Part 1: Setup
This is Part 1 of a multi-part, self-paced quick start exercise.
What Will You Do¶
In part 1, you will perform a one-time configuration of resources to enable System Sync to communicate with a Git repository. You will use System Sync to create OPA resources in your project from the turnkey policies defined in the Git repository.
- Create a Gitops Agent
- Fork the "Turnkey OPA Gatekeeper Policy" Repository
- Create a Git repository
- Create a GitOps pipeline to enable System Sync
Step 1: Create GitOps Agent¶
We must first create a GitOps Agent that will allow the System Sync pipeline to access our Git repository.
- Ensure you are logged into the console
- In the default project, navigate to GitOps -> GitOps Agents
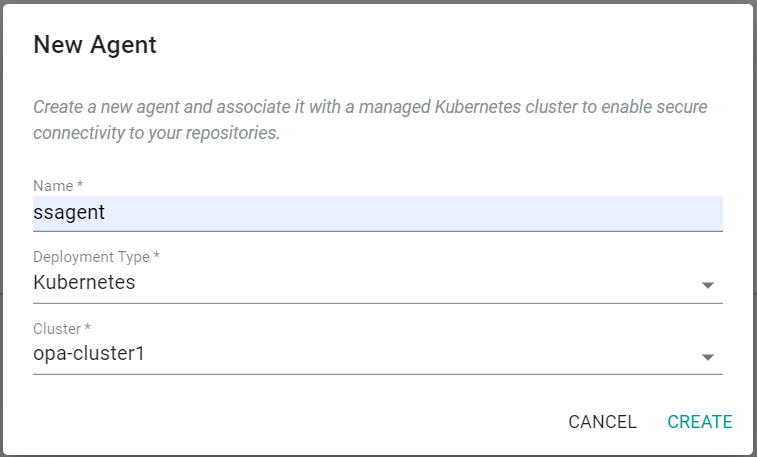
- Click on "New Agent"
- Provide a name for the Agent
- Select the cluster where the agent will be deployed
- Click "Create"
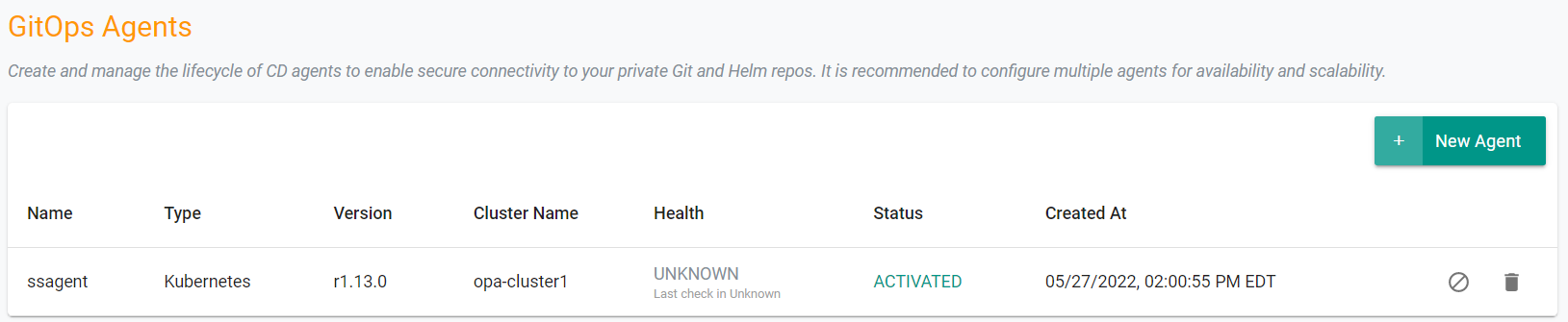
This will create an agent on the cluster specified. The agent will be used to communicate with the Git repository. It will take a few minutes for the agent to be deployed and become healthy.
Step 2: Fork Git Repo¶
Declarative specification files for the turnkey OPA resources are available in a Git repository
To get started, let us fork an existing repository.
