Part 2: Create Resources
This is Part 2 of a multi-part, self-paced quick start exercise.
What Will You Do¶
In part 2, you will setup the backup/restore resources in order to perform backup and restore operations. You will:
- Create IRSAs
- Create backup Cloud Credentials
- Create backup locations for control plane and persistent volumes
- Create data agents
- Create backup and restore policies
Step 1: Create IRSAs¶
In this step, we will create an IRSA for each cluster that will perform backup/restore operations in order to provide the backup/restore pods with the appropriate permissions needed to access the Amazon S3 bucket which will store the backup data.
- Save the below IAM policy to a local file with the name "backup-iam-policy.json"
- Update the S3 bucket name with your S3 bucket name
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:DescribeVolumes",
"ec2:DescribeSnapshots",
"ec2:CreateTags",
"ec2:CreateVolume",
"ec2:CreateSnapshot",
"ec2:DeleteSnapshot"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:DeleteObject",
"s3:PutObject",
"s3:AbortMultipartUpload",
"s3:ListMultipartUploadParts"
],
"Resource": [
"arn:aws:s3:::<bucket_name>/*"
]
},
{
"Effect": "Allow",
"Action": [
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::<bucket_name>"
]
}
]
}
- Run the below command for each cluster that will use backup/restore. Ensure to update the cluster name with your cluster name
rctl create iam-service-account <cluster-name> --name velero-rafay --namespace rafay-system --policy-document backup-iam-policy.json --role-only
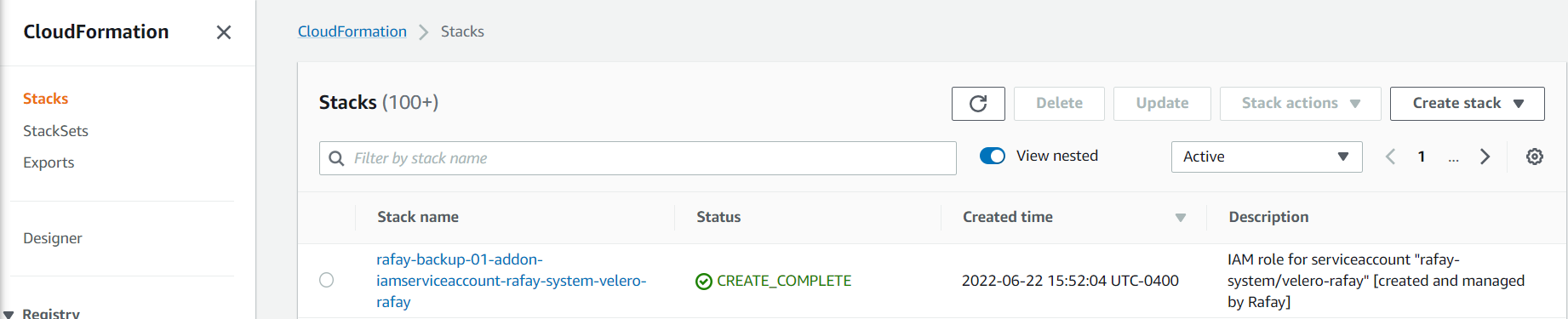
- Login to the AWS console
- Navigate to CloudFormation
- Locate the recently created stacks with a description similar to the below description
