Access
In this part, you will
- Create a K8s YAML workload that will create a Secret Provider.
- Create a K8s YAML workload that will deploy sample application which will pull the secret created in AWS Secret Manager.
- Verify the secrets are available to the pods.
Step 1: Create Secret Provider Class¶
To take advantage of the Secrets Store CSI driver a SecretProviderClass custom resource will need to be created. This provides driver configurations and parameter specific details to the CSI driver. We are utilizing ASCP so will need to define the objects and type. In the example below we will retrieve secrets from AWS Secrets Manager and sync the defined secrets to K8s cluster secrets. Secrets are defined under the secretObjects section. Objects defined in the objects section will be mounted as files.
Important
The SecretProviderClass must be in the same namespace as the pods referencing it.
Create and Publish Workload¶
- Create a file called "ExampleSecretProviderClass.yaml" from the spec below.
- In this example, we are telling the CSI to pull username, password from MySecret in AWS Secret Manager and create a K8s secret with name complete-secret
apiVersion: secrets-store.csi.x-k8s.io/v1alpha1
kind: SecretProviderClass
metadata:
name: nginx-deployment-aws-secrets
spec:
provider: aws
secretObjects: # [OPTIONAL] SecretObject defines the desired state of synced K8s secret objects
- data:
- key: username # data field to populate
objectName: username
- key: password # data field to populate
objectName: password
secretName: complete-secret # name of the Kubernetes Secret object
type: Opaque
parameters:
objects: |
- objectName: "MySecret"
objectType: "secretsmanager"
jmesPath:
- path: "username"
objectAlias: "username"
- path: "password"
objectAlias: "password"
-
Click on Application -> Workloads.
-
Click on Create New Workload with the name "secret-provider-class".
-
Select "K8s YAML" for addon type.
-
Select "Upload files manually" for Artifact Sync.
-
Select the "nginx" namespace from the dropdown.
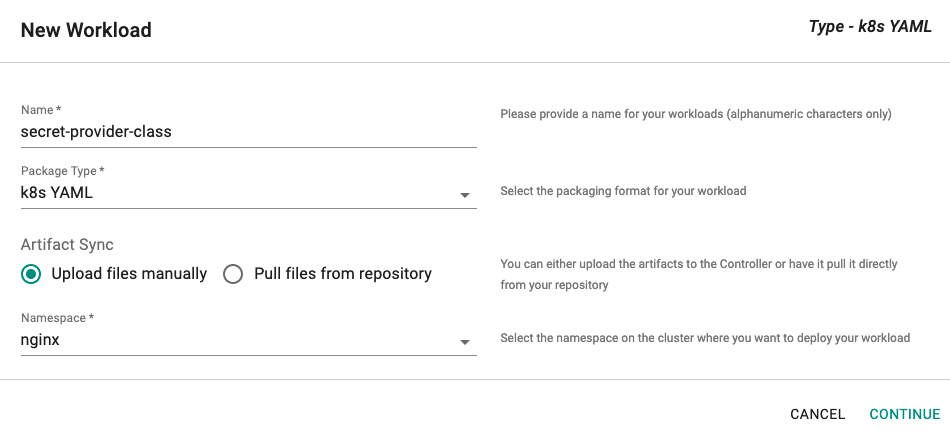
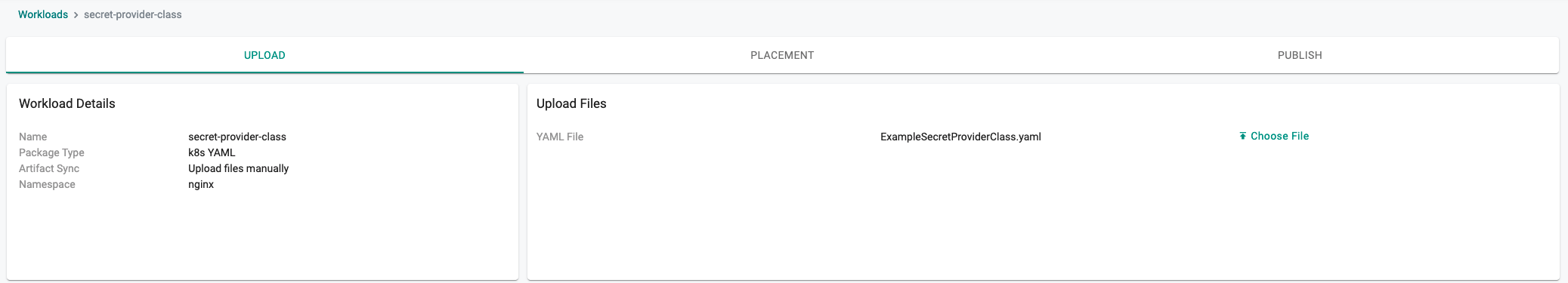
- Select the file "ExampleSecretProviderClass.yaml" created above.
