Part 1: Provision
This is Part 1 of a multi-part, self-paced quick start exercise that will focus on provisioning an AKS cluster in Azure using the web console, RCTL CLI, or Terraform.
What Will You Do¶
In part 1, you will:
- Create a new Project in your Org
- Create a Cloud Credential
- Provision an Azure AKS cluster
- Verify cluster health
- Review available dashboards
Watch a video of this exercise.
Step 1: Create Project¶
In this step, we will create a new project which will serve as a logically isolated "operating environment" (sub tenant).
Note
Creating a project requires "Org Admin" privileges.
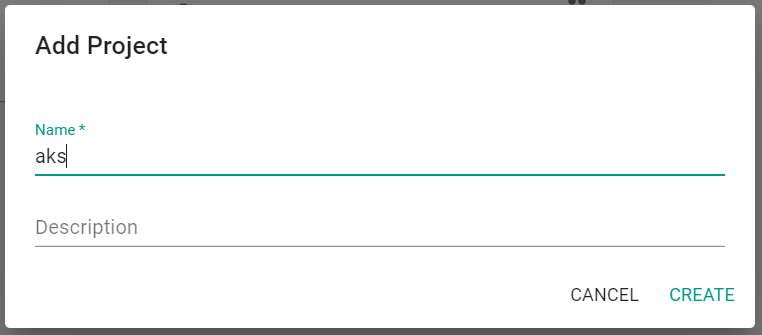
- Create a new project called "aks"
- Switch context to this project by clicking on the project in the web console
Step 2: Create Cloud Credential¶
Cloud credentials provide the controller with privileges to programmatically interact with your Azure account so that it can manage the lifecycle of infrastructure associated with AKS clusters.
- Follow the step-by-step instructions to setup Azure and obtain the required credentials.
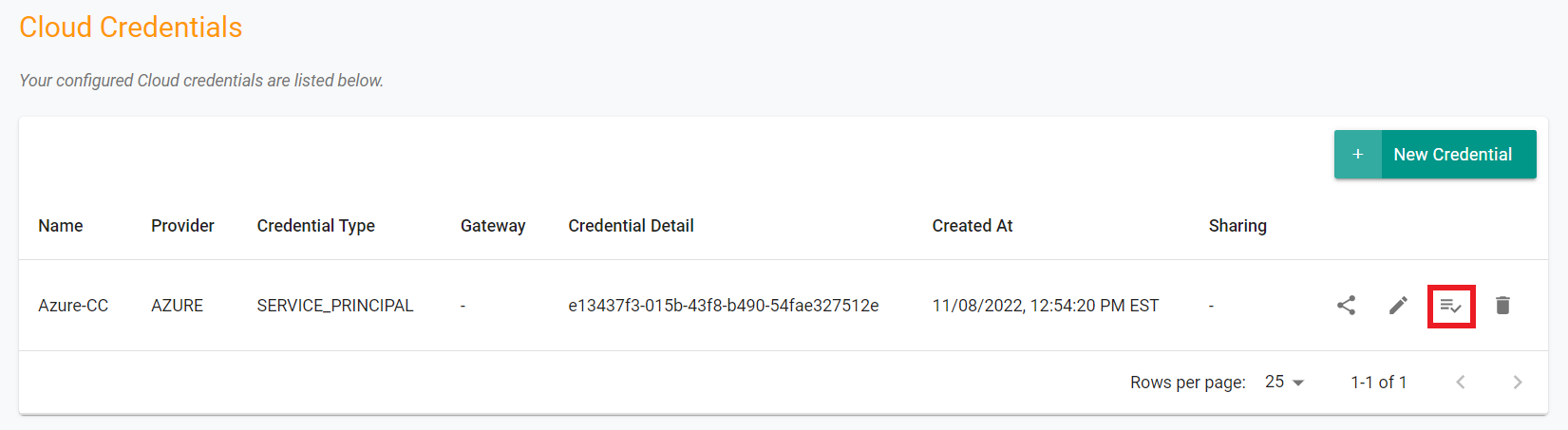
- Follow the step-by-step instructions to create an Azure cloud credential on the controller.
- Validate the newly created cloud credential to ensure it is configured correctly.