IAM role for serviceaccount "rafay-system/velero-rafay" [created and managed by Rafay]
- Click on the stack
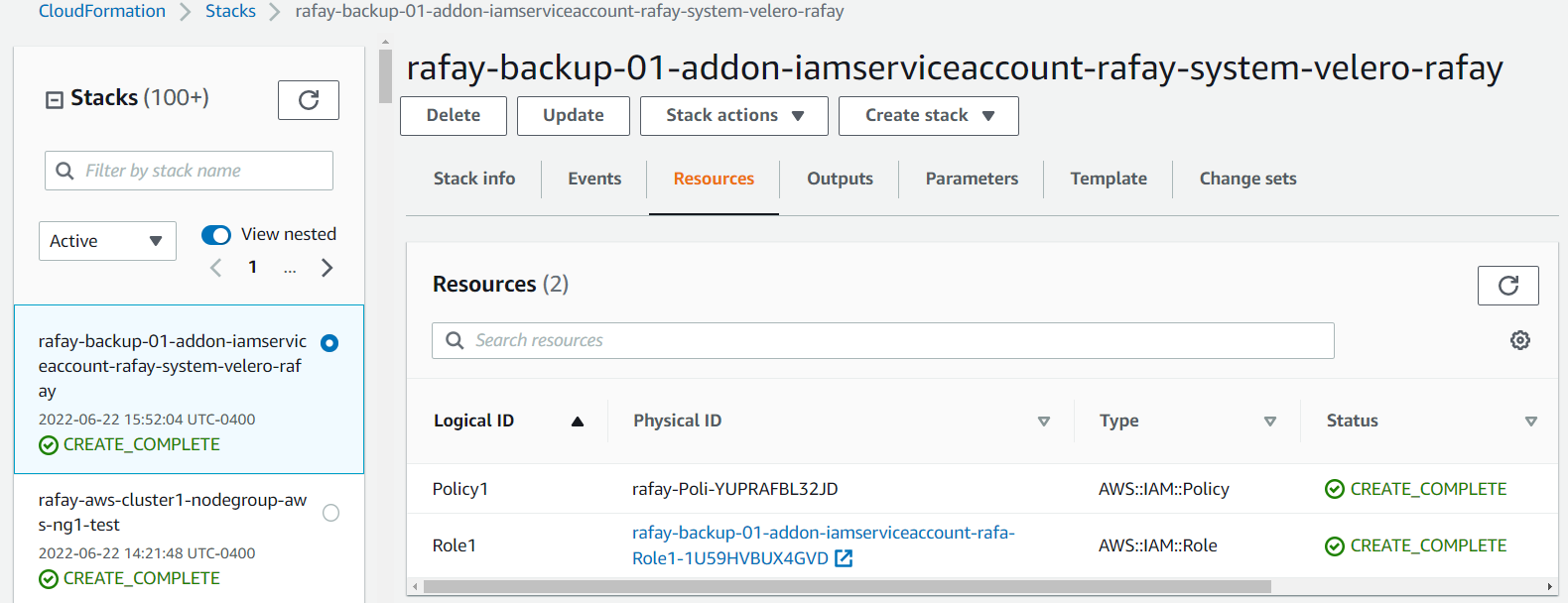
- Navigate to the "Resources" tab of the stack
- Click on the IAM role
- Copy the role ARN in each stack for later use
Step 2: Create Backup Cloud Credential¶
In this step, you will create cloud credentials for each of the clusters that will perform backup or restore operations. You will need the IAM role ARNs from the previous step in order to create the cloud credentials for each cluster.
Perform the following steps for each cluster where backup or restore operations will be peformed. Ensure to use the IAM Role ARN from the previous step for each cluster's cloud credential.
- Ensure you are logged into the console
- In your project, navigate to Infrastructure -> Cloud Credentials
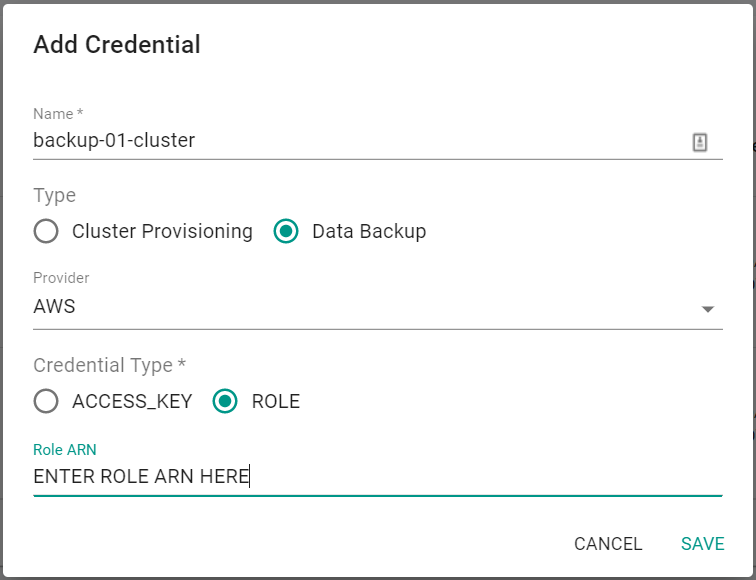
- Click on "New Credential"
- Provide a name for the Credential
- Select "Data Backup" for Type
- Select "AWS" for Provider
- Select "Role" for Credential Type
- Enter the IAM Role ARN from the previous step for the cluster
- Click "Save"
- Perform the previous steps again for the second cluster
Alternatively, you can create the cloud credential using RCTL and build this into an automation pipeline. The following command could be used ensuring the credential name and role ARN are updated first.
rctl create credential aws <name> --cred-type data-backup --role-arn <role_arn>
Step 3: Create Backup Locations¶
In this step, we will create two backup locations which will store the control plane backup data and persistent volume data respectively. We will use an Amazon S3 bucket to store the data.
