Notifications
What Will You Do¶
In this section, you will use the previously created IDP user to test the permissions of the associated IDP group. The IDP group inherits its permissions by sharing the name with an existing group in the Rafay console. You will then create a a group with different permissions in the Rafay console. This group will then be assinged to the IDP user witin the Rafay console. The IDP user will then be associated with with two groups, one from the matching IDP group and the other from the locally assigned group. The IDP user will have a union of the two associated group's permission sets.
Step 1: Test IDP User¶
In this step, we will test the permissions of the IDP user associated with the IDP group.
- Navigate to the Rafay console
- Login with the previously created IDP user account
- Click Login With SSO
- Enter your IDP credentials
- Click Sign in
You will then be logged into the Rafay console with the IDP user.
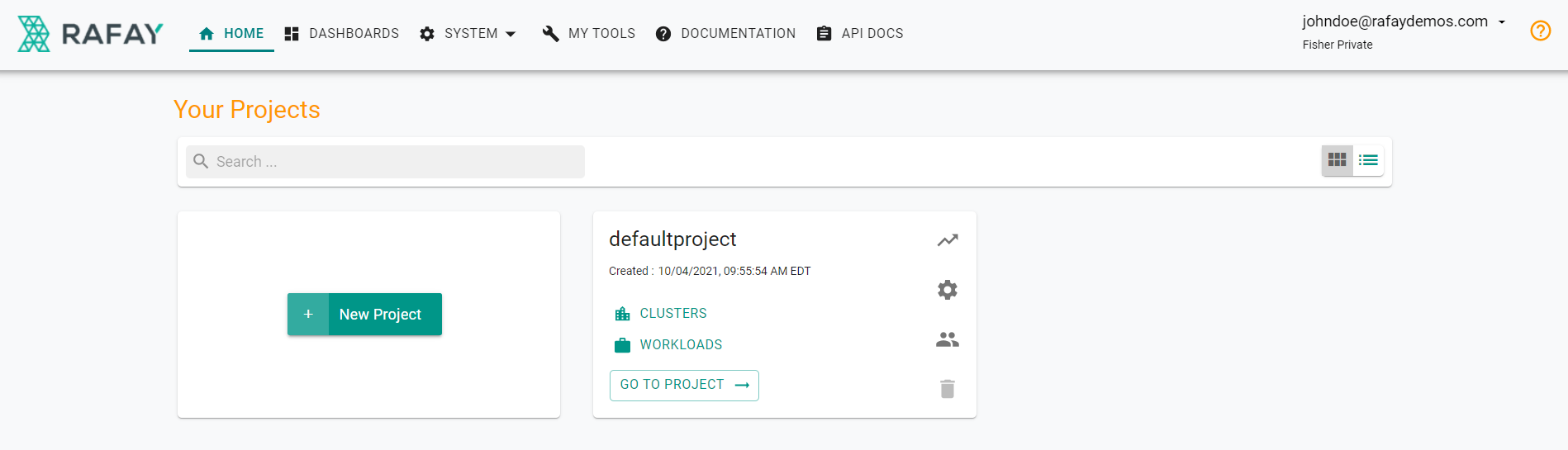
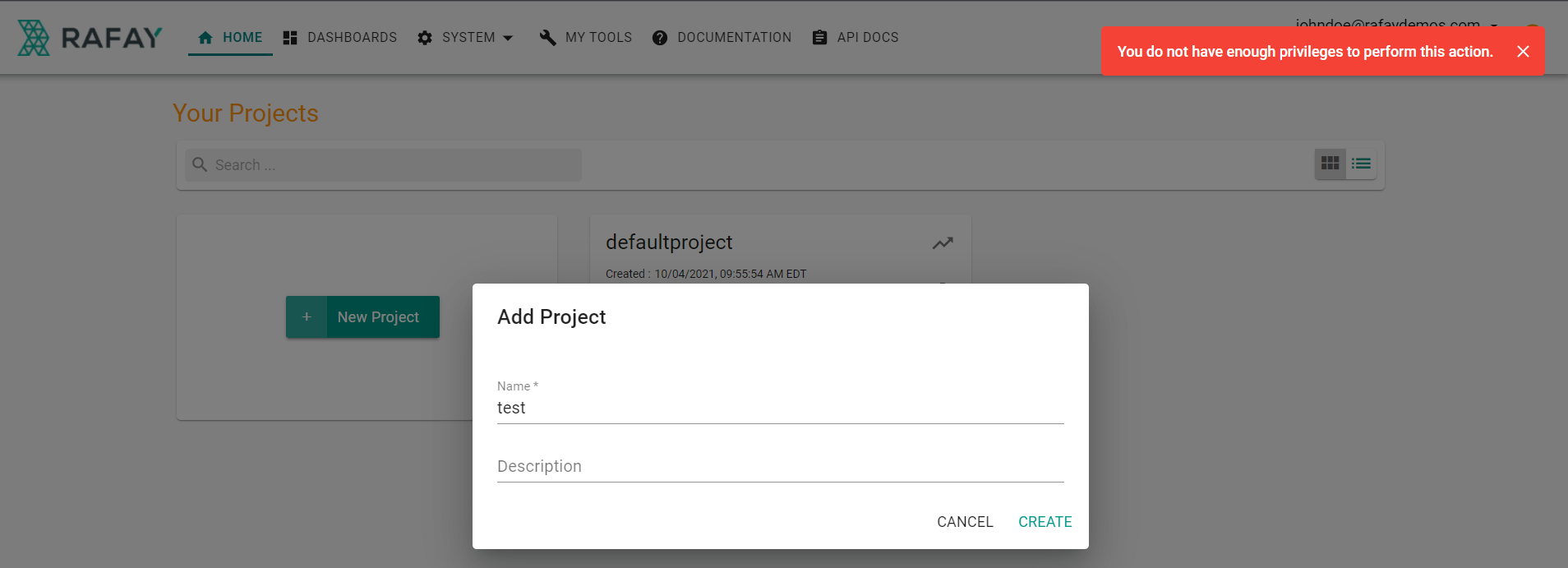
- Click on New Project
- Enter a name
- Click Create
