Project based isolation
What Will You Do¶
In this part of the self-paced exercise, we will focus on the following use case:
Teams have dedicated clusters assigned to them. Platform teams want to manage these clusters centrally and ensure that teams only have access to their respective clusters.
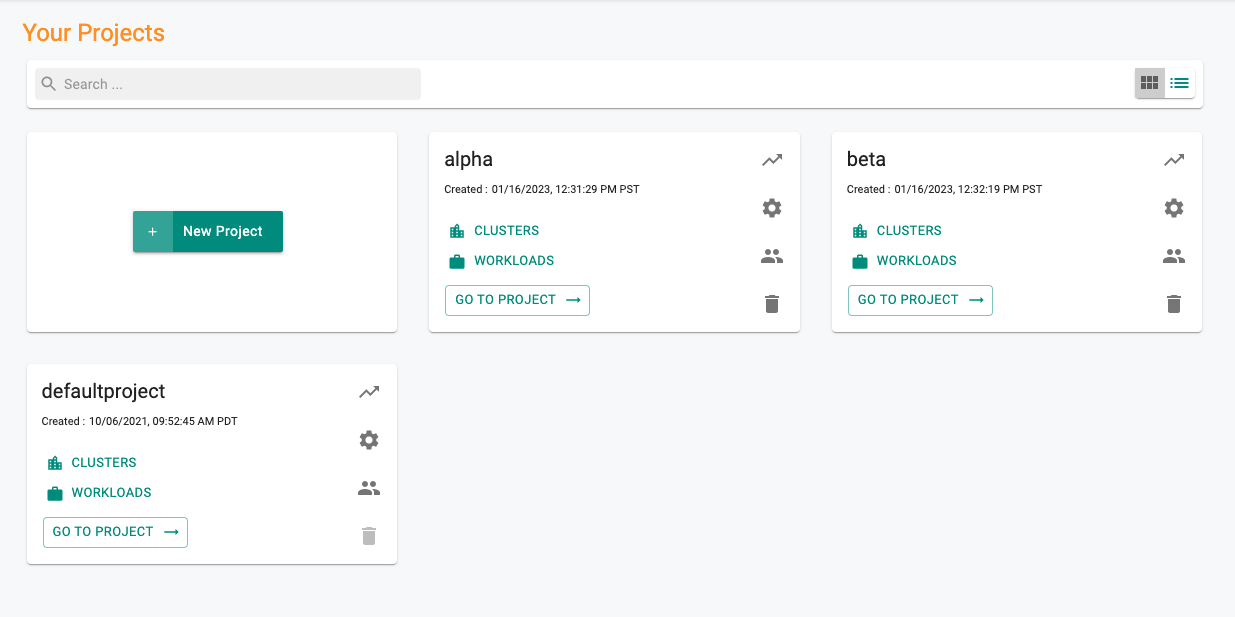
For this example, we will consider two teams, alpha and beta each having their dedicated clusters, alpha-cluster and beta-cluster respectively.
sequenceDiagram
Admin->> Controller: Step 1: Create projects for each business unit/application (e.g. alpha & beta)
Admin->> Controller: Step 2: Create cluster entries within respective projects and download bootstrap
Admin->> Clusters: Step 3: Apply bootstrap to the clusters to initiate the import process
Admin->> Controller: Step 4: Verify that the clusters are imported to the right projects and are healthy
Admin->> Controller: Step 5: Create "project specific roles" for users in alpha/beta teams and verify accessDeclarative specifications are also provided for this exercise.
