MFA
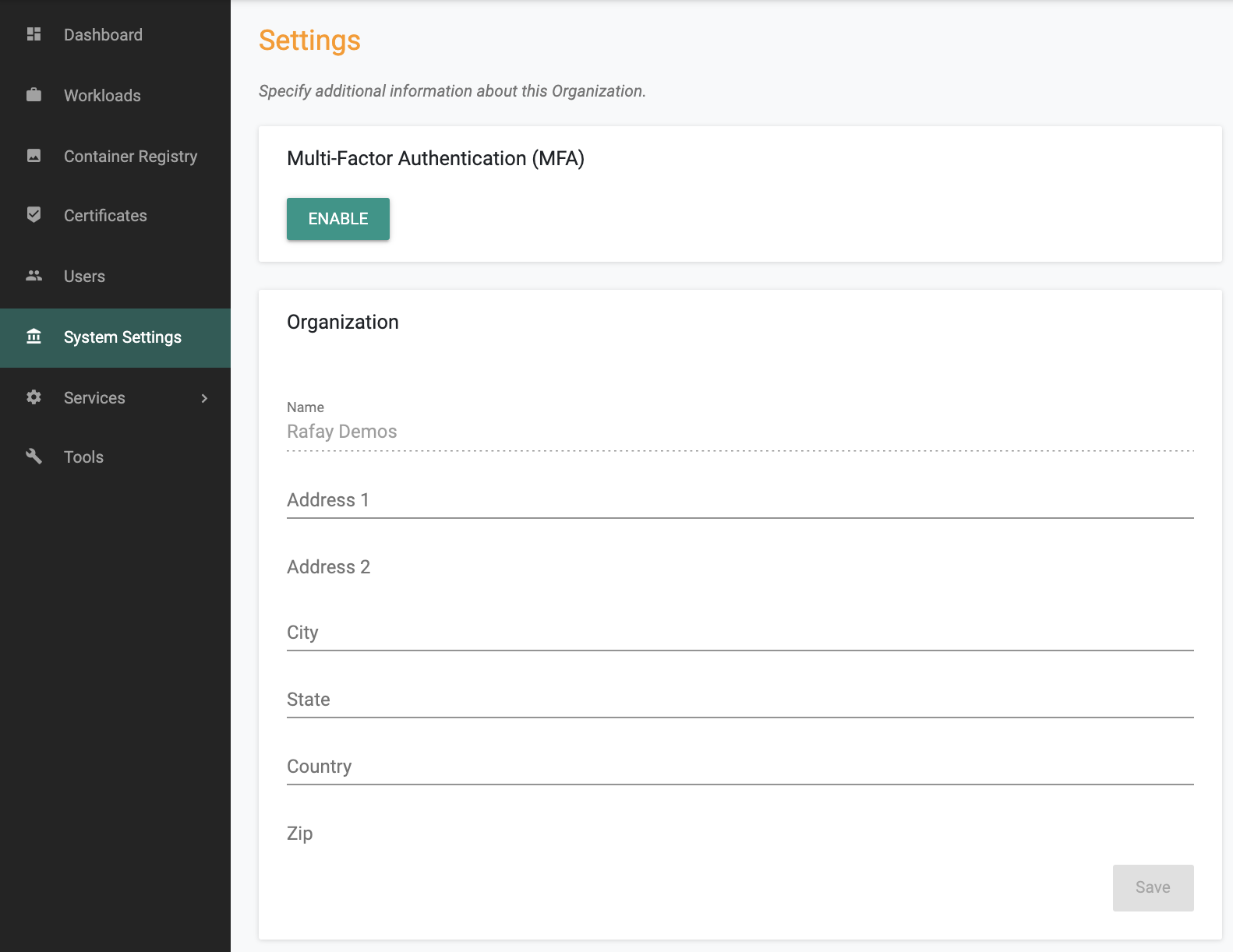
Org Admins can enable/require the use of TOTP as a second authentication factor. This allows users to be strongly authenticated before they are allowed access to the Org.
When a user attempts to login, the password based primary authentication is performed first. Once the primary authentication is successful, the user is prompted to verify their identity with MFA using TOTP. The user needs to pass both primary and secondary authentication methods before they are allowed access.
Supported Authenticators¶
ANY TOTP based Authenticator will work for MFA.
There are several authenticators available in the market with varying degrees of sophistication. We recommend that users select an authenticator that also supports the following capabilities on top of basic TOTP support. These capabilities are critical for end users especially when their phone has been stolen or broken.
- Multiple Device Support
- FaceID/TouchID protected access to TOTP app
- Cloud Backup and Recovery
Some illustrative examples of TOTP Authenticator apps are listed below:
Advanced Capabilities
Basic Capabilities
- Google Authenticator
- Microsoft Authenticator
- Okta Verify
Enabling MFA¶
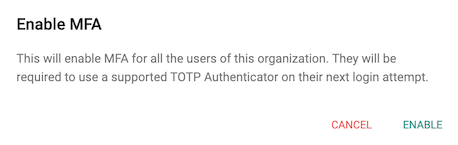
MFA is an Org wide configuration that can be enabled/disabled by Org Admins. Once enabled, all users in the Org will be prompted/required to enroll for MFA at their next login.
Note
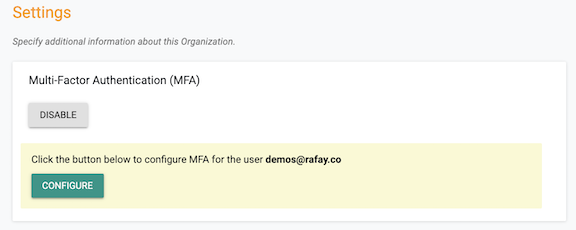
The admin that enabled MFA for the Org is reminded to enroll an MFA authenticator as well.