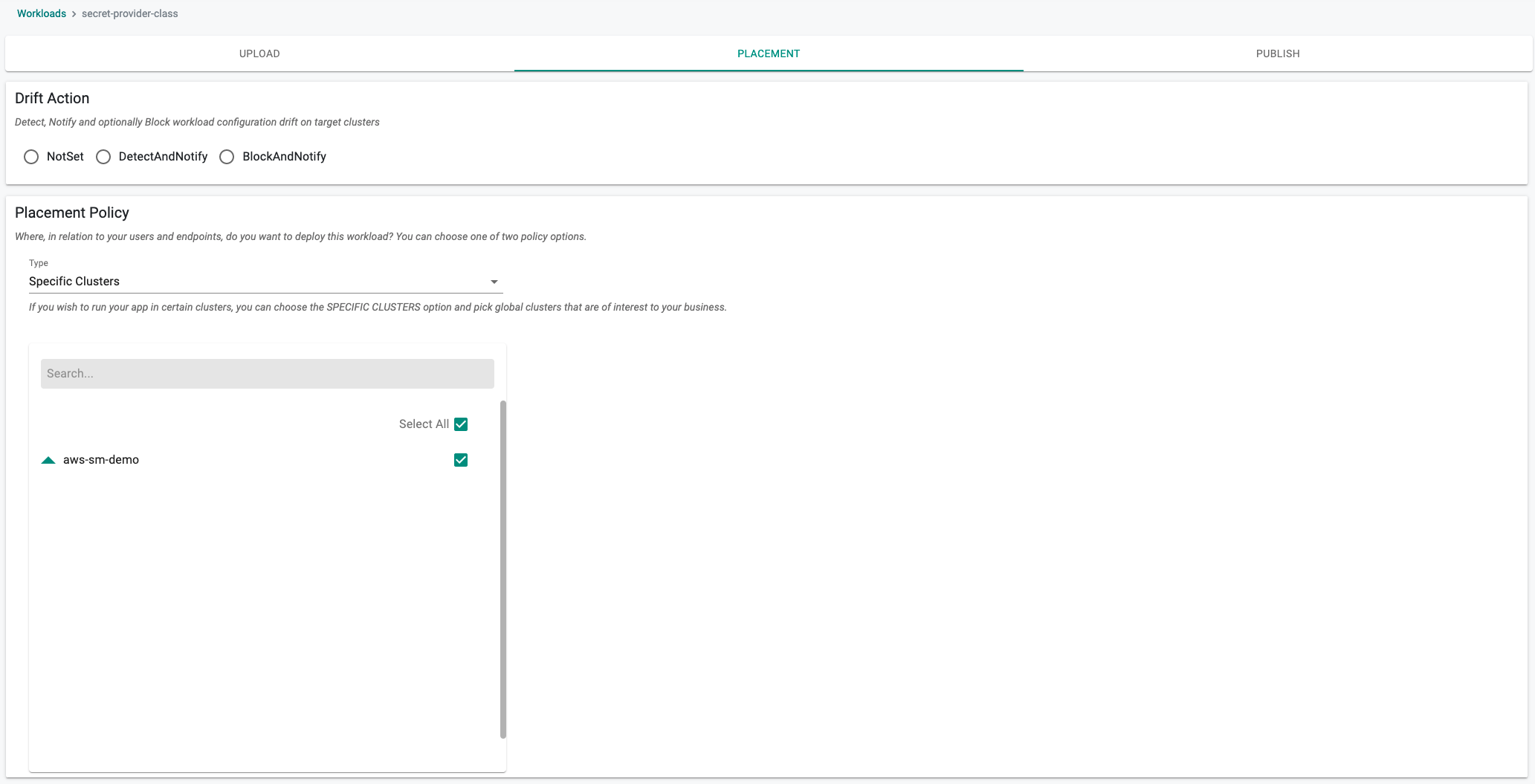
- Select a cluster for the placement policy
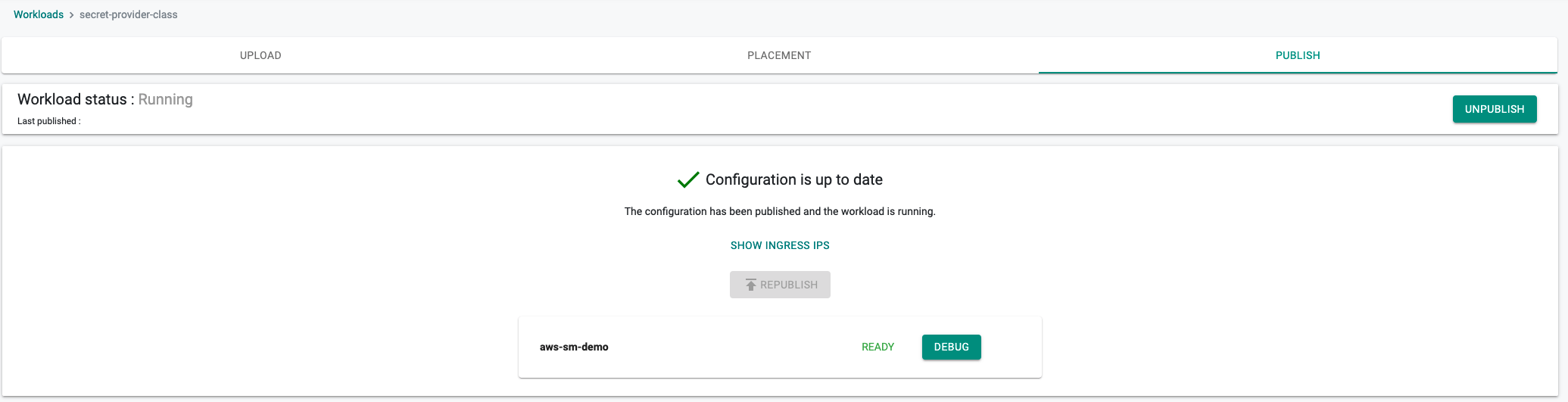
- Publish the workload
In a minute the workload should be deployed.
Step 2: Deploy Application¶
We are using nginx in this example to pull the secret from AWS Secret Manager.
In this step, we will configure and deploy a Nginx workload to the EKS Cluster. We will use a K8s YAML manifest which will incorporate the IRSA for Nginx from the prior step. The following manifest will create a service and deployment and is configure to use the SecretProviderClass and IRSA we created in previous steps so no changes are needed.
Create and Publish Workload¶
- Download the K8S YAML manifest from the Git repo.
wget https://raw.githubusercontent.com/aws/secrets-store-csi-driver-provider-aws/main/examples/ExampleDeployment.yaml
- Service Account name: It should match the name created with IRSA here
- CSI Volume: secretProviderClass is the name of the Secret Provider Class created here
- Volume Mount: Path inside the pod, secret should be mounted so that application can read
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
labels:
app: nginx
spec:
replicas: 2
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
serviceAccountName: nginx-deployment-sa
volumes:
- name: secrets-store-inline
csi:
driver: secrets-store.csi.k8s.io
readOnly: true
volumeAttributes:
secretProviderClass: "nginx-deployment-aws-secrets"
containers:
- name: nginx-deployment
image: nginx
ports:
- containerPort: 80
volumeMounts:
- name: secrets-store-inline
mountPath: "/mnt/secrets-store"
readOnly: true
-
Click on Application -> Workloads.
-
Click on Create New Workload with the name "nginx-aws-sm".
-
Select "K8s YAML" for addon type.
-
Select "Upload files manually" for Artifact Sync.
-
Select the "nginx" namespace from the dropdown.