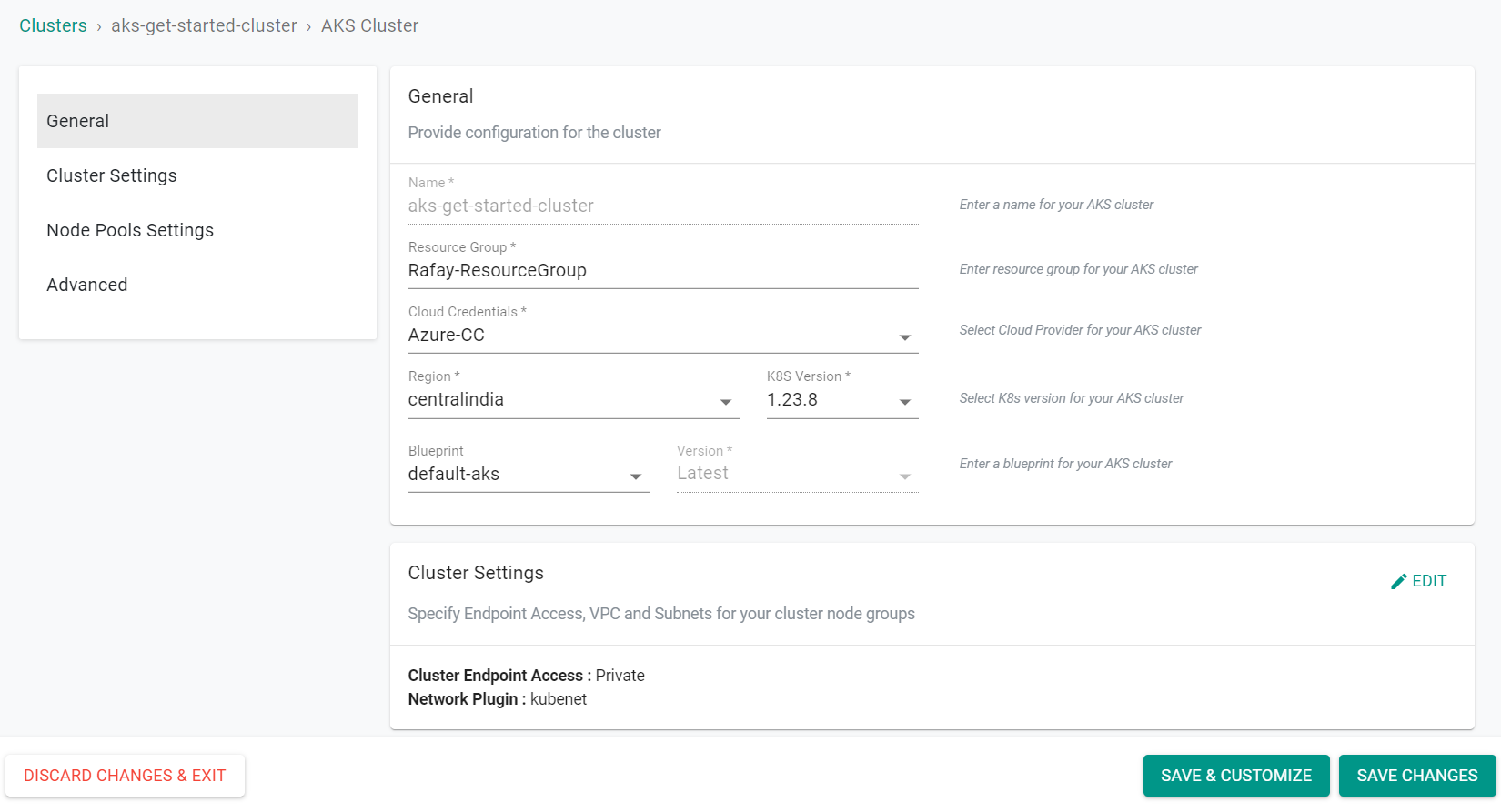
Step 3: Configure & Provision Cluster¶
In this step, you will configure and customize your Azure AKS Cluster using either the web console, the RCTL CLI with a YAML based cluster specification, or Terraform with some configuration files.
Select a method to provision and manage your AKS cluster from the tabs below.
- Navigate to the previously created project in your Org
- Select Infrastructure -> Clusters
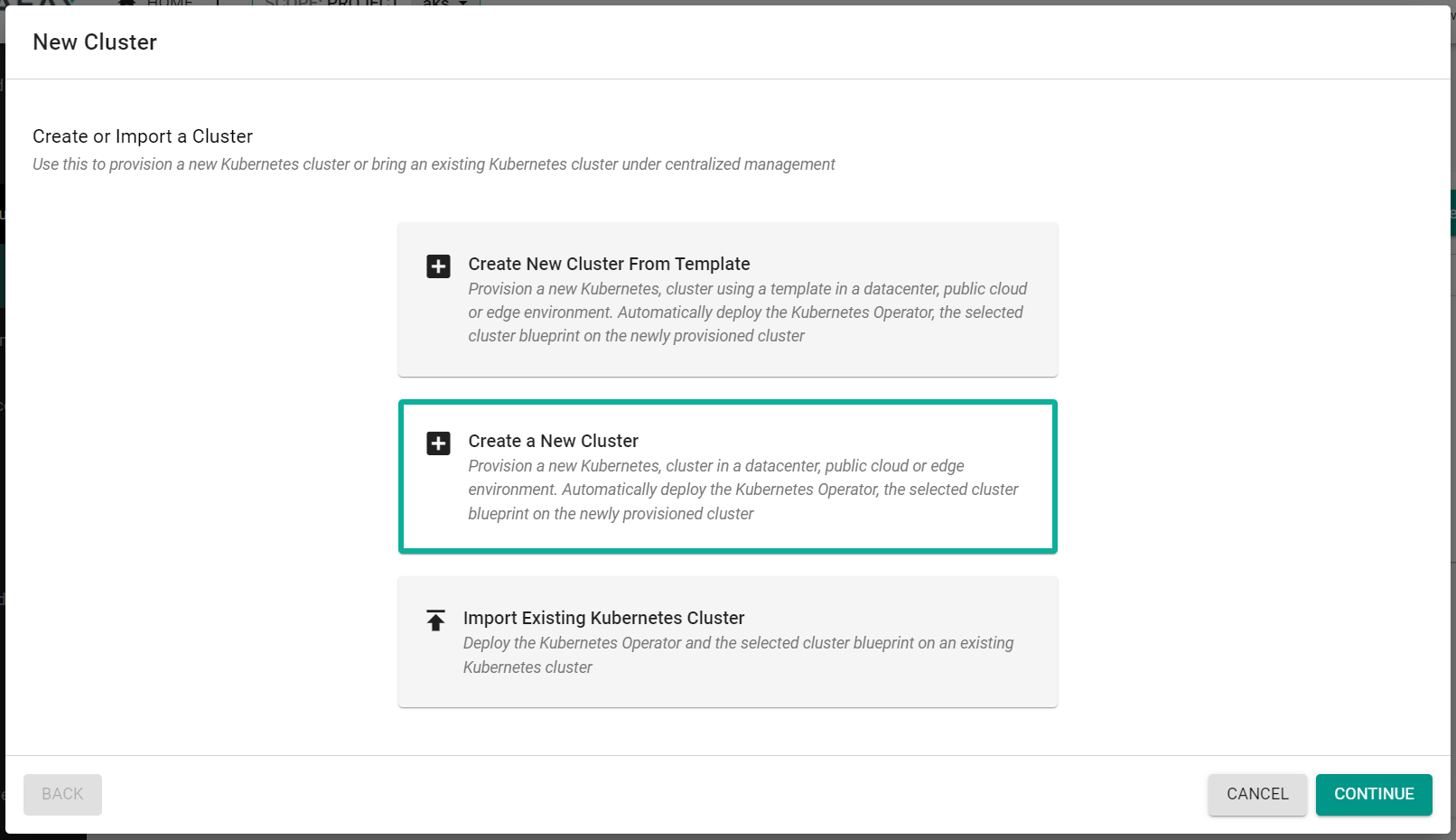
- Click "New Cluster"
- Select "Create a New Cluster"
- Click "Continue"
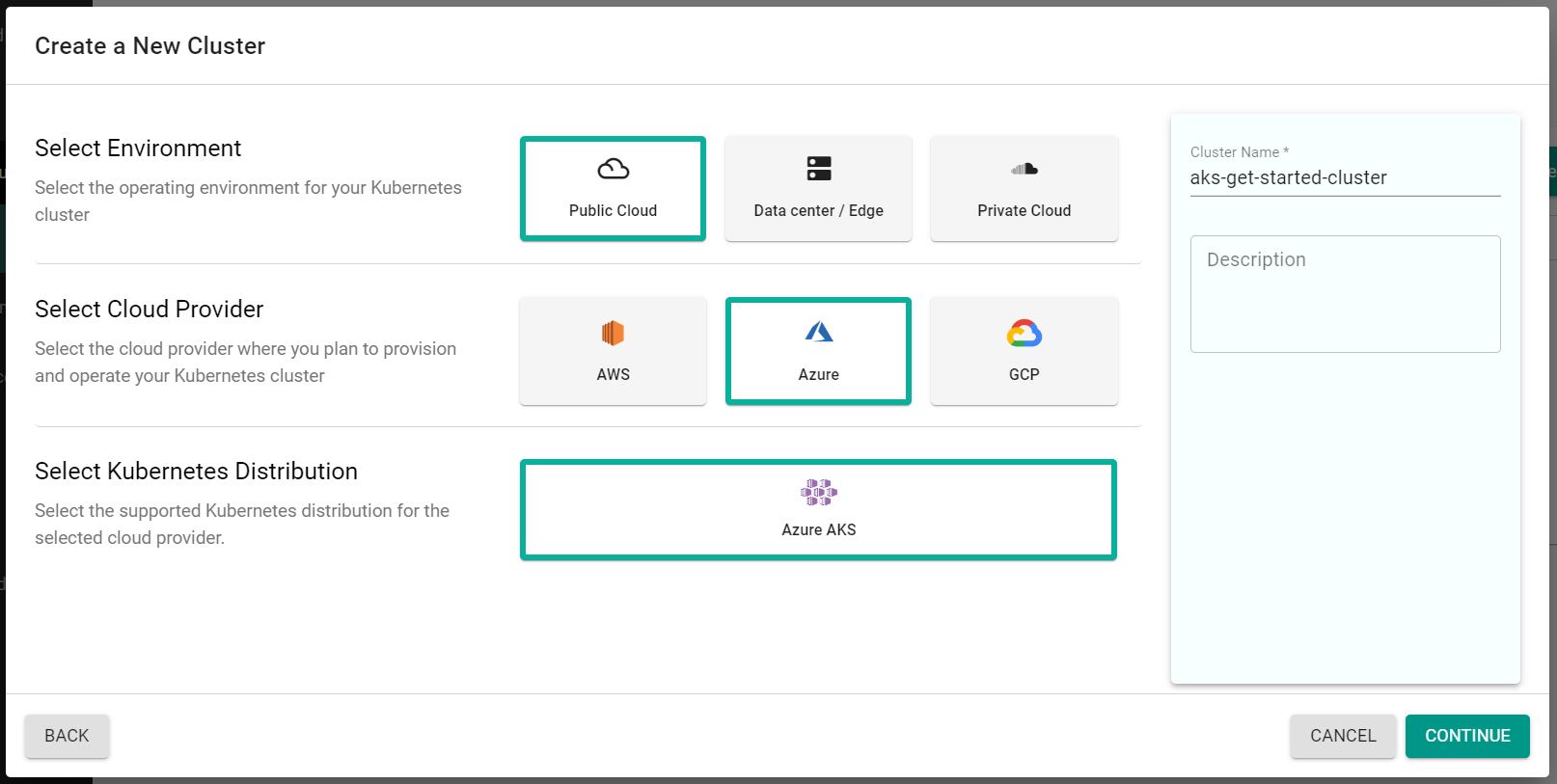
- Select "Public Cloud"
- Select "Azure"
- Select "Azure AKS"
- Enter a cluster name
- Click "Continue"
- Enter the "Resource Group" where the cluster will be created
- Select the previously created "Cloud Credentials"
- Select the Azure Region for the cluster
- Select the K8S Version for the cluster
- Select the "default-aks" blueprint
- Click "Save Changes"
- Click "Provision"
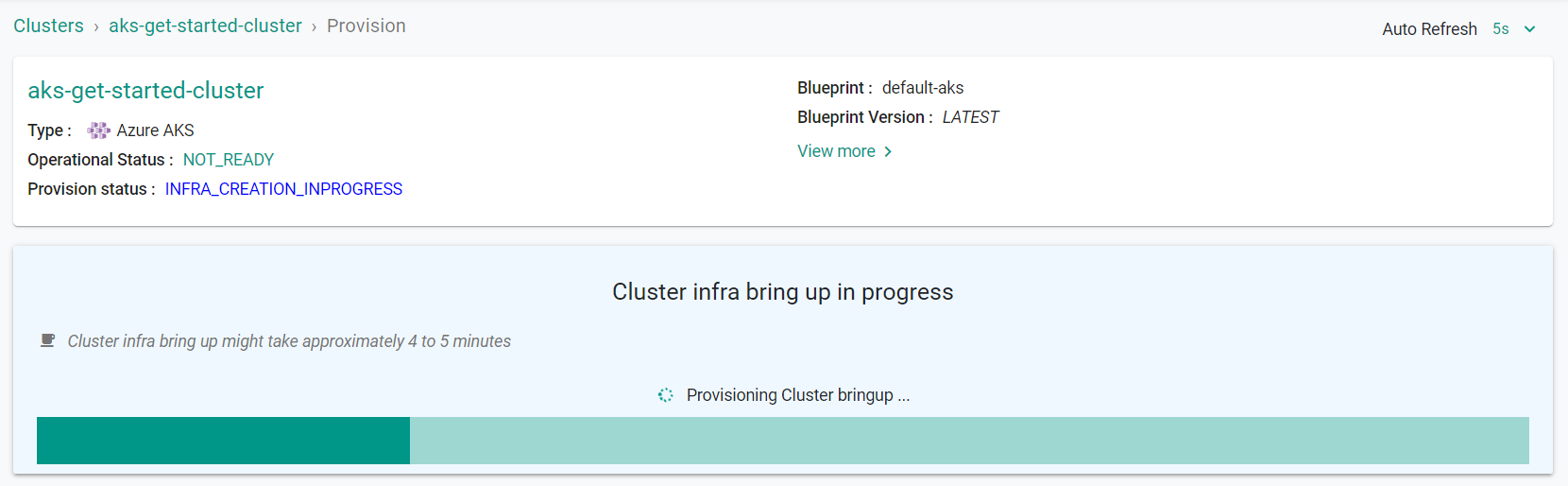
Provisioning will take approximately 10 minutes to complete. The final step in the process is the blueprint sync for the default blueprint. This can take a few minutes to complete because this requires the download of several container images and deployment of monitoring and log aggregation components.
- Save the below specification file to your computer as "aks-cluster-basic.yaml". Note, the highlighted sections in the spec will need to be updated to match your environment.
apiVersion: infra.k8smgmt.io/v3
kind: Cluster
metadata:
# The name of the cluster
name: aks-get-started-cluster
# The name of the project the cluster will be created in
project: defaultproject
spec:
blueprintConfig:
# The name of the blueprint the cluster will use
name: default-aks
# The name of the cloud credential that will be used to create the cluster
cloudCredentials: azure-cc
config:
kind: aksClusterConfig
metadata:
# The name of the cluster
name: aks-get-started-cluster
spec:
managedCluster:
apiVersion: "2022-07-01"
identity:
# The identity type the AKS cluster will use to access Azure resources
type: SystemAssigned
# The Azure geo-location where the resources will reside
location: centralindia
properties:
apiServerAccessProfile:
# Make network traffic between the API server and node pools on a private network
enablePrivateCluster: true
# DNS name prefix of the Kubernetes API server FQDN
dnsPrefix: aks-get-started-cluster-dns
# The Kubernetes version that will be installed on the cluster
kubernetesVersion: 1.29.4
networkProfile:
loadBalancerSku: standard
# Network plugin used for building the Kubernetes network. Valid values are azure, kubenet, none
networkPlugin: kubenet
sku:
# The name of a managed cluster SKU
name: Basic
# If not specified, the default is Free. See uptime SLA for more details. Valid values are Paid, Free
tier: Free
type: Microsoft.ContainerService/managedClusters
nodePools:
- apiVersion: "2022-07-01"
# The Azure geo-location where the node pools will reside
location: centralindia
# The name of the node pool
name: primary
properties:
# The desired number of nodes that can run in the node pool
count: 1
# Whether to enable auto-scaler
enableAutoScaling: true
# The maximum number of nodes that can run in the node pool
maxCount: 1
# The maximum number of pods that can run on a node
maxPods: 40
# The minimum number of nodes that can run in the node pool
minCount: 1
mode: System
# The kubernetes version that will run on the node pool
orchestratorVersion: 1.29.4