You will see that you are unable to create a new project as you do not have the required permissions with the IDP user account. The user is associated with the "Organization Read Only" group which has read only permissions.
- Click on defaultproject
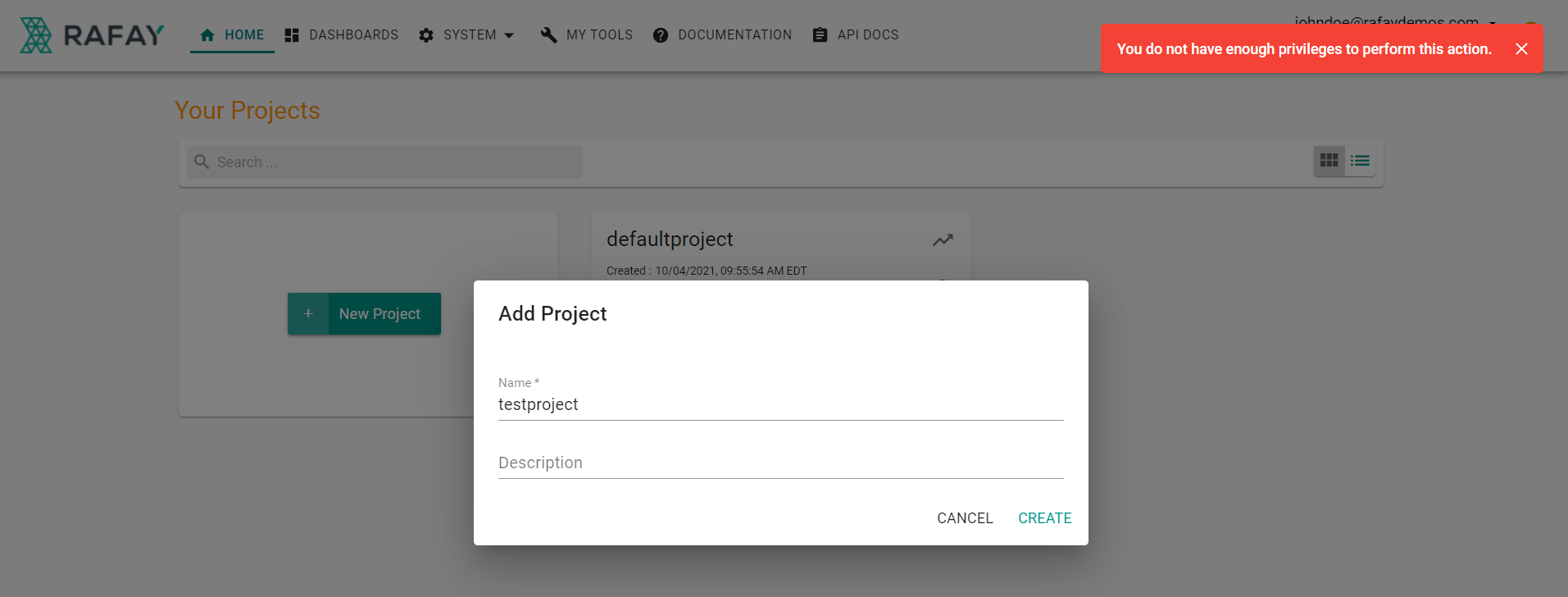
- Click Infrastructure -> Blueprints
- Click New Blueprint
- Enter a name for the blueprint
- Click Save
You will see that you are unable to create a blueprint with the IDP user account as it only has read only permissions.
Step 2: Create Local Group¶