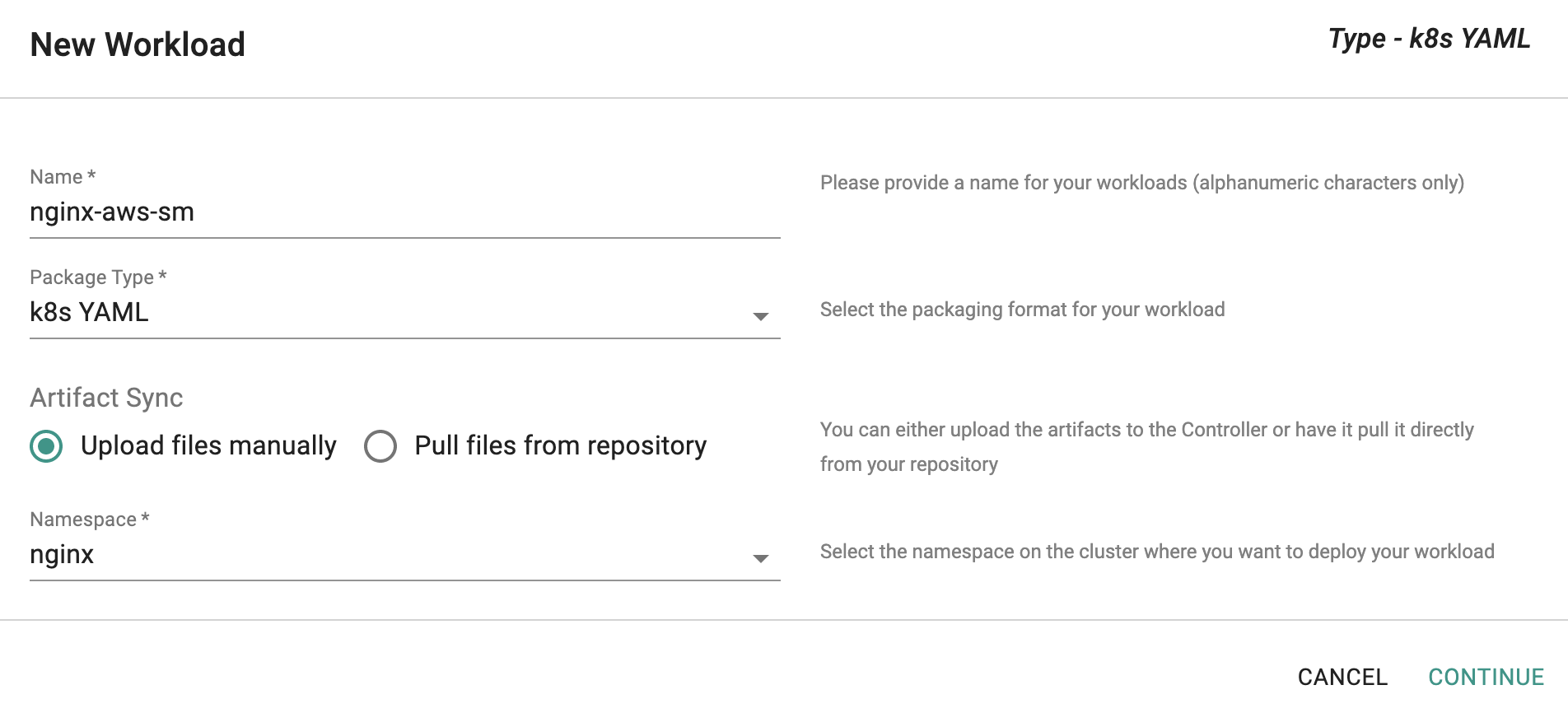
- Select the file downloaded in the previous step.
- Select a cluster for the placement policy