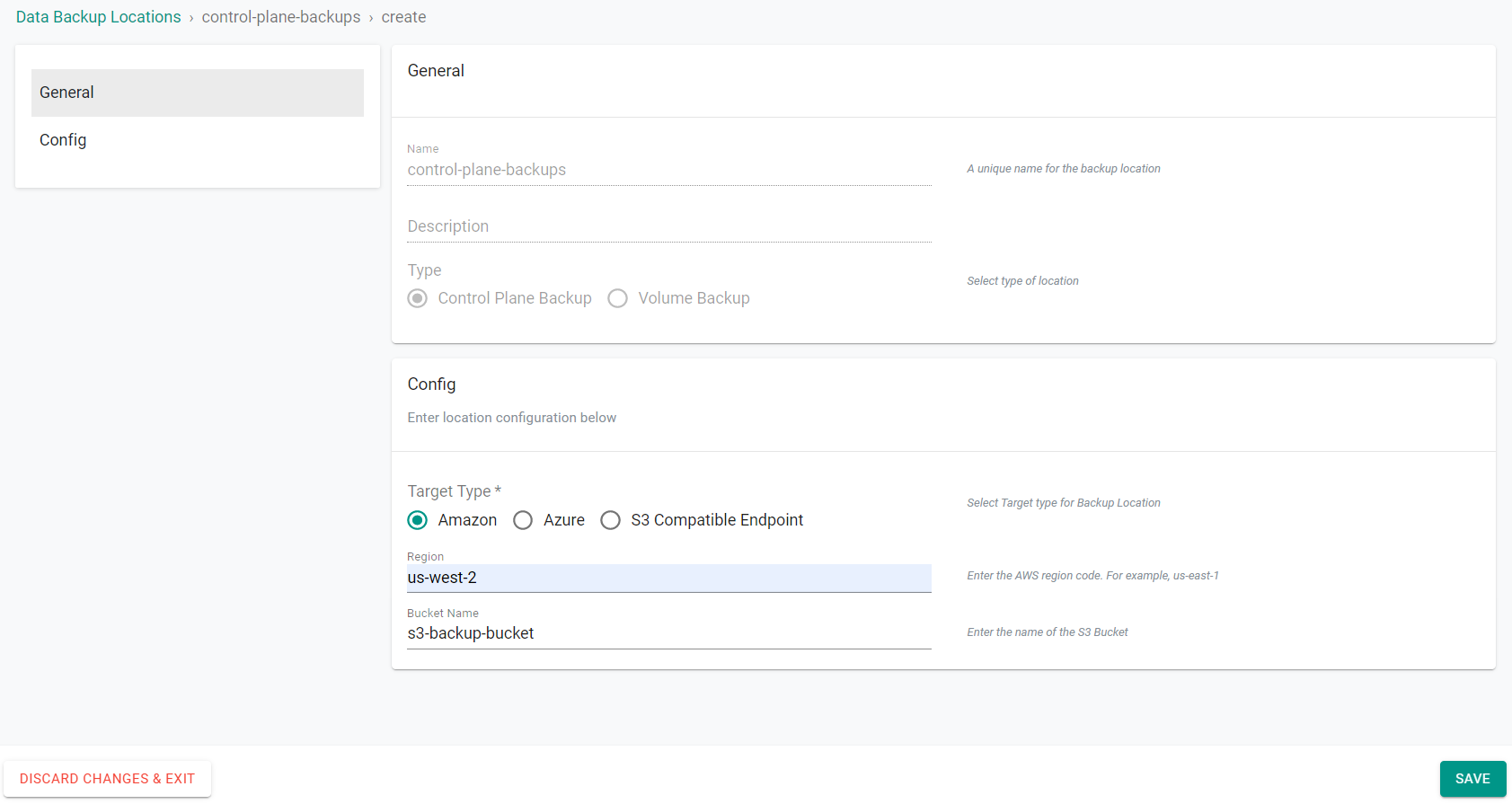
First, we will create the backup location for the Control Plane backups.
