28059 | Unable to publish catalog based workloads |