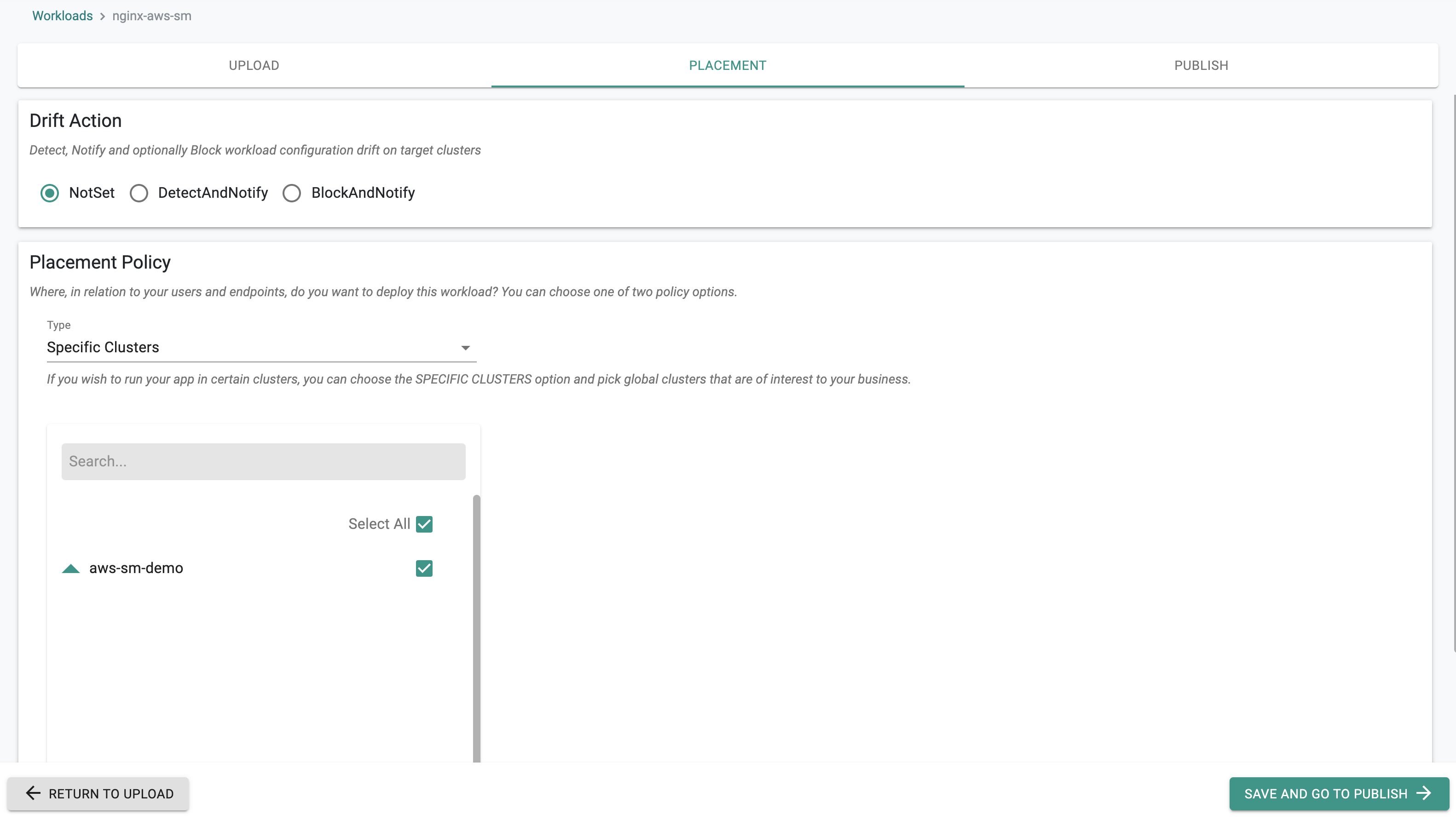
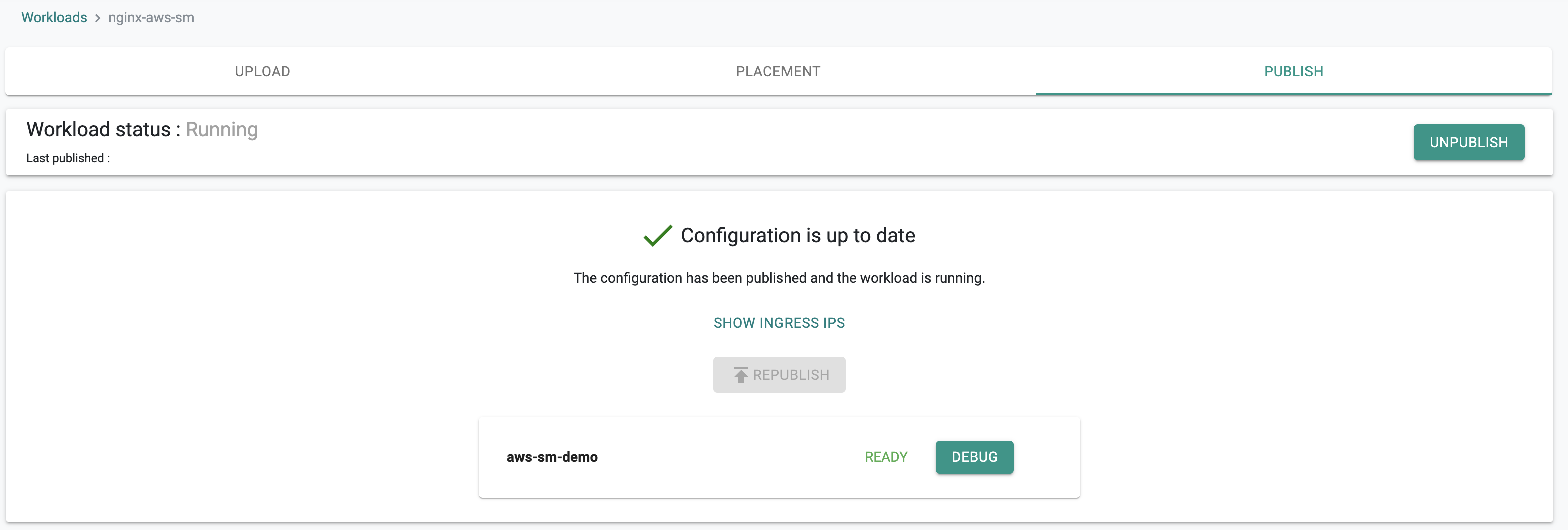
- Publish the workload
In a minute the workload should be deployed.