In this step, we will create a local group in the Rafay console with infrastructure administrator privledges and add the IDP user to the group. Since the IDP user that was previously created only has read only permissions, we will need to use an account with Organization Administrator privledges.
- Navigate to the Rafay console
- Login with an Organization Administrator account
- Click on System -> Groups
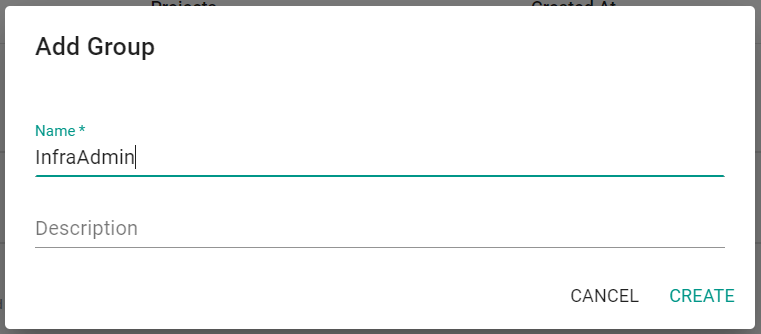
- Click New Group
- Enter the name InfraAdmin
- Click Create
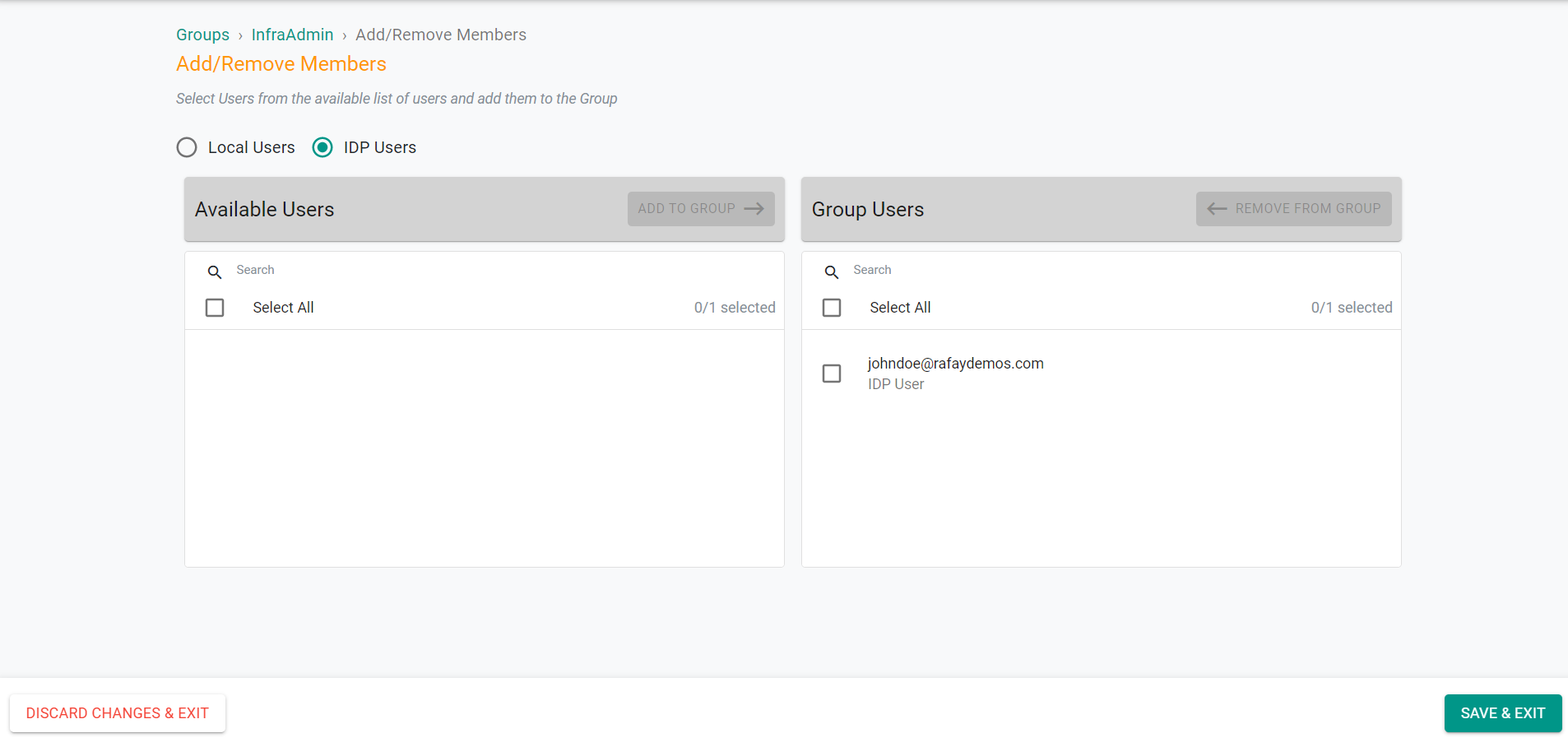