- In your project, navigate to Backup/Restore -> Locations
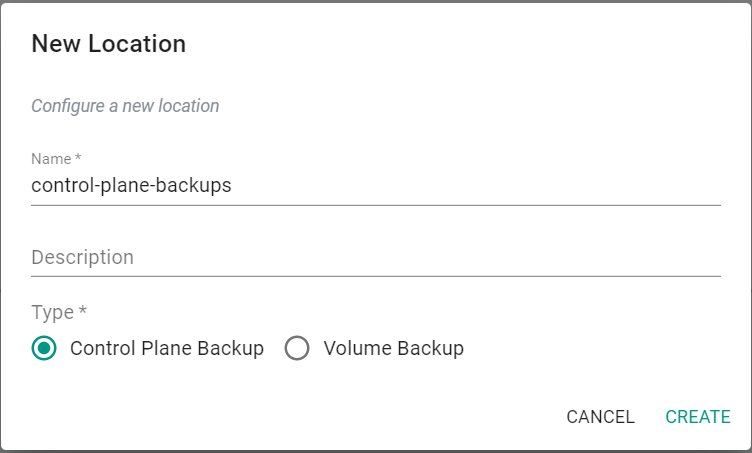
- Click on "New Location"
- Provide a name for the Location
- Select "Control Plane Backup" for Type
- Click "Create"
- Select "Amazon" for the Target Type
- Enter the AWS region where the bucket is located
- Enter the S3 bucket name
- Click "Save"
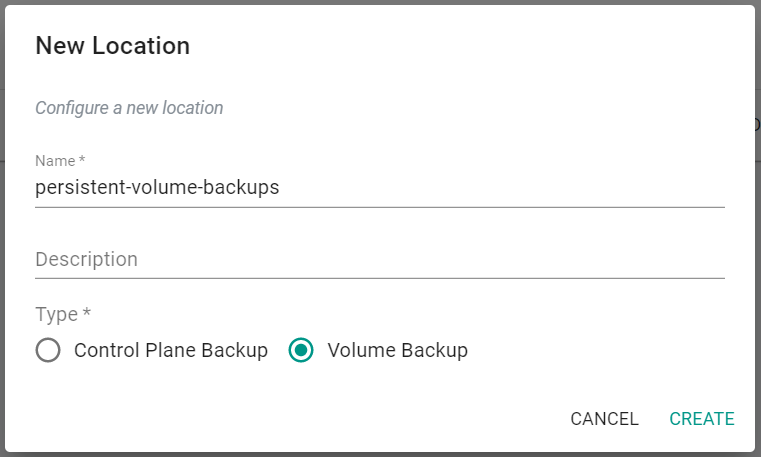
- Navigate to Backup/Restore -> Locations
- Click on "New Location"
- Provide a name for the Location
- Select "Volume Backup" for Type
- Click "Create"
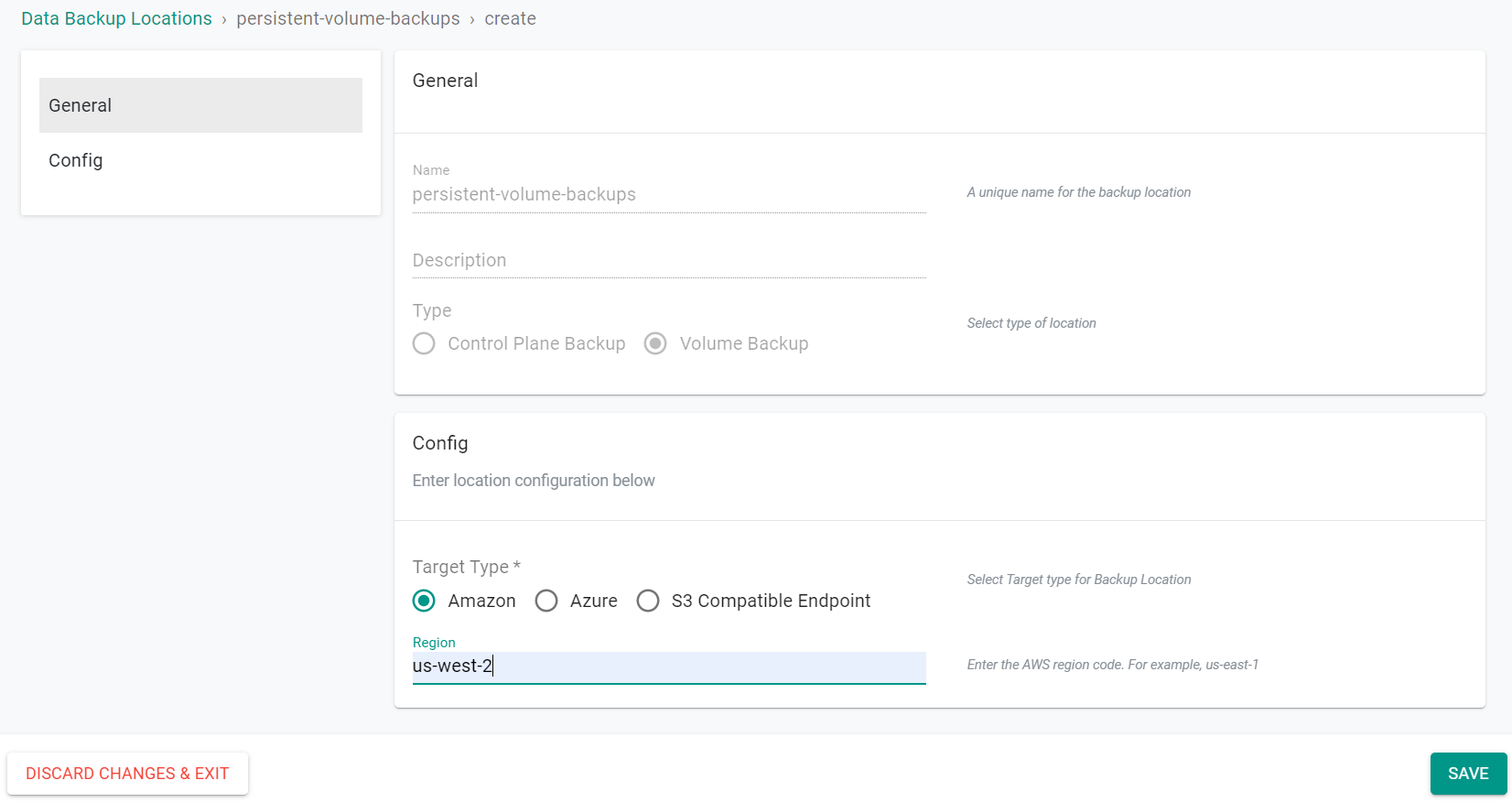
- Select "Amazon" for the Target Type
- Enter the AWS region where the bucket is located
- Click "Save"
Alternatively, you can create the backup locations using RCTL and build this into an automation pipeline. The following commands could be used ensuring the location name, bucket region and bucket name are updated first.