# The operating system type that the nodes in the node pool will run
osType: Linux
# Valid values are VirtualMachineScaleSets, AvailabilitySet
type: VirtualMachineScaleSets
# The size of the VMs that the nodes will run on
vmSize: Standard_DS2_v2
type: Microsoft.ContainerService/managedClusters/agentPools
# The resource group where the cluster will be created
resourceGroupName: Resource-Group
proxyConfig: {}
type: aks
Update the following sections of the specification file with details to match your environment
-
Update the name and project sections with the name of the cluster and the name of the project in your organization
metadata: name: aks-get-started-cluster project: defaultproject -
Update the cloudprovider section with the name of the cloud credential that was previously created
cloudprovider: azure-cc -
Update the name section with the name of the cluster to be created
metadata: name: aks-get-started-cluster
Managed Identity¶
- Update the identity type to use either a System-assigned or User-assigned managed identity
Below is the configuration needed for a System-assigned managed identity in which Azure automatically creates an identity for the AKS cluster and assigns it to the underlying Azure resources.
type: SystemAssigned
Below is a sample configuration needed for a User-assigned managed identity. The user identity will need to be updated to match an identity in your environment. With user-assigned managed identities, you have the flexibility to create and manage identities independently from the AKS cluster. These identities can then be associated with one or more AKS clusters, enabling seamless identity reuse across multiple AKS clusters or other Azure resources.