- On the Users tab, click Add/Remove Members
- Select IDP Users
- Select the previously created IDP user
- Click Add to Group
- Click Save & Exit
- Click Continue to confirm adding the user to the group
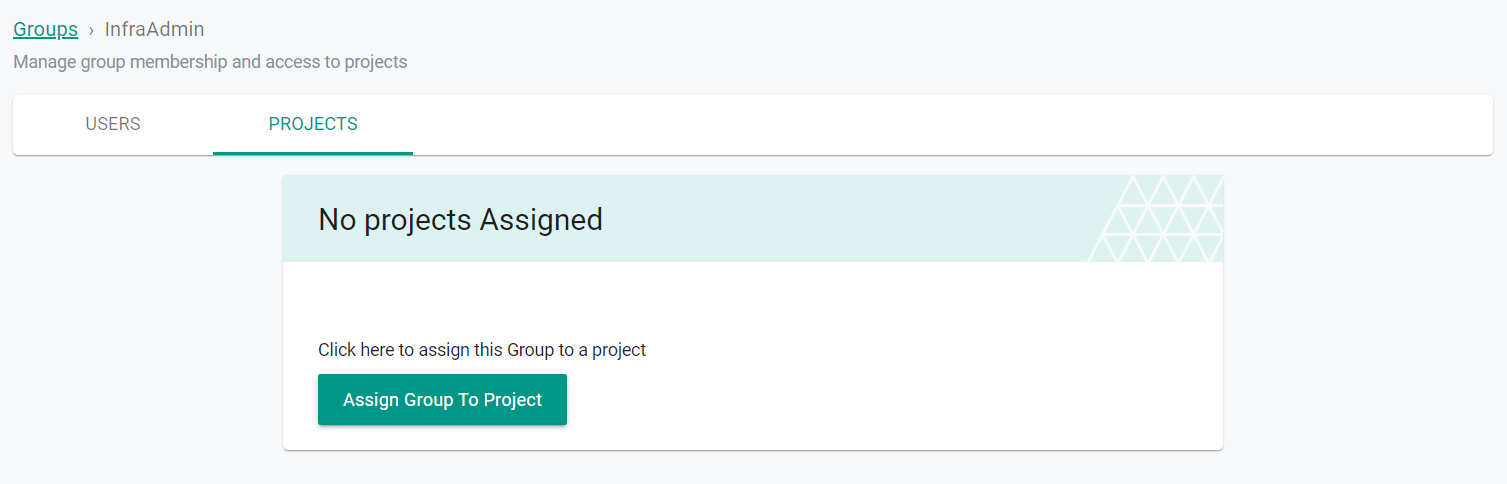
- Click on the Projects tab
- Click Assign Group To Project
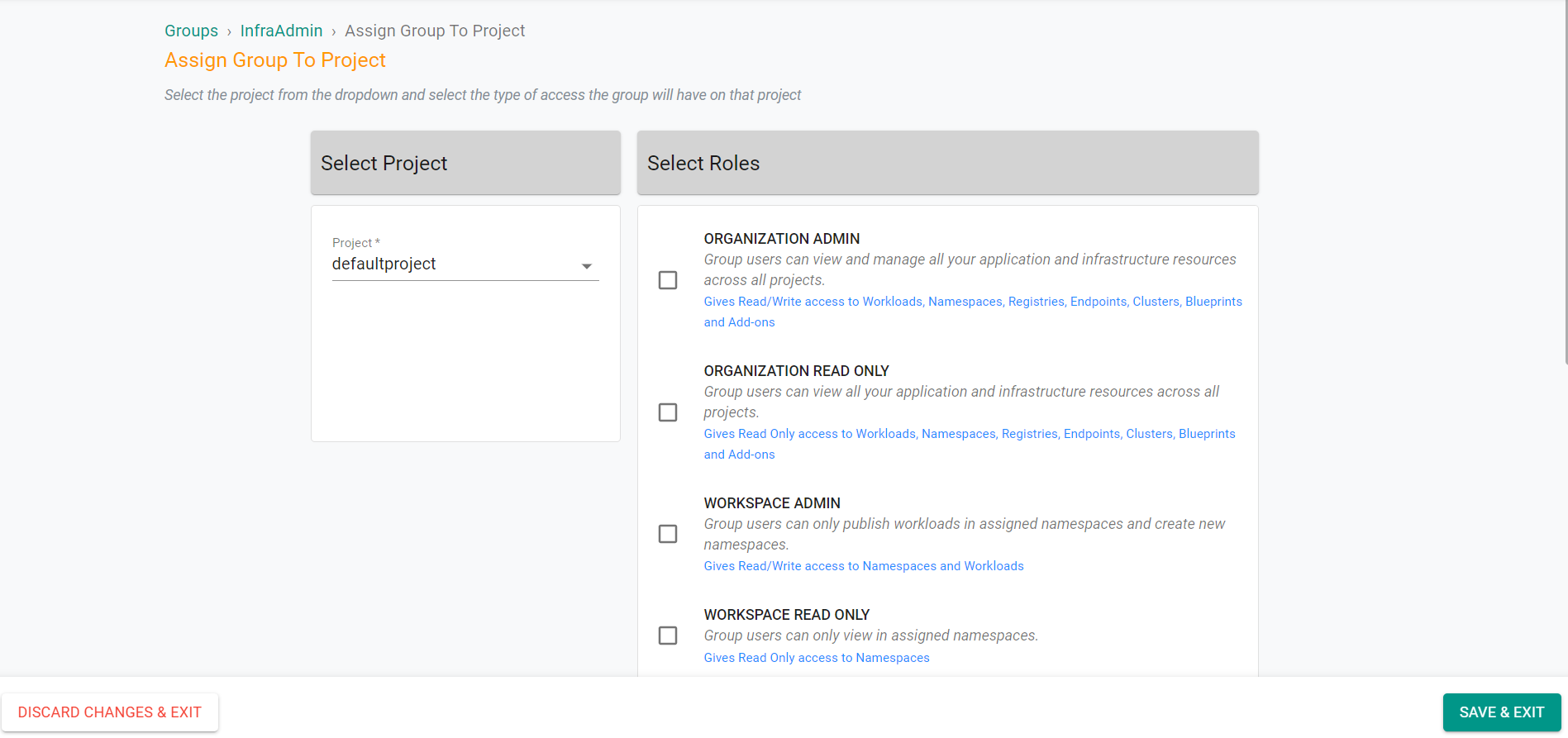
- Under Select Project, select defaultproject
- Under Select Roles, select Infrastructure Admin
- Click Save & Exit
Step 3: Check IDP User Groups¶
In this step, we will check the groups that are associated with the IDP user.
