Setup
What Will You Do¶
This is Part 1 of a multi-part, self-paced quick start exercise. In this part, you will use the Infra Admin persona to setup and configure the needed resources to use Environment Manager.
Step 1: Import Template¶
In this step, you will use the Loader Utility to import the Environment Manager templates needed for this environment.
- Follow the instructions here to use the loader utility
- When using the loader utility, be sure to uncomment the following template - ../terraform/gcp/101-vpc-instance in the templates section of the values.yaml file
Step 2: Configure Environment Contexts¶
In this step, you will configure an environment context in the controller with your GCP account details. These account details will be used by Environment Manager to interact with your cloud account.
- Follow the step-by-step instructions to setup GCP and obtain the required JSON credentials file
- Encode the contents of the JSON file into base64
- Log into the controller and select your project
- Navigate to Environments -> Contexts
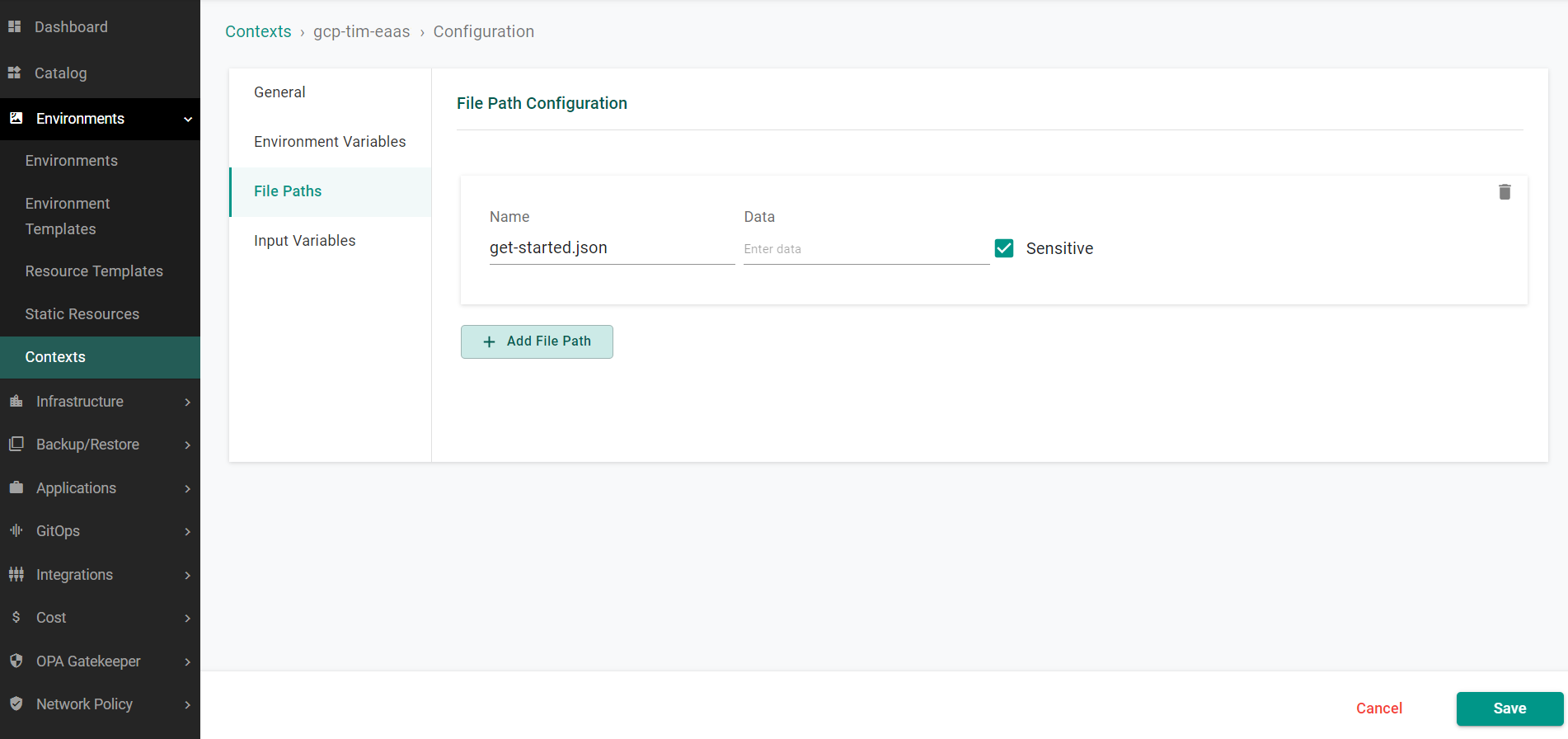
- Click on the existing context name
- Select File Paths
- Populate the data field for the file path with the base64 encoded credentials
- Ensure that you select the sensitive checkbox for the inputs
- Click Save
Important
The Rafay agent automatically writes back the environment variables to Git. The resources (esp. secrets) you identify as sensitive. will be automatically encrypted using a secret sealer before being synced to your Git repo.
Step 3: Configure Template Variables¶
In this step, you will review the resource templates and environment templates to ensure that all variables are updated for your environment.
- Navigate to Environments -> Resource Templates
- Click on the resource templates that were created
- Click the view icon of the template version
- Verify all Input Variables
If any Input variables need to be modified, create a new version of the template with the modified variables. If a new version is created, be sure to update the Environment Template with any updated resource template versions.
- Navigate to Environments -> Environment Templates
- Click on the environment template that was created
- Click the view icon of the template version
- Verify all Input Variables
If any input variables need to be modified, create a new version of the template with the modified variables.
Recap¶
At this point, you have everything setup and configured to manage environments through Environment Manager.