type: UserAssigned
userAssignedIdentities: /subscriptions/a2252eb2-7a25-432b-a5ec-e18eba6f26b1/resourceGroups/demo/providers/Microsoft.ManagedIdentity/userAssignedIdentities/demo-mgi-cli: {}
-
Update the location sections with the Azure region where the cluster will be created
location: centralindia -
Update the dnsprefix section with the DNS name prefix to use with the hosted Kubernetes API server FQDN
dnsPrefix: aks-get-started-cluster-dns -
Update the resourceGroupName section with the name of the Azure Resource Group where the resources will be created
resourceGroupName: Resource-Group - Save the updates that were made to the file
- Execute the following command to provision the cluster from the specification file previously saved
Expected output (with a task id):
./rctl apply -f aks-cluster-basic.yaml
{
"taskset_id": "w2l0q62",
"operations": [
{
"operation": "ClusterCreation",
"resource_name": "aks-get-started-cluster",
"status": "PROVISION_TASK_STATUS_PENDING"
},
{
"operation": "NodegroupCreation",
"resource_name": "primary",
"status": "PROVISION_TASK_STATUS_INPROGRESS"
},
{
"operation": "BlueprintSync",
"resource_name": "aks-get-started-cluster",
"status": "PROVISION_TASK_STATUS_INPROGRESS"
}
],
"comments": "The status of the operations can be fetched using taskset_id",
"status": "PROVISION_TASKSET_STATUS_PENDING"
}
To retrieve the status of the apply operation, enter the below command with the generated task id
./rctl status apply w2l0q62
Expected Output
{
"taskset_id": "w2l0q62",
"operations": [
{
"operation": "ClusterCreation",
"resource_name": "aks-get-started-cluster",
"status": "PROVISION_TASK_STATUS_INPROGRESS"
},
{
"operation": "NodegroupCreation",
"resource_name": "primary",
"status": "PROVISION_TASK_STATUS_PENDING"
},
{
"operation": "BlueprintSync",
"resource_name": "aks-get-started-cluster",
"status": "PROVISION_TASK_STATUS_PENDING"
}
],
"comments": "Configuration is being applied to the cluster",
"status": "PROVISION_TASKSET_STATUS_INPROGRESS"
}
- Login to the web console and view the cluster being provisioned
Provisioning will take approximately 10 minutes to complete. The final step in the process is the blueprint sync for the default blueprint. This can take a few minutes to complete because this requires the download of several container images and deployment of monitoring and log aggregation components.
Once the cluster finishes provisioning, download the cluster configuration file and compare it to the specification file used to create the cluster. The two files will match.
- Go to Clusters -> Infrastructure.
- Click on the Settings Icon for the newly created cluster and select "Download Cluster Config"
Make sure the following are installed or available.
- Terraform
- Text editor (or ability to update files using a terminal)
Make sure you have the following information. You may need to create these in your Azure environment or in the console.
- Azure Subscription ID
- Add a Contributor Role to the Subscription
- Azure Application ID and Azure Tenant ID
- The Application ID is also known as the Client ID.
- Azure Client Secret
- Azure Resource Group
- Console API Key and Secret
To provision a cluster using Terraform:
- Download and decompress the Get Started package. Navigate to the
/terraform/aksfolder. - Edit the
config.jsonfile. The file location is /terraform/artifacts/credentials/config.json. For this exercise, just change the following.api_key- Use the console API key.api_secret- Use the console API secret.project_id- Download the CLI Config file from the console and open the file with a text editor.
- Edit the
terraform.tfvarsfile. The file location is /terraform/terraform.tfvars. For this exercise, just update the following.subscription_idtenant_idclient_idclient_secretcluster_resource_groupcluster_location
- Open the terminal or command line.
- Navigate to the
terraformfolder. - Run
terraform init.- Initializes the directory containing the Terraform configuration files, preparing the directory for use with Terraform.
- Run
terraform validate.- Validates the configuration files in the directory, without accessing any remote services.
- Run
terraform apply. Enteryeswhen prompted. -Provisions the cluster.
It can take 20 minutes to provision the cluster. Check the console for the provisioning status.
Step 4: Verify Cluster¶
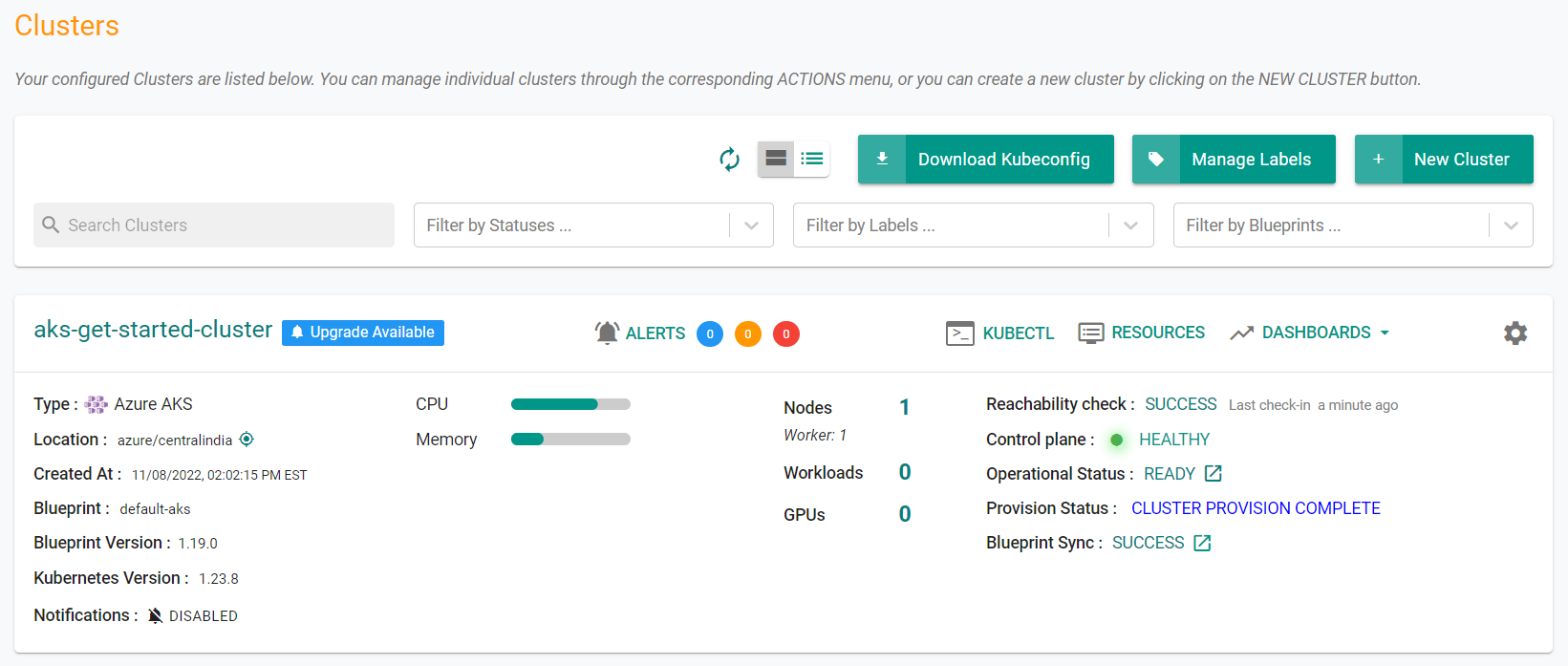
Once provisioning is complete, you should have a ready to use Azure AKS Cluster. We will verify the cluster by checking its health and status.