- Ensure you are logged into your GitHub.com account
- Navigate to the public Git repository
- Click on Fork repository
- Select your account name to fork the repo to
- Once complete, you should see a copy of the repository in your Git system (e.g. GitHub)
- The Turnkey OPA resources are located in the "turnkey-opa" directory
Step 3: Add Repository¶
- In the default project, navigate to Integrations -> Repositories
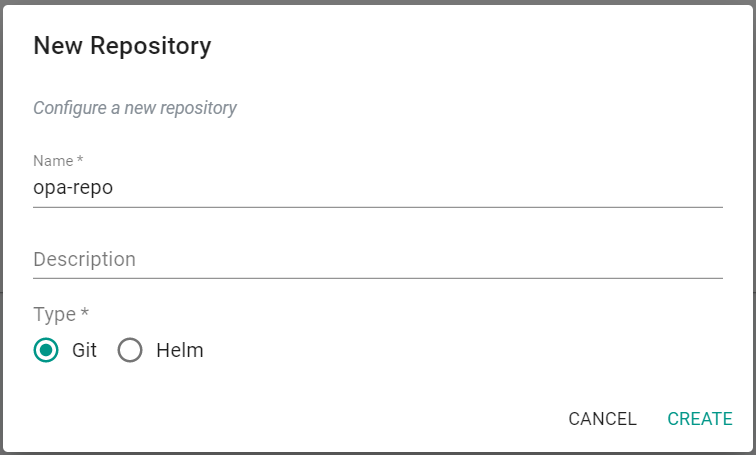
- Click "New Repository"
- Enter a name for the repository
- Select "Git" for Type
- Click "Create"
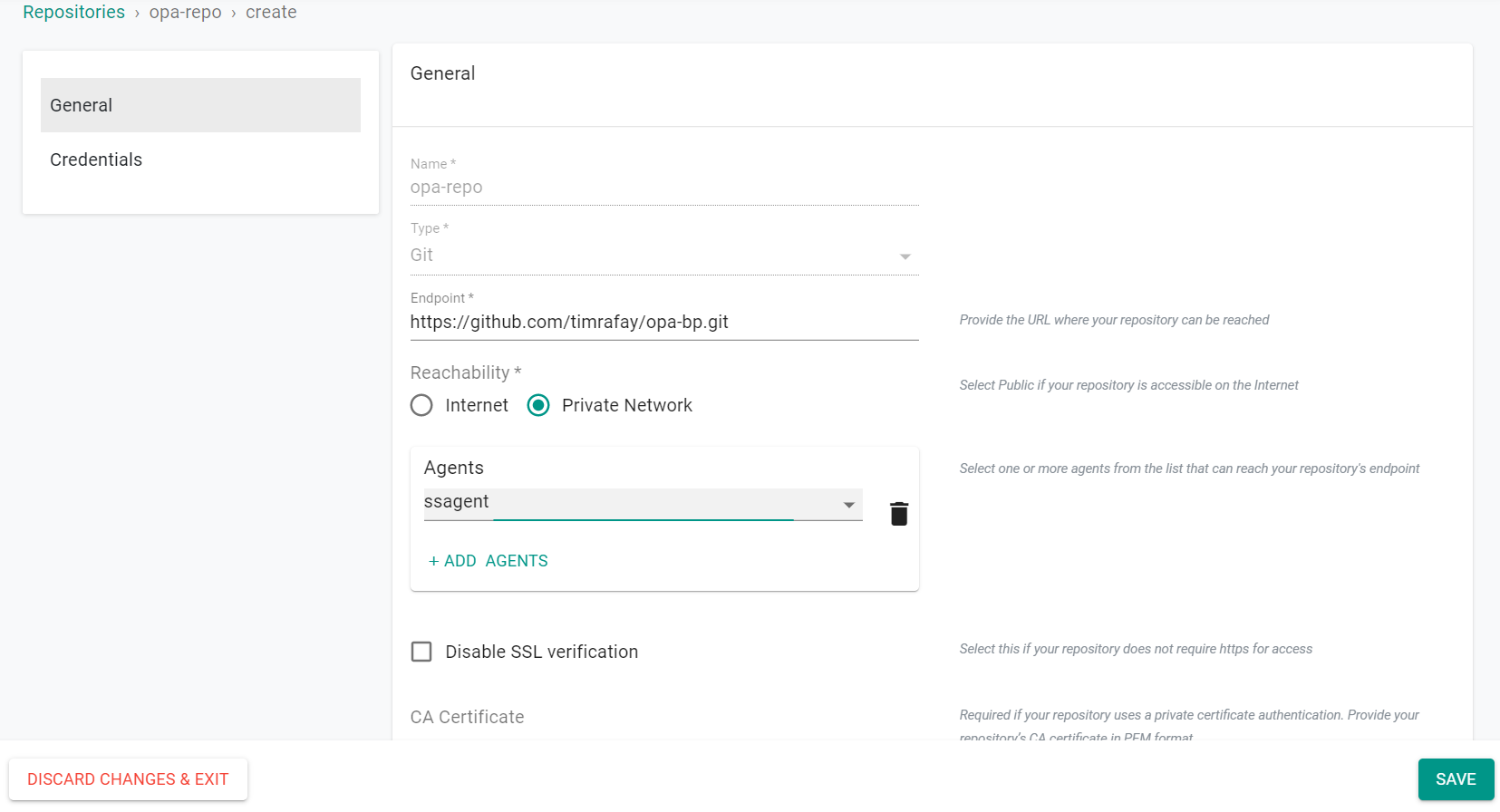
- Provide the forked Git repo's Endpoint URL
- Select "Private Network" for Reachability
- Select the agent that was previously created
- Click "Save"
Note
It does not matter if your GitHub repo is public or private. If private, you need to provide access credentials.