Step 3: Access the secrets¶
- Navigate to the resources tab for the cluster.
- Select "Workloads" as the Show Resources By and the workload as "nginx-aws-sm"
- Select Pods
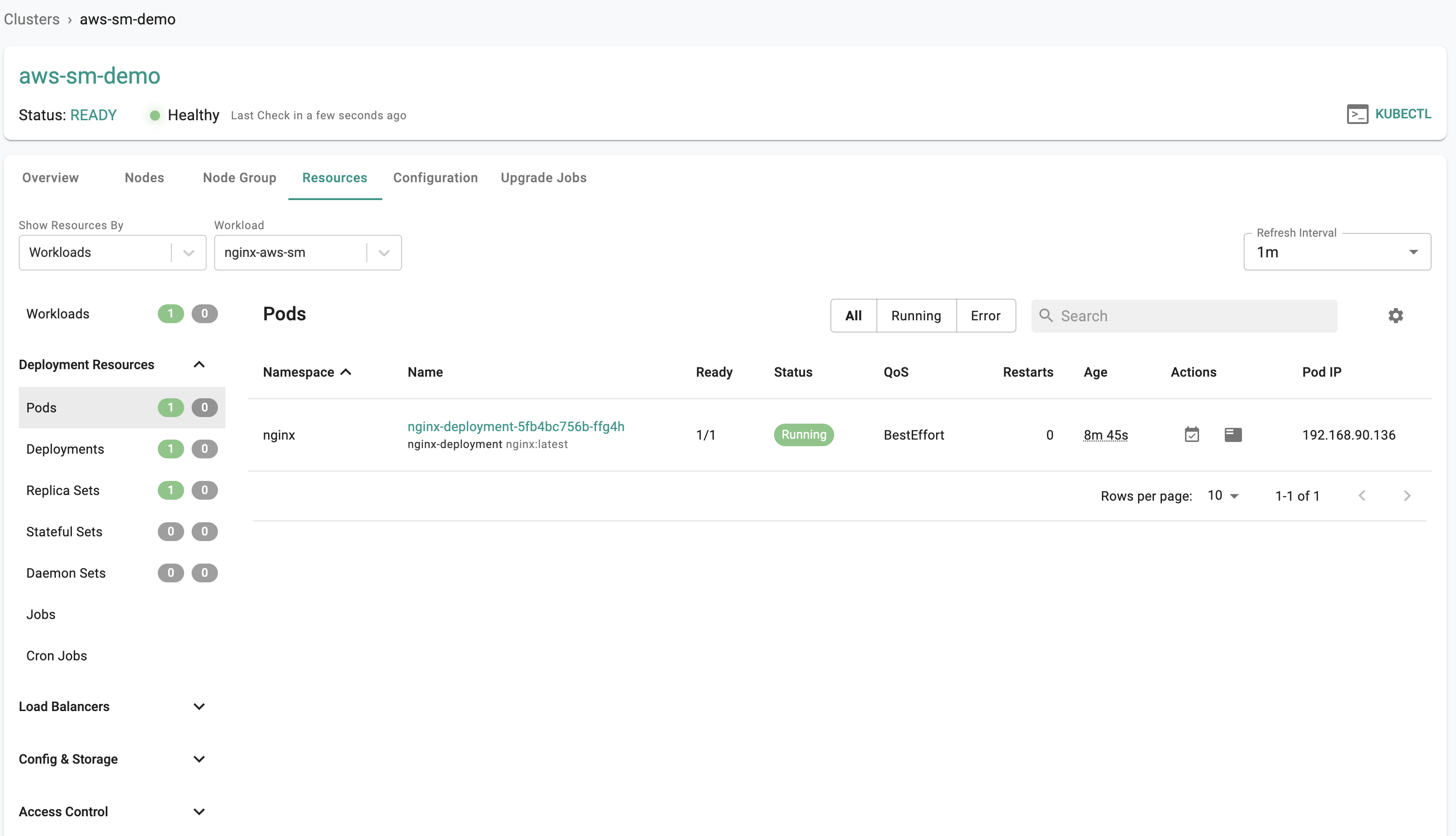
- Click on the "Shell & Logs" icon under the Actions tab.