- Navigate to the Rafay console
- Login with an Organization Administrator account
- Click on System -> Users
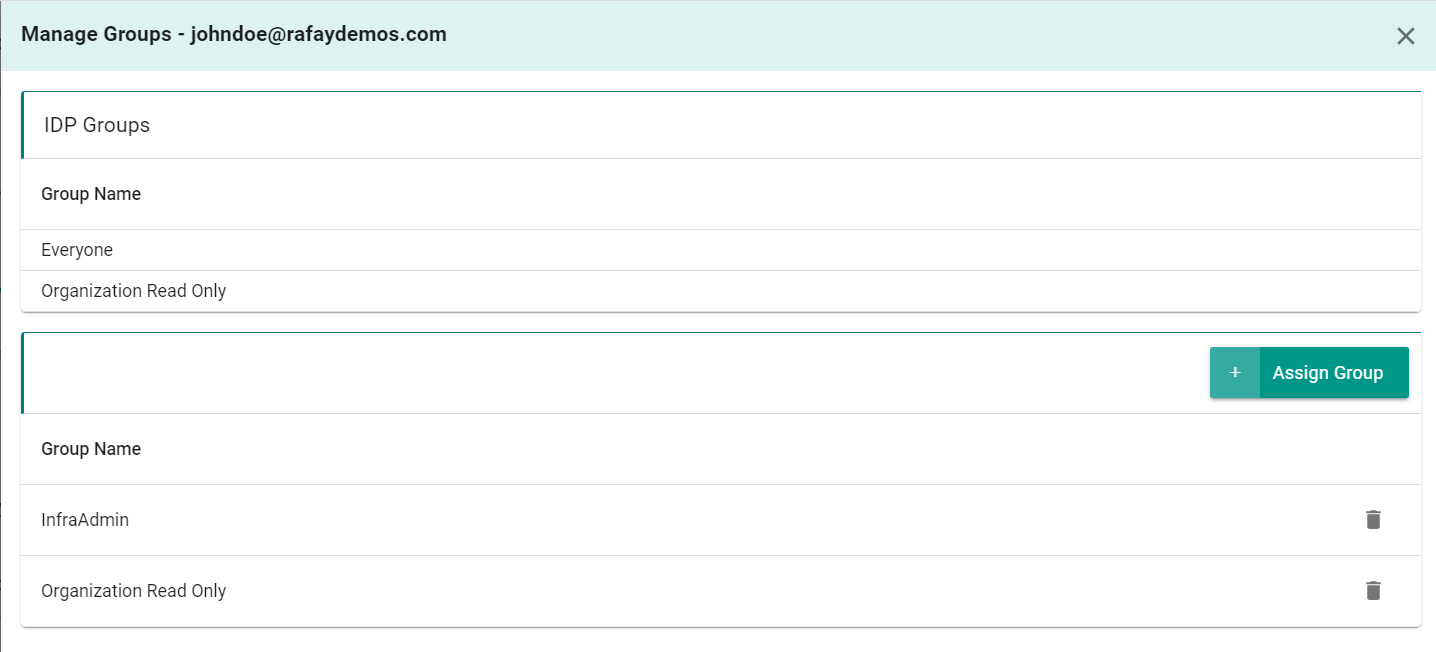
- Click on the Manage Groups icon next to the IDP user
At the top of the window, you will see the IDP groups associated to the user. On the lower portion of the window, you will see the local groups associated to the user. In this scenario, the Organization Read Only group was inherited through the IDP group association and the InfraAdmin group was assigned locally. We know the InfraAdmin group was assigned locally as it is not listed in the IDP Groups section at the top of the window.