rctl create dp-location <name> --backup-type controlplanebackup --target-type amazon --region <region> --bucket-name <bucketname>
rctl create dp-location <name> --backup-type volumebackup --target-type amazon --region <region> --bucket-name <bucketname>
Step 4: Create Data Agents¶
In this step, we will create a data agent on each cluster where a backup or restore operation will occur. The agent on each cluster will be used to perform the backup/restore operations.
Perform the following steps for each cluster where backup or restore operations will be peformed.
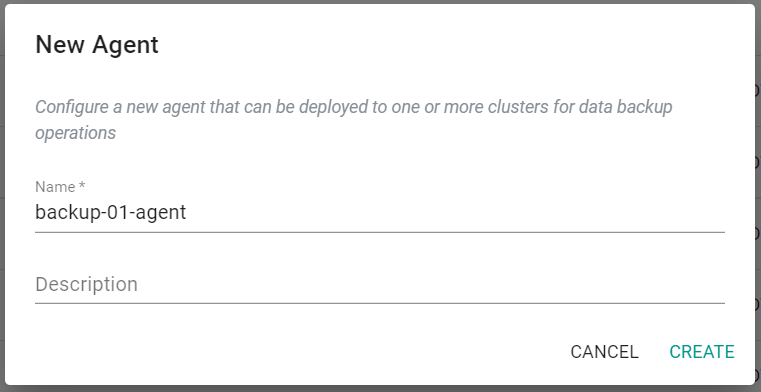
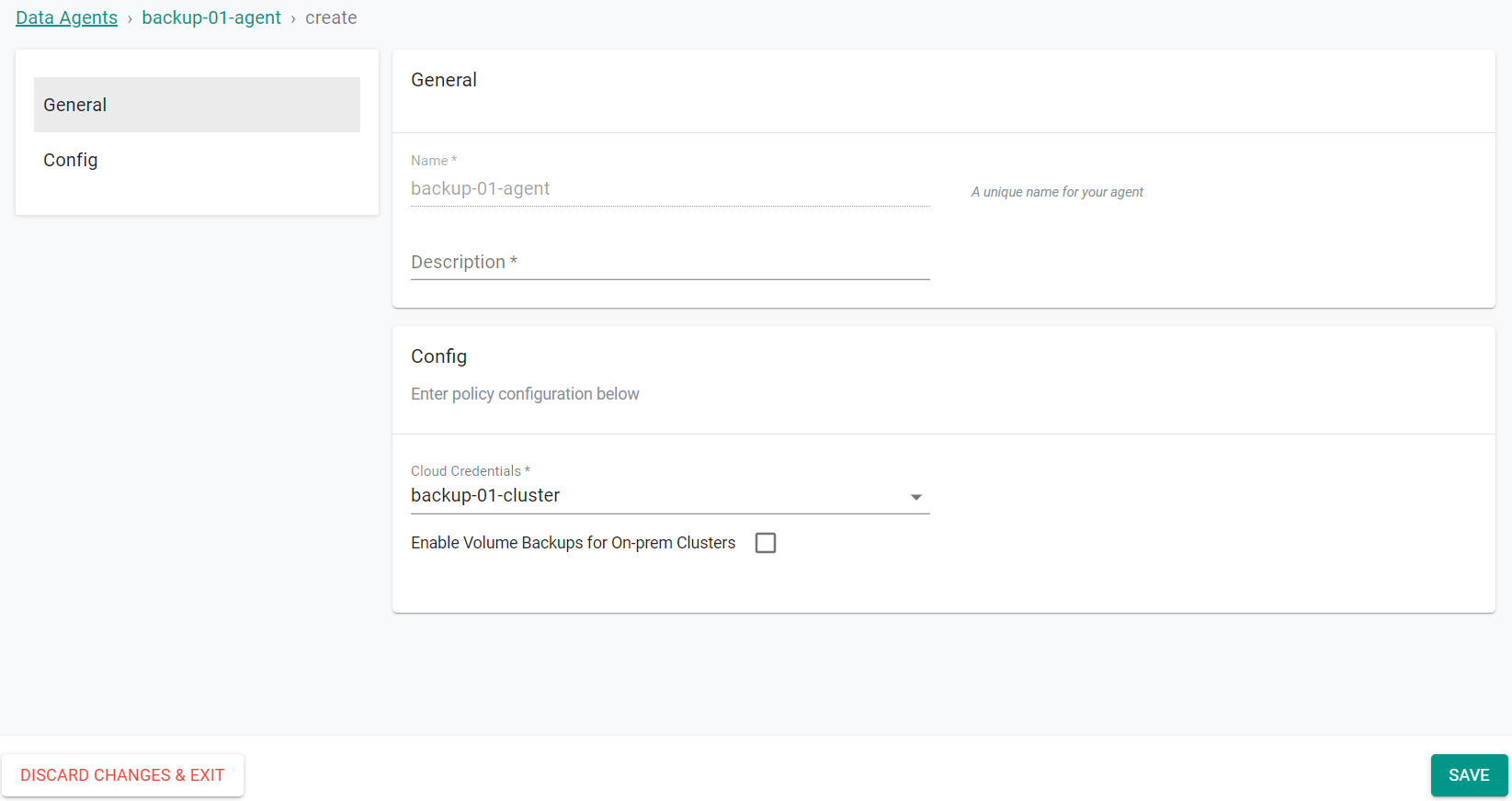
- In your project, navigate to Backup/Restore -> Data Agents
- Click on "New Agent"