Step 1: Create projects for alpha and beta teams¶
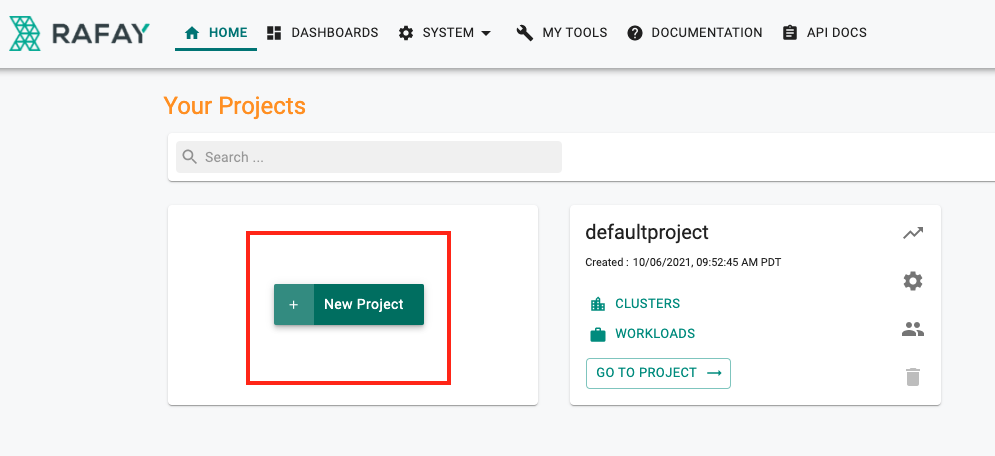
- Login into your Org as an Org Admin
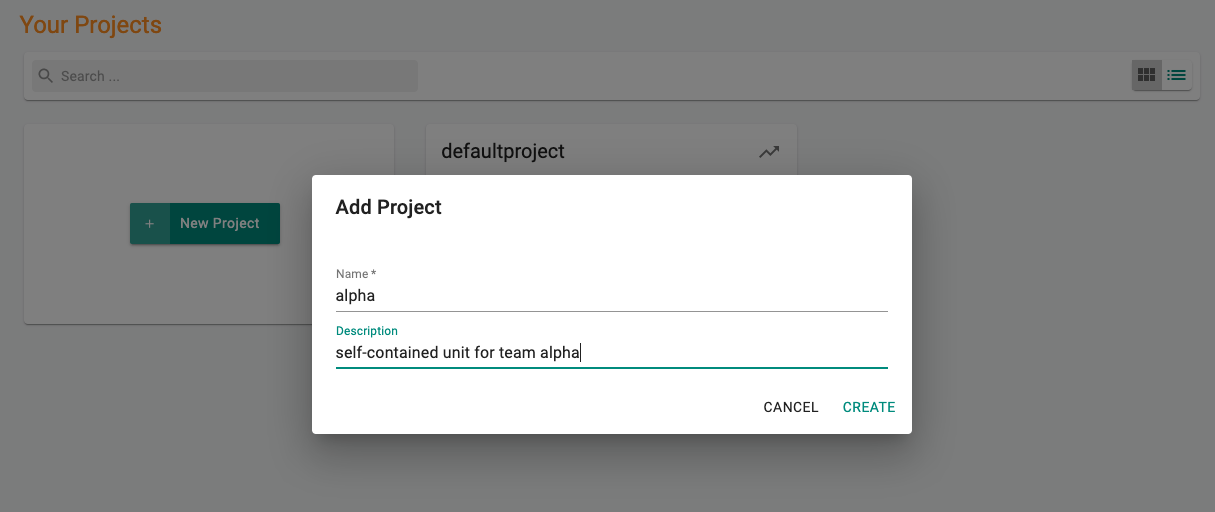
- Click on New Project
- Provide the name for the project (e.g. alpha) and a suitable description
- Click Create
- Repeat the same exercise and create another project for team beta
Step 2: Create cluster entries, download bootstrap¶
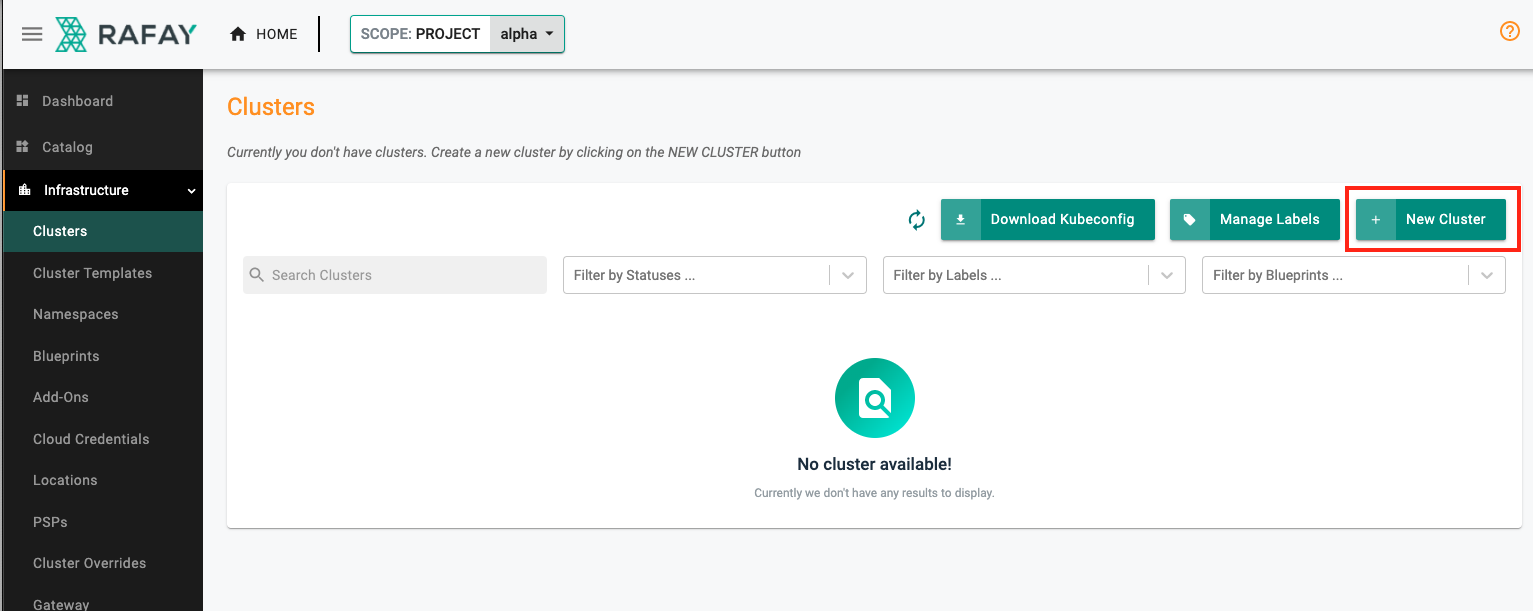
- Navigate to project alpha
- Click on New Cluster
- Select Import Existing Kubernetes Cluster
- Click Continue
- Select Environment and Kubernetes Distribution as appropriate
- Provide a cluster name (e.g. alpha-cluster) and description as needed
- Click Continue
- For this example, we will keep the Blueprint selection as minimal, click Continue
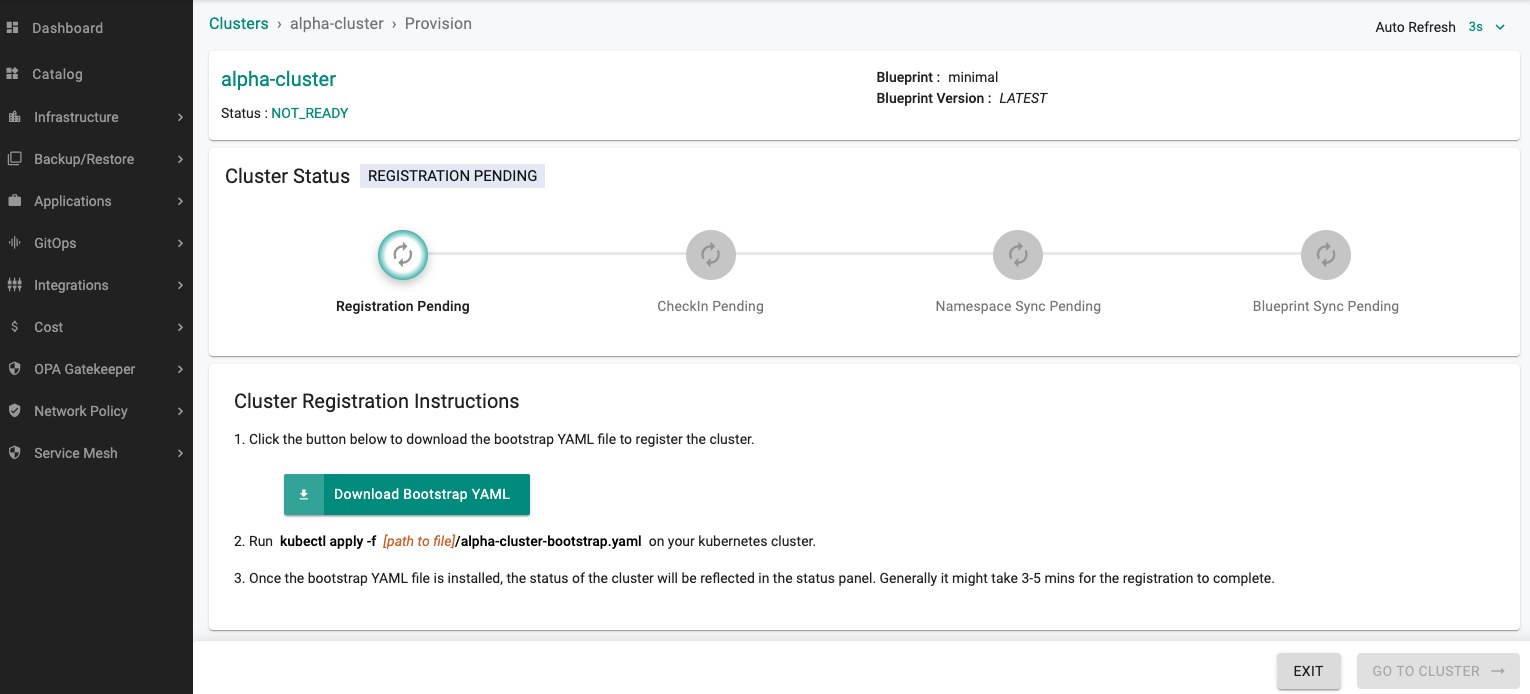
