Controlled Access
What Will You Do¶
In this part of the self-paced exercise, you will associate a role with a user based on the least privilege principle and verify scope of kubectl access for the user. The role association will ensure that the user's kubectl acess is restricted based on their corporate identity. You will also configure kubectl settings to allow only web based access.
Step 1: Role Assignment¶
We will restrict the scope of the user to a particular namespace and will associate the Namespace Admin role to achieve the same.
- Click on Home -> SYSTEM and select Users from the drop-down menu
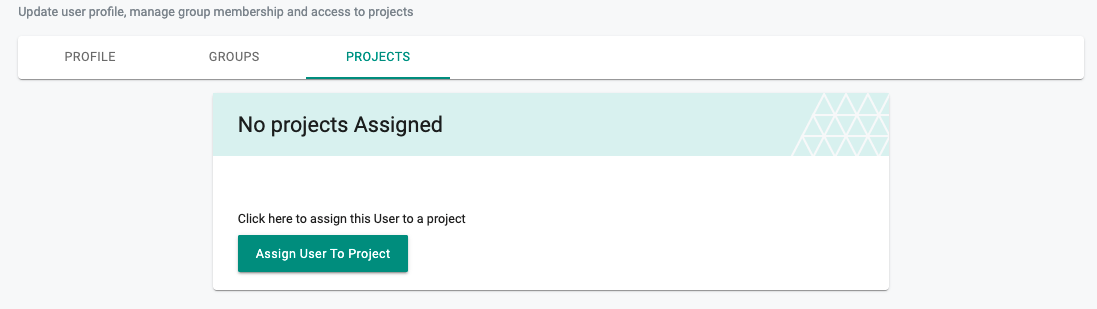
- Select the user from the list, click on the Projects Tab
- Click on Assign User to Project
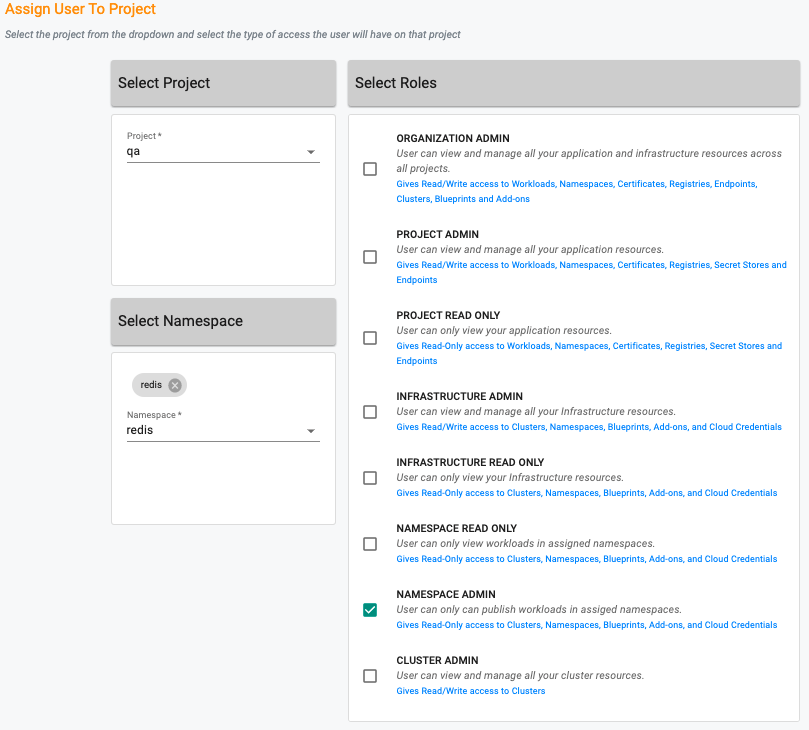
- Select the Project from the drop-down menu, select the Namespace Admin role and select the Namespace from the dropdown menu
- You have now associated the user with the Namespace Admin role
Step 2: Configure KubeCTL settings¶
- Click on Home -> SYSTEM and select Settings from the drop-down menu
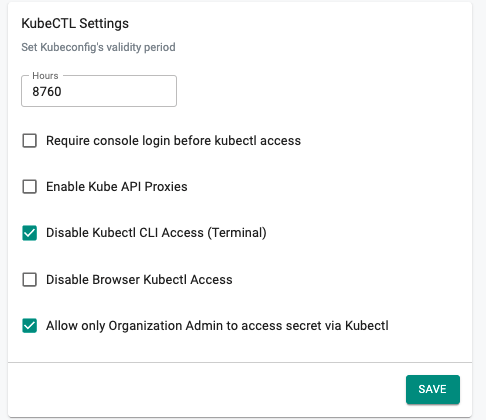