Optionally,
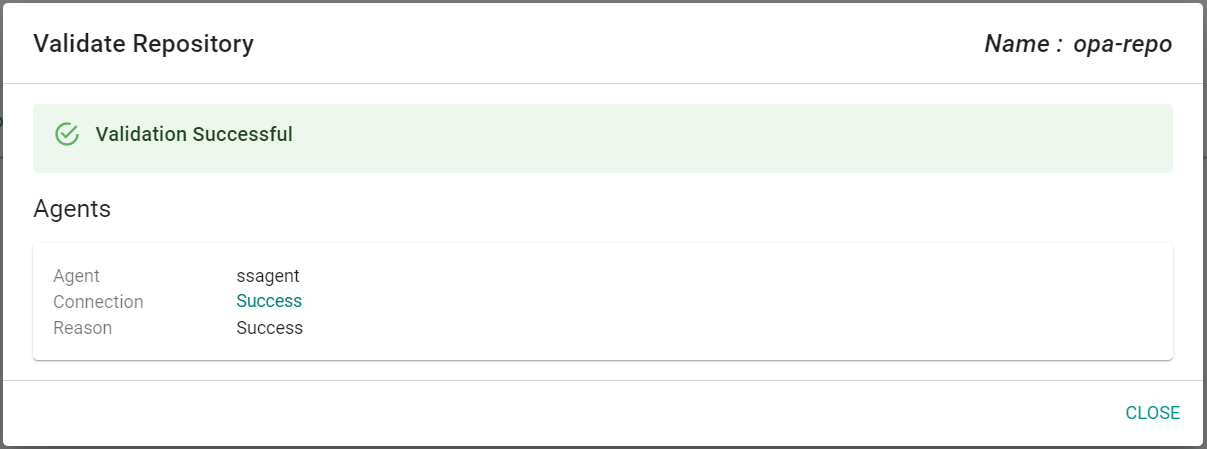
- Under Infrastructure -> Repositories, Click on validate for your repository
- If you see a validation successful message, the controller is able to access the repository
Step 4: GitOps Pipeline¶
The GitOps pipeline will ensure that the resources in the system are "always kept reconciled" with the desired specifications in the Git repository. It will also ensure the Git repository is reconciled with the system if a change is made directly from the console.
We will now create a GitOps Pipeline.
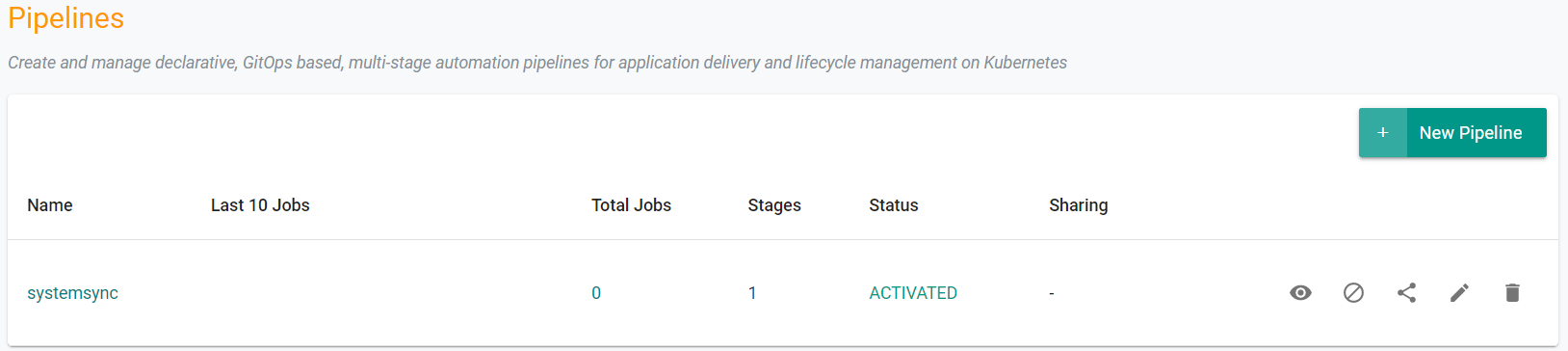
- Navigate to GitOps -> Pipelines
- Click "New pipeline"
- Enter a name for the pipeline
- Click "Create"
Add Stage¶
A pipeline can have multiple stages, with completely different actions to model your desired workflows. In this exercise, we will test with a simple, single stage pipeline.