- Download the cryptographically unique bootstrap YAML required to register the cluster
Step 3: Apply bootstrap to initiate the import process¶
Use kubectl to apply the "cluster bootstrap" file on your K8s cluster.
kubectl apply -f [path to file]/alpha-cluster-bootstrap.yaml
This will create a namespace for the k8s mgmt operator, download the container images, and register with the controller. This one time import process can take ~2 minutes.
namespace/rafay-system created
serviceaccount/system-sa created
clusterrole.rbac.authorization.k8s.io/rafay:manager created
clusterrolebinding.rbac.authorization.k8s.io/rafay:rafay-system:manager-rolebinding created
clusterrole.rbac.authorization.k8s.io/rafay:proxy-role created
clusterrolebinding.rbac.authorization.k8s.io/rafay:rafay-system:proxy-rolebinding created
priorityclass.scheduling.k8s.io/rafay-cluster-critical created
role.rbac.authorization.k8s.io/rafay:leader-election-role created
rolebinding.rbac.authorization.k8s.io/rafay:leader-election-rolebinding created
customresourcedefinition.apiextensions.k8s.io/namespaces.cluster.rafay.dev created
customresourcedefinition.apiextensions.k8s.io/tasklets.cluster.rafay.dev created
customresourcedefinition.apiextensions.k8s.io/tasks.cluster.rafay.dev created
service/controller-manager-metrics-service-v3 created
deployment.apps/controller-manager-v3 created
configmap/connector-config-v3 created
configmap/proxy-config-v3 created
deployment.apps/rafay-connector-v3 created
service/rafay-drift-v3 created
validatingwebhookconfiguration.admissionregistration.k8s.io/rafay-drift-validate-v3 created
Repeat Steps (3) and (4) with Project "beta" and cluster "beta-cluster".
