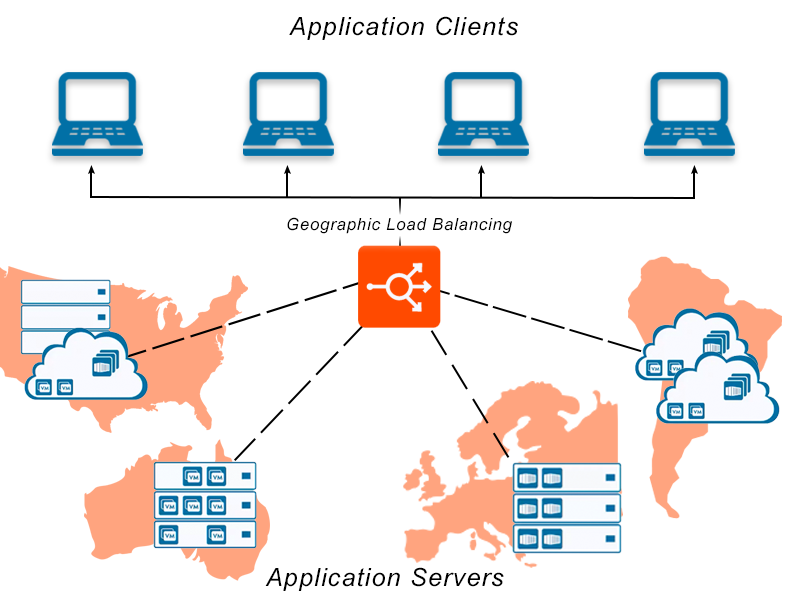
DNS based GSLB
DNS-based Global Load Balancing involves configuring a domain in the Domain Name System (DNS) such that client requests to the domain are distributed across a group of servers. This facilitates faster access to a domain by providing several IP addresses for a single host or domain name, which routes traffic between two or more servers. DNS-based Load Balancing helps optimize client requests for a specific domain.
Use Cases¶
Geo Steering or Targeting¶
For workloads deployed to multiple, geographically distributed clusters, DNS based GSLB can automatically steer users to the nearest cluster.
Failover¶
For workloads deployed to multiple, geographically distributed clusters, DNS based GSLB can automatically failover user access in case of disruptions to one cluster.
Wizard based Workloads¶
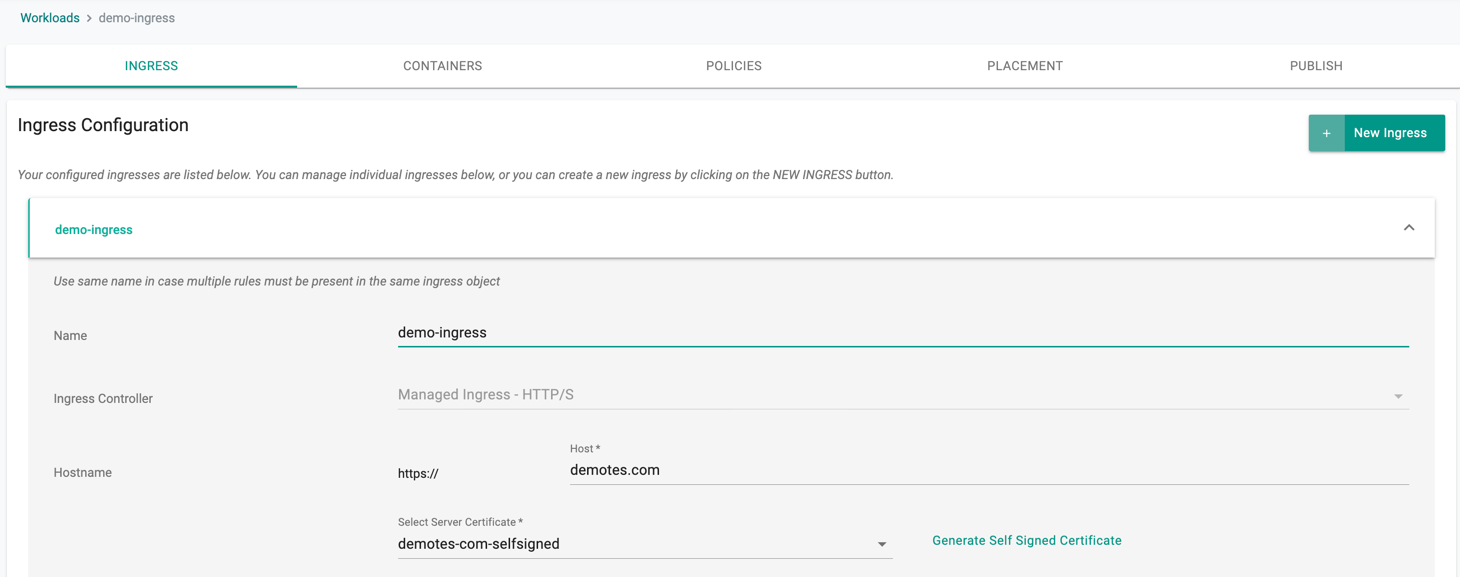
For wizard based workloads, provide the hostname as shown in the screenshot below