- Provide a name for the Data Agent
- Click "Create"
- Select the cloud credential of the cluster where the data agent will be deployed
- Click "Save"
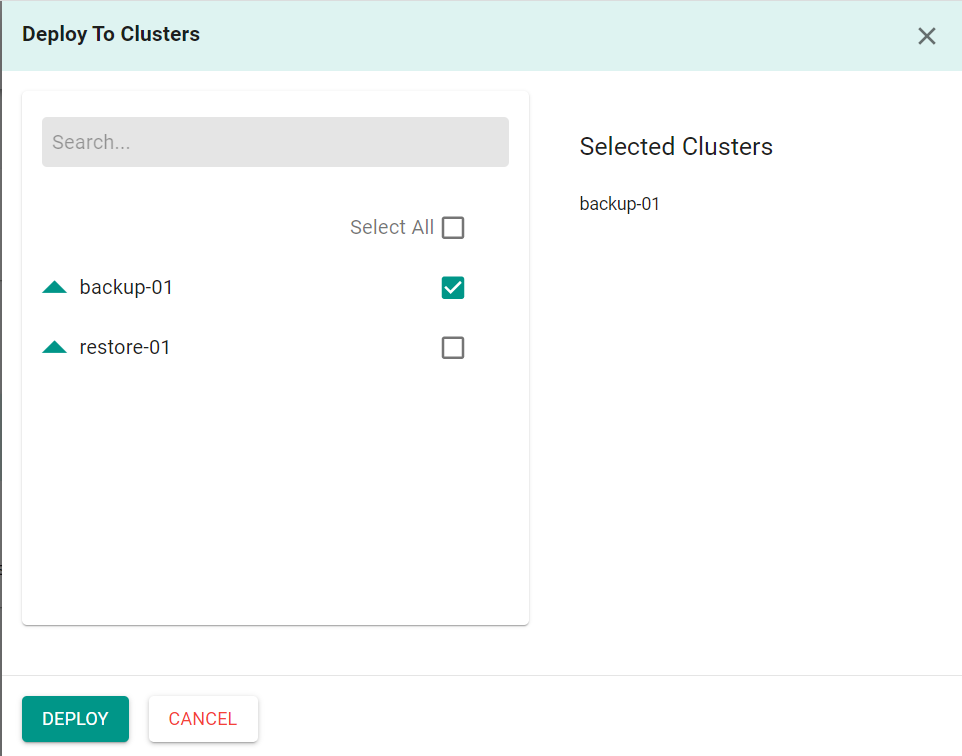
We must now deploy the agent to a cluster.
- Click "Deploy to Clusters"
- Select the cluster
- Click "Deploy"
- Perform the previous steps again for the second cluster
Alternatively, you can create and deploy the data agents using RCTL and build this into an automation pipeline. The following commands could be used ensuring the data agent name, cloud credential name and cluster name are updated first.
rctl create dp-agent <name> --cloud-credentials <cloudcredentials>
rctl deploy dp-agent <agent-name> --cluster-name <cluster-name>
Step 5: Create Backup and Restore Policies¶
In this step, you will create both a backup and a restore policy.