Step 4a: Cluster Status & Health¶
The Kubernetes management operator automatically deployed on the cluster by the controller will "maintain a heartbeat" with the controller and will "proactively monitor" the status of the components on the worker node required for communication with the control plane and the controller.
- Cluster reachability should be not more than 1 minute
- Control plane should report as Healthy
Step 4b : Zero Trust Kubectl¶
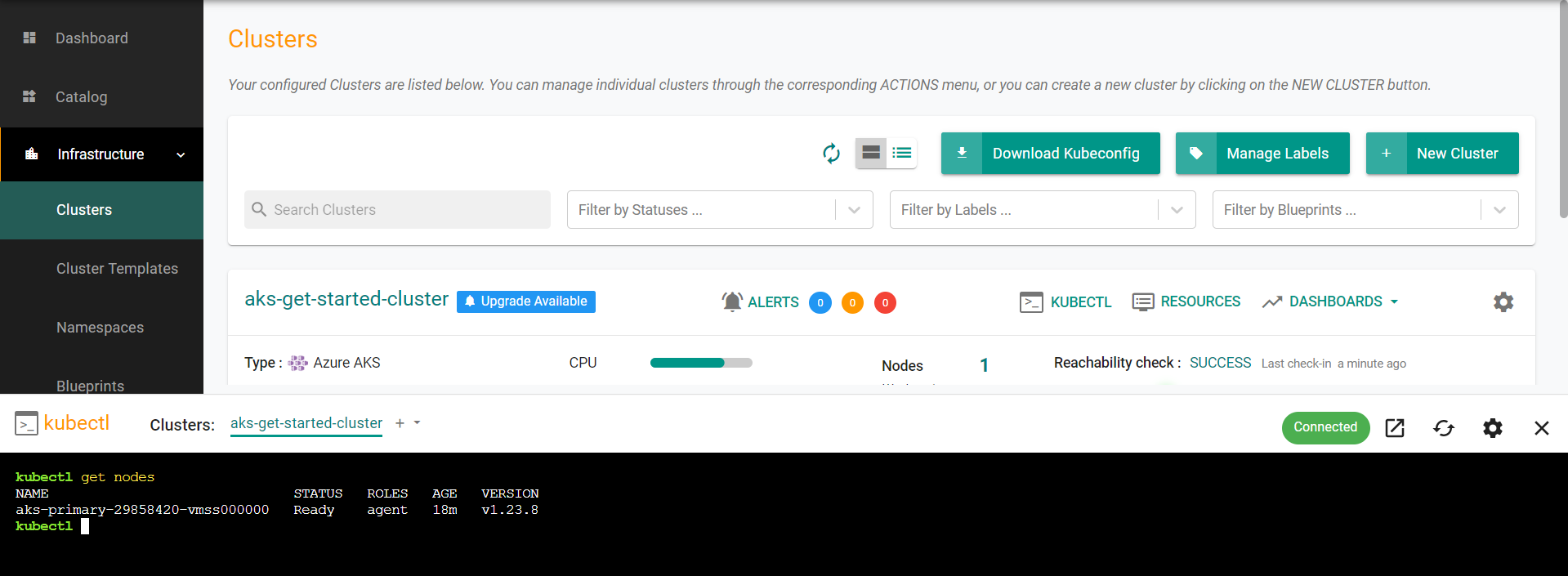
Your AKS Cluster's API Server is private and secure (i.e. cloaked and not directly reachable on the Internet). The controller provides a zero trust kubectl channel for authorized users.
- Click the "Kubectl" button on the cluster card.
- This will launch a web based kubectl shell for you to securely interact with the API server over a zero trust channel
Step 5: Dashboards¶
The default cluster blueprint automatically deploys Prometheus and other components required to monitor the AKS cluster. This data is aggregated from the cluster on the controller in a central, time series database. This data is then made available to administrators in the form of detailed dashboards.