The Admin is warned that all users in the Org will be required to enroll for MFA at their next login attempt.
The admin that enabled MFA for the Org is also prompted to enroll for MFA.
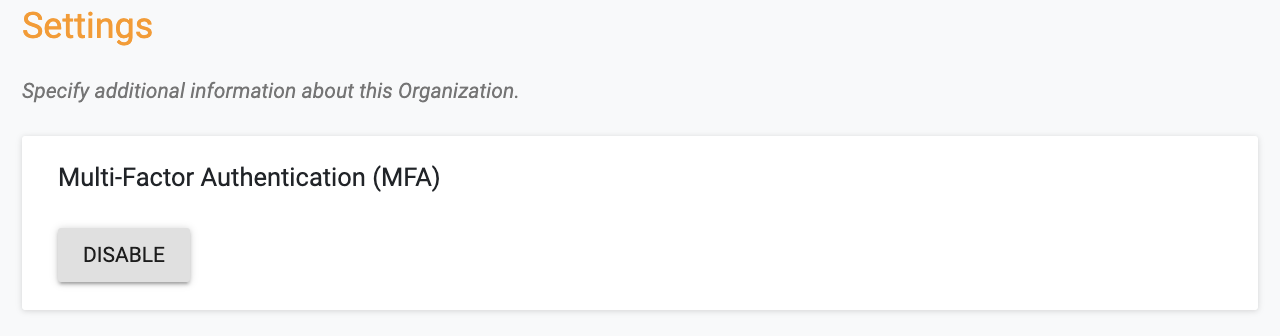
Disabling MFA¶
Org Admins in an Org can disable MFA for all users in their Org. Note that this can be performed only if MFA was previously enabled for the Org.
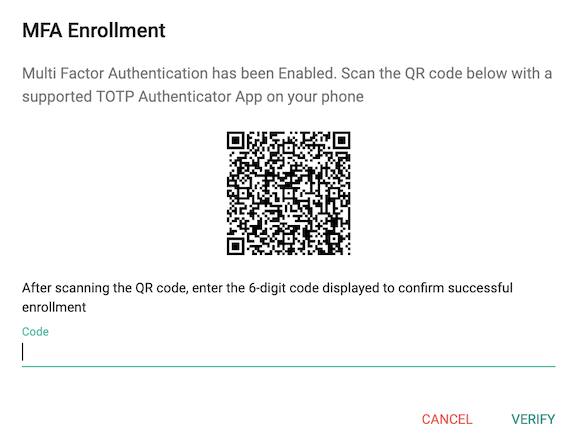
MFA Enrollment¶
If the user does not yet have a TOTP associated with their account (i.e. have not completed enrollment), they will be required to enroll an authenticator after passing primary authentication.
A QR code containing an automatically generated key will be presented to the user to be scanned by their TOTP Authentication App.
Enrollment is completed once the user enters the 6-digit code generated by their authenticator app.
The next time the enrolled user attempts to login into their Org, they will be required to type in the OTP code after they successfully login with their username and password.
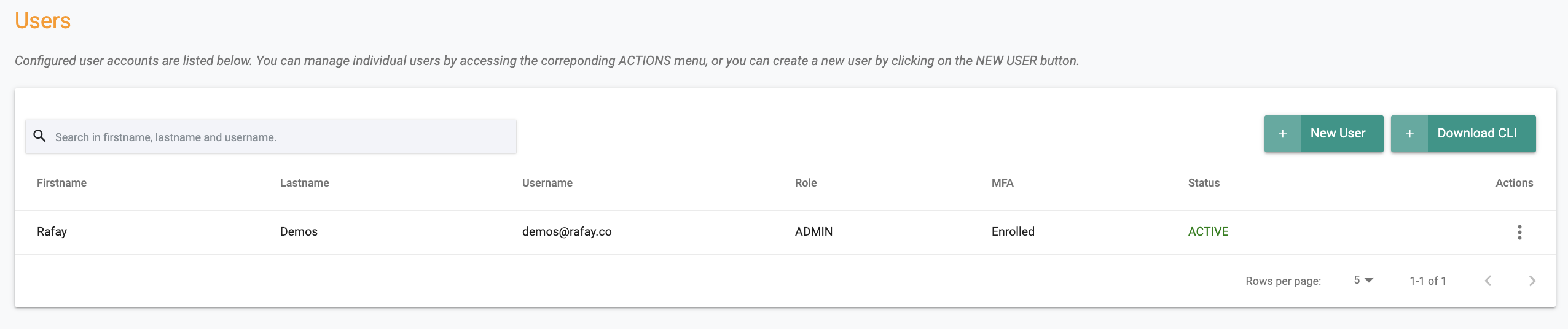
Admins can check MFA enrollment status for users in their Org by clicking on Users in the left panel. The MFA enrollment status is displayed in the column called MFA. The status can either be "Enrolled or Not Enrolled".
Reset MFA¶
If the user has either "lost" their phone with the TOTP authenticator app OR has a new phone with a new TOTP authenticator app, they may be unable to access the Web Console. When required, Org Admins can "Reset MFA" for a specific user. This forces the user to enroll into MFA again with their new phone/authenticator app.
- Navigate to System -> Users
- Click on "Reset MFA" for identified user