First, you will create a backup policy.
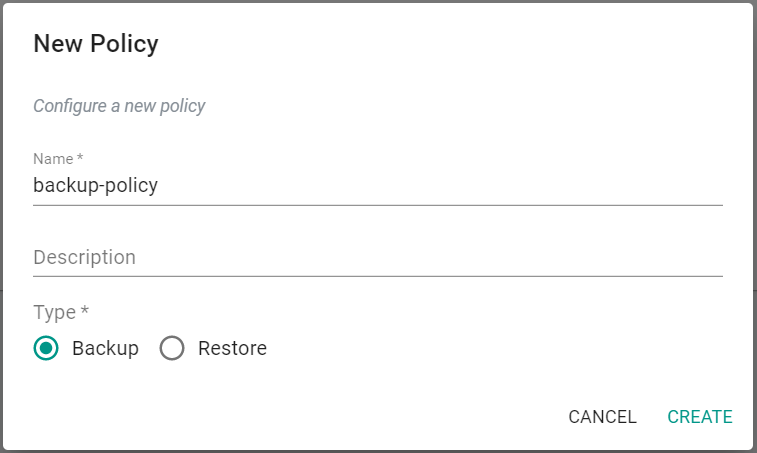
- In your project, navigate to Backup/Restore -> Policies
- Click on "New Policy"
- Provide a name for the backup policy
- Select "Backup" for Type
- Click "Create"
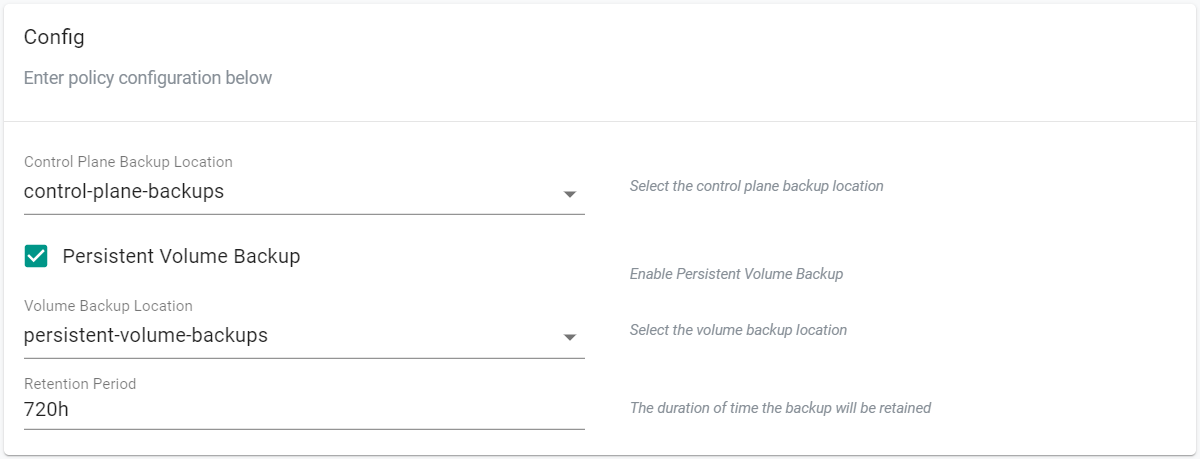
- Under the "Config" section, select the control plane backup location that was previously created
- Select "Persistent Volume Backups" to enable it
- Select the volume backup location that was previously created
- Click "Save"
Alternatively, you can create the backup policy using RCTL and build this into an automation pipeline. The following command could be used ensuring the policy name, control plane location and volume location are updated first.