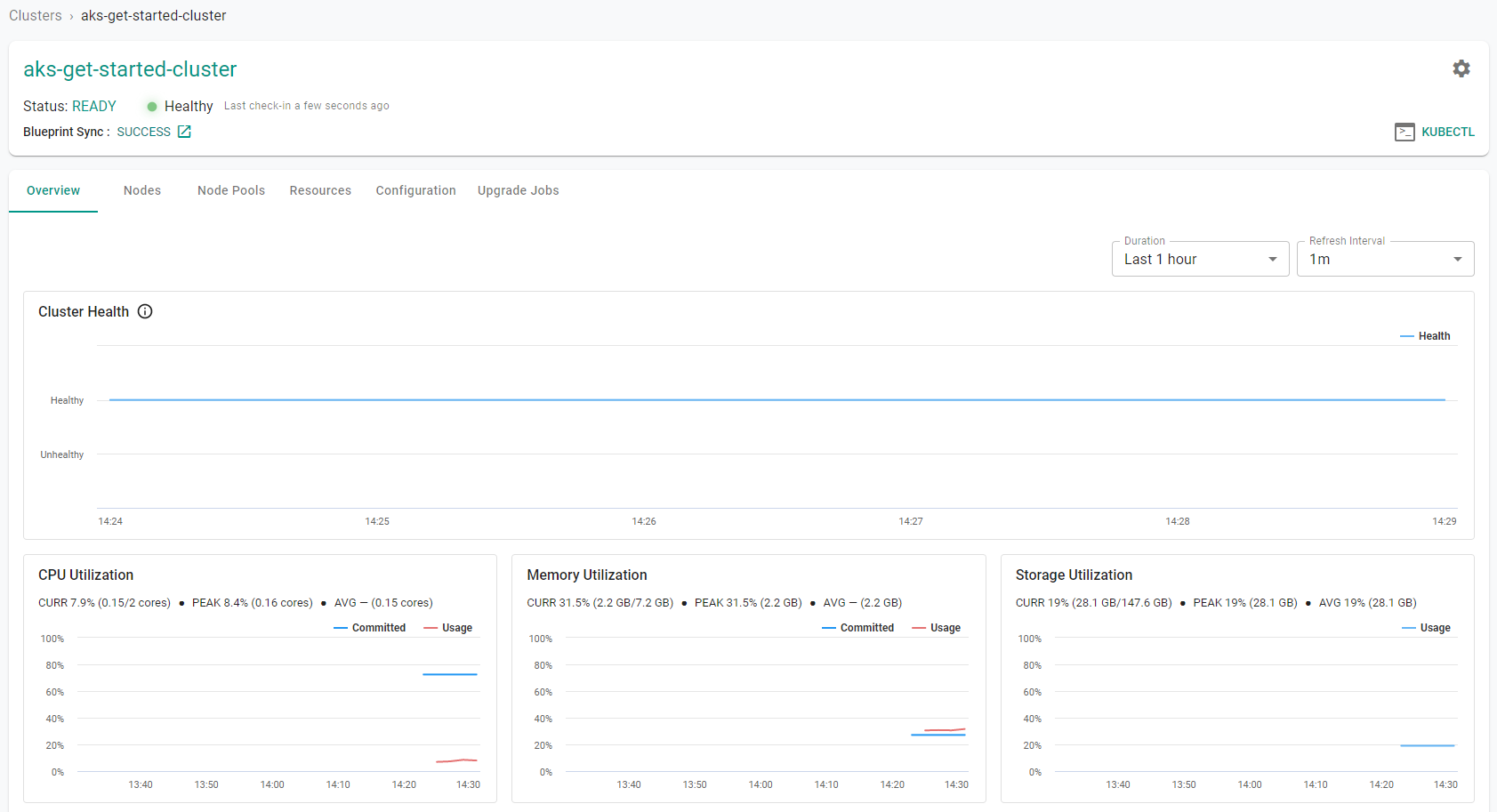
Step 5a: Cluster Dashboard¶
Click on the cluster name to view the cluster dashboard. You will be presented with time series data for the following
- Cluster Health
- CPU Utilization
- Memory Utilization
- Storage Utilization
- Number of Worker Nodes
- Number of workloads and their status
- Number of pods and their status
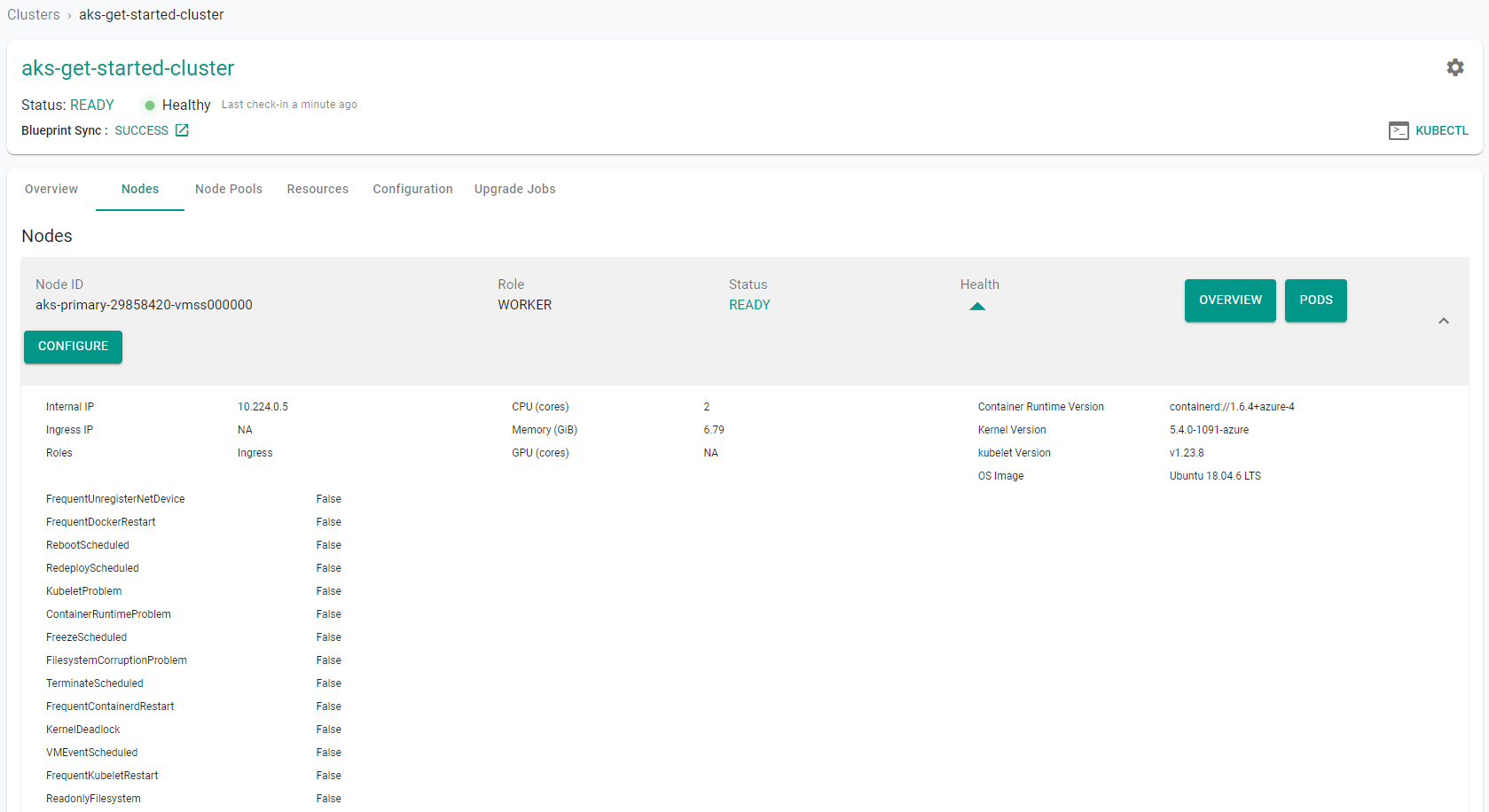
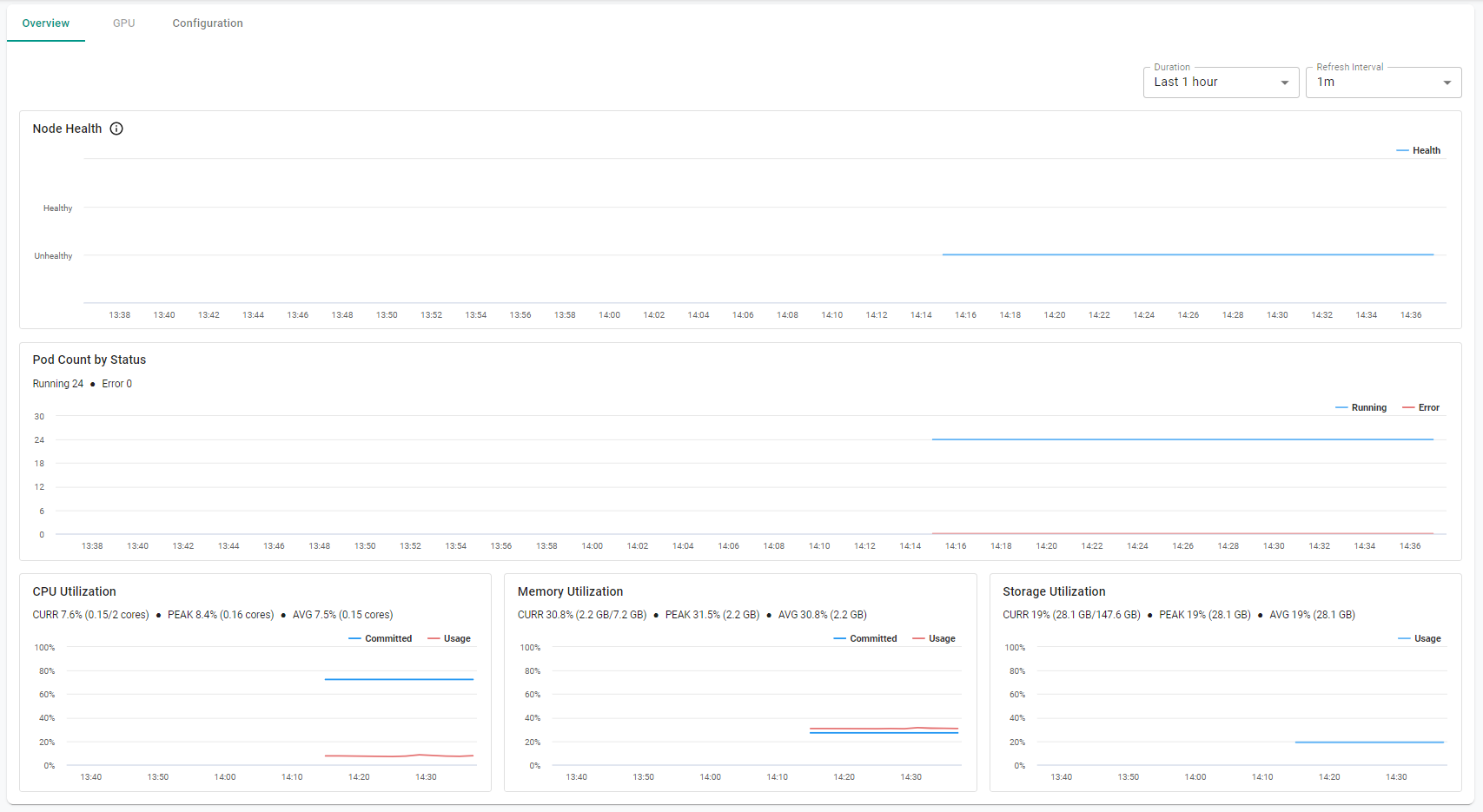
Step 5b: Node Dashboard¶
Click on the node to view the node dashboard.
Now, click on "Overview". You will be presented with time series data for the following metrics:
- Node Health
- CPU Utilization
- Memory Utilization
- Storage Utilization
Step 5c: Kubernetes Resources¶
The dashboard also comes with an integrated Kubernetes dashboard. Click on "Resources" and you will be presented with all the Kubernetes resources organized using a number of filters.
Recap¶
Congratulations! At this point, you have
- Successfully configured and provisioned an Azure AKS cluster
- Used zero trust kubectl to securely access the AKS cluster's API server
- Used the integrated cluster, node and k8s dashboards to monitor and view details about the cluster