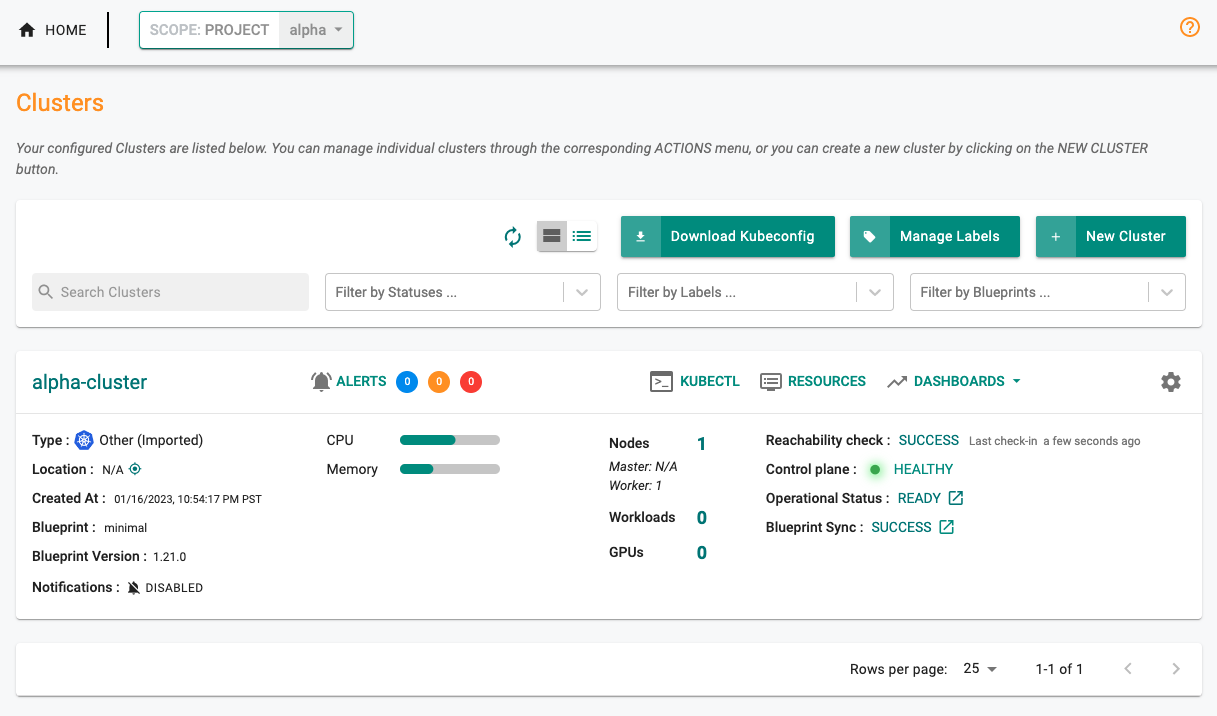
Step 4: Verify that the clusters are imported to the right projects¶
On the console, you will notice that the imported cluster would have registered itself and will start receiving instructions from the controller. You can also check the status of the mgmt operator pods on your cluster using kubectl.
kubectl get po -n rafay-system
You should something like
NAME READY STATUS RESTARTS AGE
controller-manager-v3-66dfbd5db4-v97vw 1/1 Running 0 68s
edge-client-84499dfdd4-qn67q 1/1 Running 0 71s
rafay-connector-v3-7fb99b5cd9-clh2g 1/1 Running 0 68s
relay-agent-556c86f7bc-chxk8 1/1 Running 0 2m49s
Once the k8s operator is operational, it will "establish and maintain a heartbeat" with the controller.
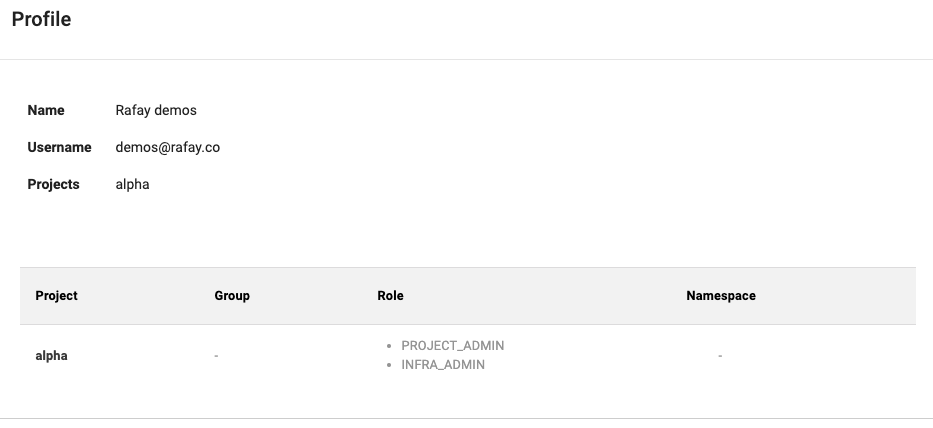
Step 5: Create "project specific roles" for users¶
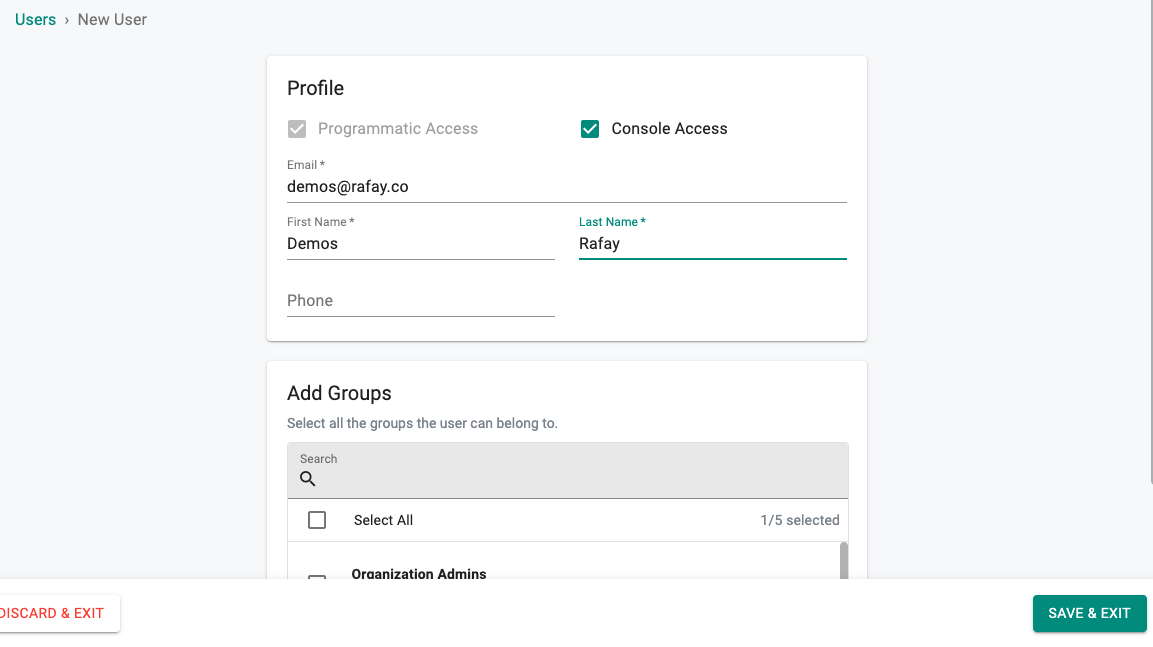