rctl create dp-policy <name> --type backup --location <location> --snapshot-location <snapshot-location> --retention-period 720h
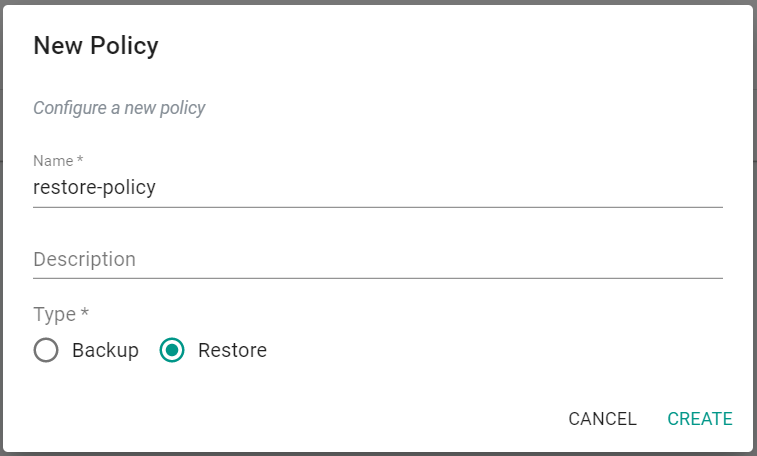
Now, you will create a restore policy.
- Navigate to Backup/Restore -> Policies
- Click on "New Policy"
- Provide a name for the restore policy
- Select "Restore" for Type
- Click "Create"
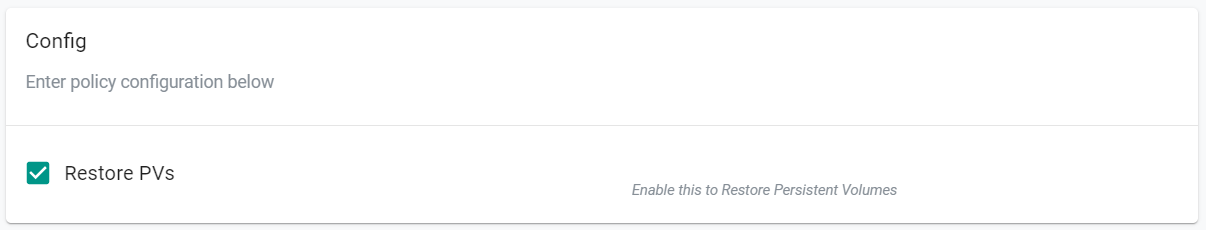
- Under the "Config" section, select "Resore PVs"
- Click "Save"
Alternatively, you can create the restore policy using RCTL and build this into an automation pipeline. The following command could be used ensuring the policy name is updated first.
rctl create dp-policy <name> --type restore --restore-pvs
Recap¶
In this part, you have created the needed backup and restore resources in order to be able to initiate backup and restore jobs on your two clusters.