Step 4: Test IDP User with Local Group¶
In this step, we will test the newly added permissions of the IDP user that is now associated with a local group that has Infrastructure Admin privledges on the defaultproject.
- Navigate to the Rafay console
- Login with the previously created IDP user account
- Click on New Project
- Enter a name
- Click Create
You will see that the user still does not have permissions for organizational level changes.
- Click on defaultproject
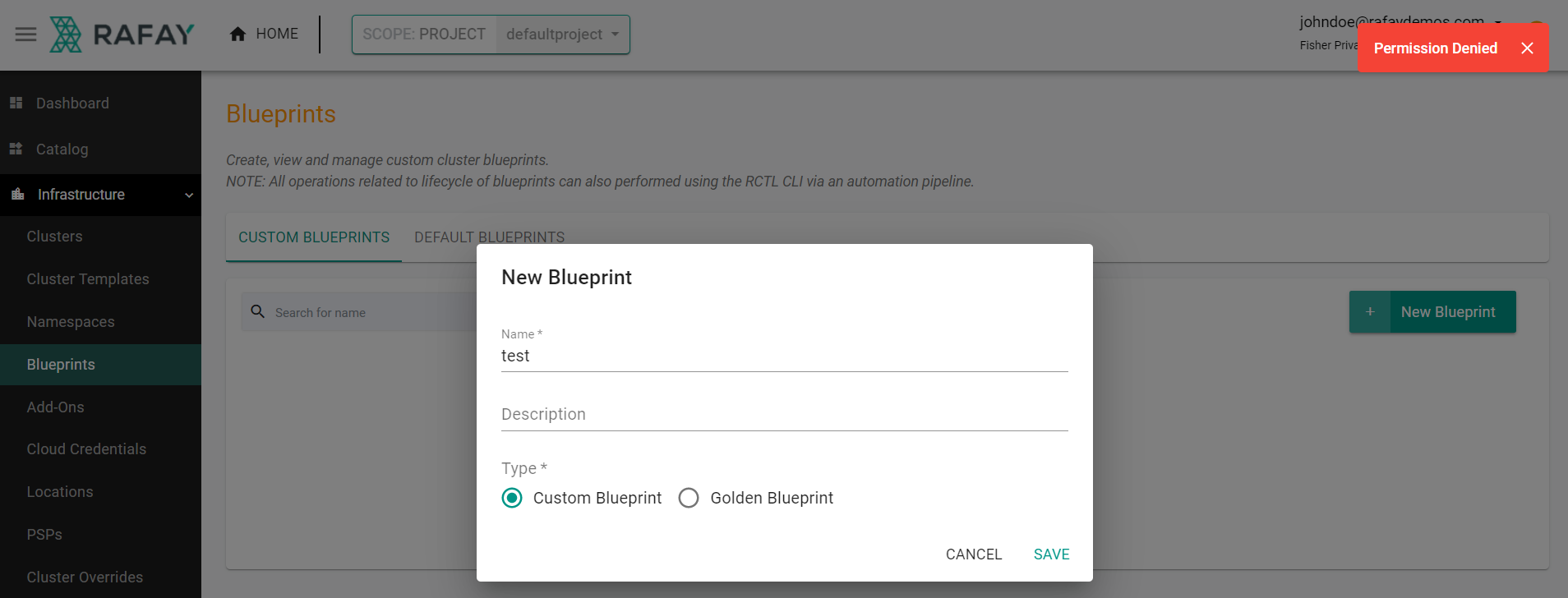
- Click Infrastructure -> Blueprints
- Click New Blueprint
- Enter a name for the blueprint
- Click Save
- Enter a version name
- Click Save Changes
You will see that you are now able to create a blueprint with the IDP user account as it now has Infrastructure Administrator permissions.
Recap¶
In this part, you tested both IDP and local group permissions assigned to an IDP user to see how the union of the groups permissions functioned.