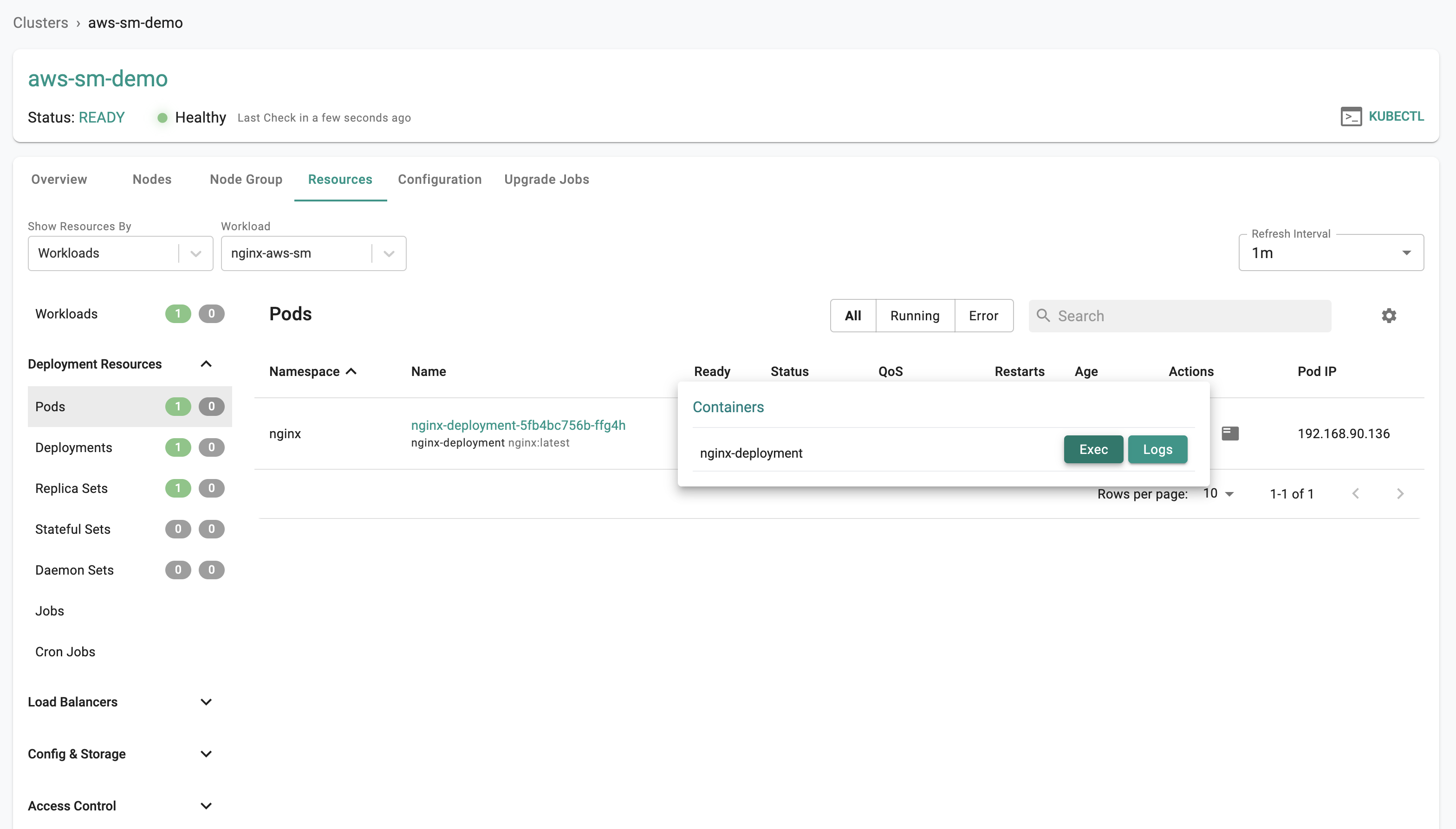
- Click on the "Exec" button.