- Configure the KubeCTL Settings as desired. For this example, we will disable Kubectl CLI Access and Allow only Org Admin to access Secret (only allow Browser Kubectl Access). This configuration will apply to all users in the organization
Step 3: Verify scope of KubeCTL access¶
- Log in to the console as the Namespace Admin
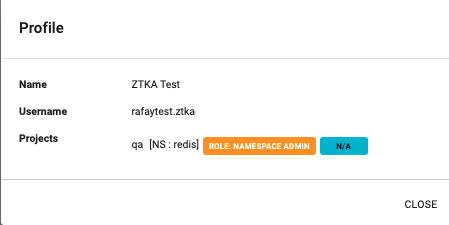
- Verify the role association by clicking on the user account (right hand top corner) and selecting Profile from the drop-down
- Navigate to the Namespace
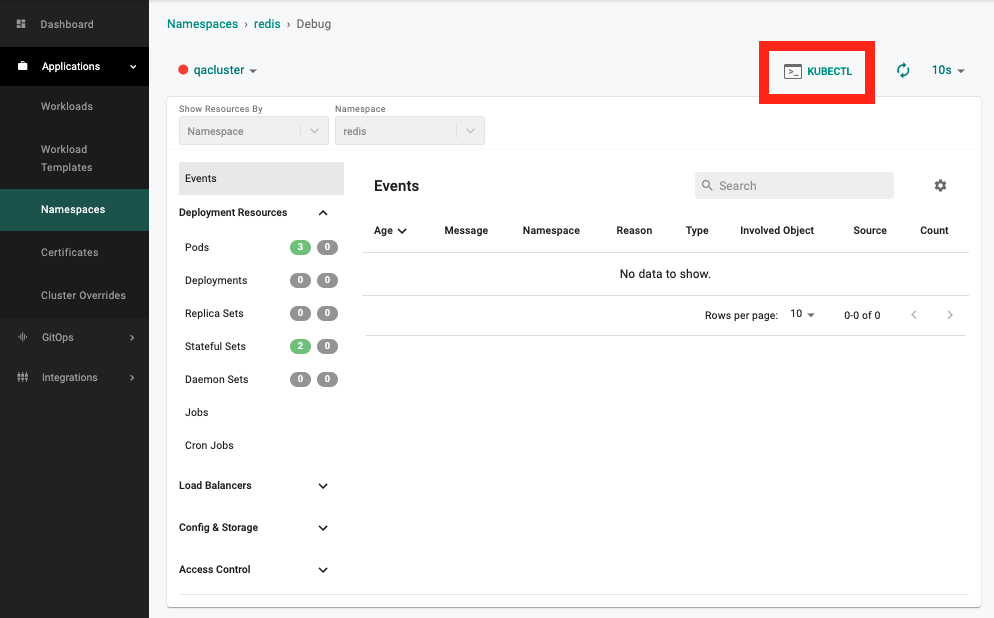
- Select the Namespace, click on the Publish Tab and Click on DEBUG
- Clicking on KUBECTL opens an interactive kubectl session within the browser
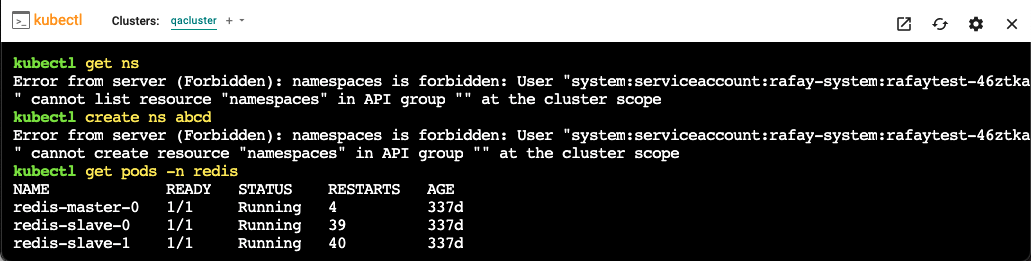
- Since the user is associated with the Namespace Admin role, commands such as kubectl get ns or kubectl create namespace are prevented. The RBAC role configured for the user is thus automatically enforced for kubectl access
Note
- RBAC is automatically enforced for kubectl CLI access (Terminal) as well
- A JIT service account is created (post authentication/authorization process) when a kubectl access is initially attempted, the service account is removed after a defined period
- Auto completion feature of commands is available with kubectl web access to make it easier for users