- Navigate to System -> Users
- Click on New User
- Input appropriate details (do not add any groups as yet)
- Click Save & Exit
- You will see a pop-up stating that the user has not been assigned to any groups. Select Yes to continue
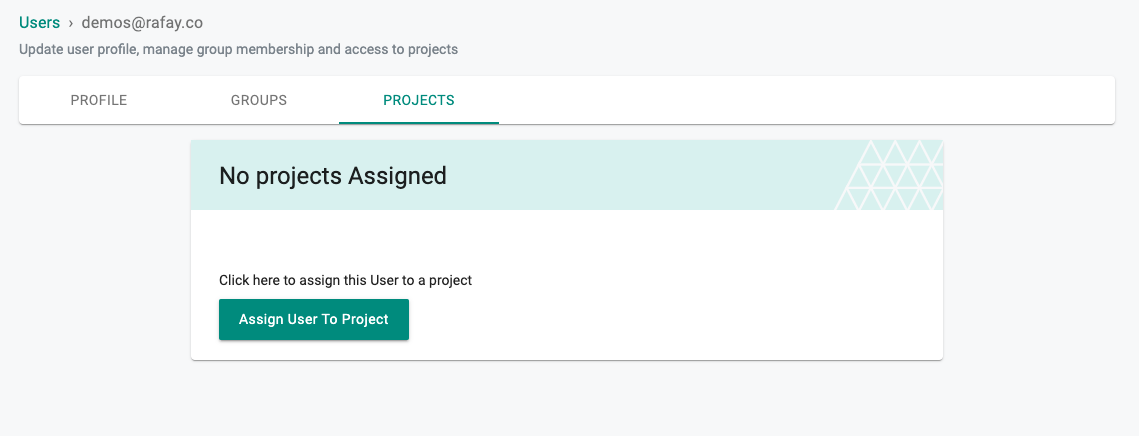
- Select the user that was just created
- Click on the Projects tab
- Select Assign User To Project
- Select alpha project from the dropdown on the left
- Select the Project Admin role or Infra Admin role
-
Click Save & Exit
-
Log out of the console now and log in as the user that was created
- You can now notice that the user only has access to alpha project and cannot view project beta (and the resources in project beta)
Recap¶
Congratulations! At this point, you have successfully leveraged "Projects" to achieve isolation between clusters belonging to two different teams.