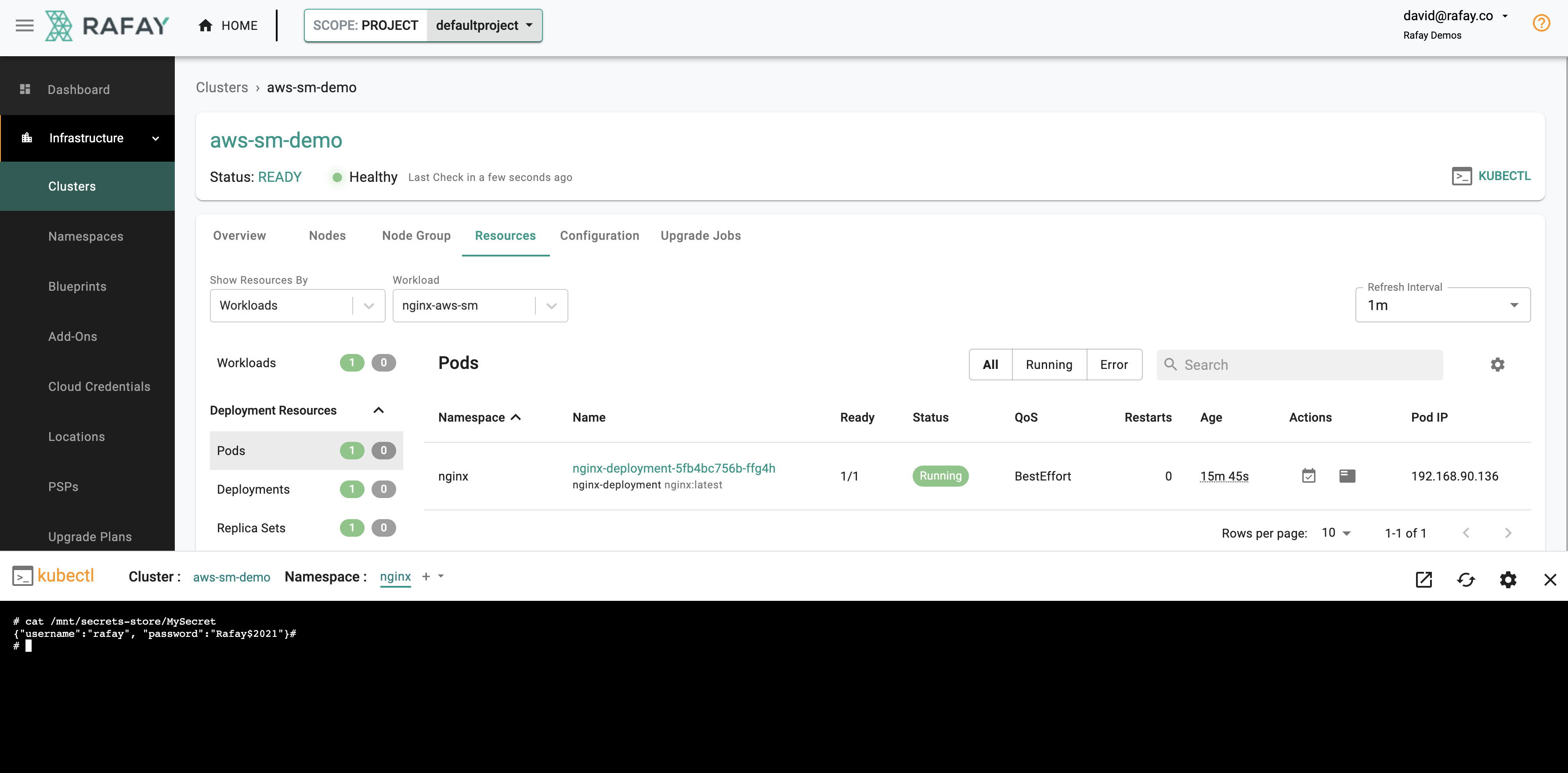
- Run the following command in the shell.
# cat /mnt/secrets-store/MySecret
The secret we configured in AWS Secrets Manager will be displayed and can be used in your applications.
{"username":"rafay", "password":"Rafay$2021"}
- For users that enabled and configured Secret Sync Click on the "KUBECTL" button for the cluster and run the following kubectl command. You should see a count of two for the secret.
kubectl get secrets -n nginx complete-secret
NAME TYPE DATA AGE
complete-secret Opaque 2 121m
- You can also grab the key/value pairs defined in the secret.
kubectl get secrets -n secrets-manager complete-secret -o yaml
apiVersion: v1
data:
password: UmFmYXkkMjAyMQ==
username: cmFmYXk=
kind: Secret
Important
K8s secrets are stored as Base64 encoded strings. You can use the base64 program to decode the strings.
echo UmFmYXkkMjAyMQ== | base64 --decode
Rafay
Congratulations! You can now pull and inject secrets from AWS Secrets Manager into your applications.
More information about Secret Store CSI driver and examples can be found here