Step 1: Create projects for alpha and beta teams¶
You can alternatively create projects by using the declarative spec. For more information on automation via RCTL CLI, refer here.
apiVersion: system.k8smgmt.io/v3
kind: Project
metadata:
description: self-contained unit for team alpha
name: alpha
spec:
default: false
- Type the command below to create project alpha
rctl apply -f <path-to-filename>.yaml
- Repeat the same exercise and create another project for team beta
Step 2: Create cluster entries, download bootstrap¶
An illustrative example of the cluster spec YAML file is shown below.
kind: Cluster
metadata:
name: alpha-cluster
project: alpha
spec:
type: imported
# location, can be custom or predefined
location: newyorkcity-us
blueprint: minimal
- Type the command below to create a cluster entry in project alpha
rctl create cluster -f <path-to-filename>.yaml
- Type the command below to download the cryptographically unique bootstrap YAML required to register the cluster
rctl get clusterbootstrap alpha-cluster -o yaml > <path-to-bootstrap-filename>.yaml
Step 3: Apply bootstrap to initiate the import process¶
Use kubectl to apply the "cluster bootstrap" file on your K8s cluster.
kubectl apply -f [path to file]/alpha-cluster-bootstrap.yaml
This will create a namespace for the k8s mgmt operator, download the container images, and register with the controller. This one time import process can take ~2 minutes.
namespace/rafay-system created
serviceaccount/system-sa created
clusterrole.rbac.authorization.k8s.io/rafay:manager created
clusterrolebinding.rbac.authorization.k8s.io/rafay:rafay-system:manager-rolebinding created
clusterrole.rbac.authorization.k8s.io/rafay:proxy-role created
clusterrolebinding.rbac.authorization.k8s.io/rafay:rafay-system:proxy-rolebinding created
priorityclass.scheduling.k8s.io/rafay-cluster-critical created
role.rbac.authorization.k8s.io/rafay:leader-election-role created
rolebinding.rbac.authorization.k8s.io/rafay:leader-election-rolebinding created
customresourcedefinition.apiextensions.k8s.io/namespaces.cluster.rafay.dev created
customresourcedefinition.apiextensions.k8s.io/tasklets.cluster.rafay.dev created
customresourcedefinition.apiextensions.k8s.io/tasks.cluster.rafay.dev created
service/controller-manager-metrics-service-v3 created
deployment.apps/controller-manager-v3 created
configmap/connector-config-v3 created
configmap/proxy-config-v3 created
deployment.apps/rafay-connector-v3 created
service/rafay-drift-v3 created
validatingwebhookconfiguration.admissionregistration.k8s.io/rafay-drift-validate-v3 created
Repeat Steps (3) and (4) with Project "beta" and cluster "beta-cluster".
Step 4: Verify that the clusters are imported to the right projects¶
On the console, you will notice that the imported cluster would have registered itself and will start receiving instructions from the controller. You can also check the status of the mgmt operator pods on your cluster using kubectl.
kubectl get po -n rafay-system
You should something like
NAME READY STATUS RESTARTS AGE
controller-manager-v3-66dfbd5db4-v97vw 1/1 Running 0 68s
edge-client-84499dfdd4-qn67q 1/1 Running 0 71s
rafay-connector-v3-7fb99b5cd9-clh2g 1/1 Running 0 68s
relay-agent-556c86f7bc-chxk8 1/1 Running 0 2m49s
Once the k8s operator is operational, it will "establish and maintain a heartbeat" with the controller.
Step 5: Create "project specific roles" for users¶
- Navigate to System -> Users
- Click on New User
- Input appropriate details (do not add any groups as yet)
- Click Save & Exit
- You will see a pop-up stating that the user has not been assigned to any groups. Select Yes to continue
- Select the user that was just created
- Click on the Projects tab
- Select Assign User To Project
- Select alpha project from the dropdown on the left
- Select the Project Admin role or Infra Admin role
-
Click Save & Exit
-
Log out of the console now and log in as the user that was created
- You can now notice that the user only has access to alpha project and cannot view project beta (and the resources in project beta)
Recap¶
Congratulations! At this point, you have successfully leveraged "Projects" to achieve isolation between clusters belonging to two different teams.