- Under Stages, Click "Add New Stage"
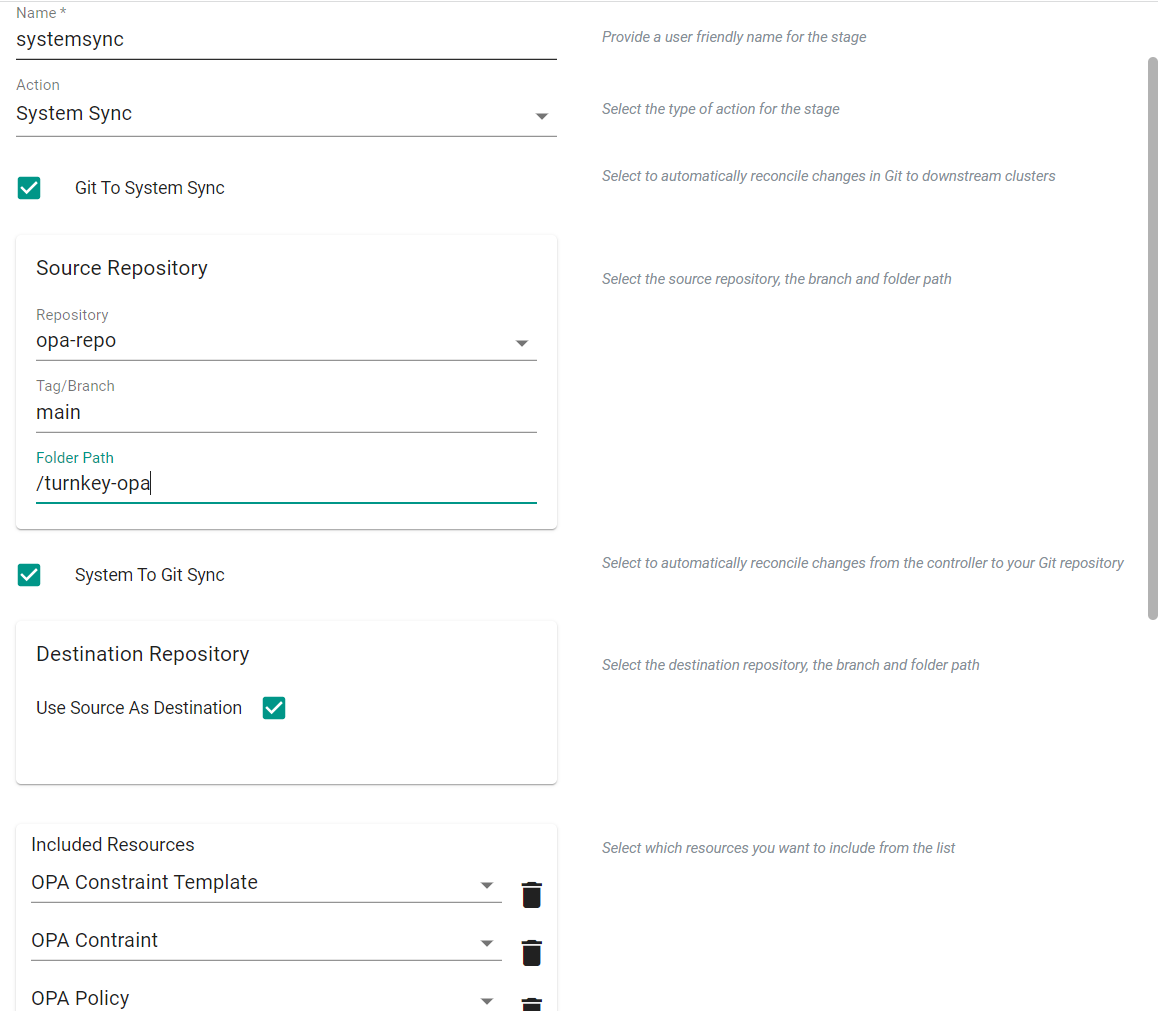
- Provide a name for the stage
- For Action, select "System Sync"
- Select "Git to System Sync"
- Select the previously created repository
- Enter "main" for the branch
- Enter '/turnkey-opa' for the folder path
- Select "System to Git Sync"
- Select "Use Source As Destination"
- Under "Included Resources", click "Add Resource"
- Select "OPA Constraint Template"
- Again, under "Included Resources", click "Add Resource"
- Select "OPA Constraint"
- Again, under "Included Resources", click "Add Resource"
- Select "OPA Policy"
- Click "Save"
Add Trigger¶
A pipeline can be executed based on an "external trigger". For example, changes to the manifests in your Git repository. In this exercise, we will configure a trigger that will receive a webhook notification when specific files in your Git repository are modified.
- Under Triggers, click "Add New Trigger"
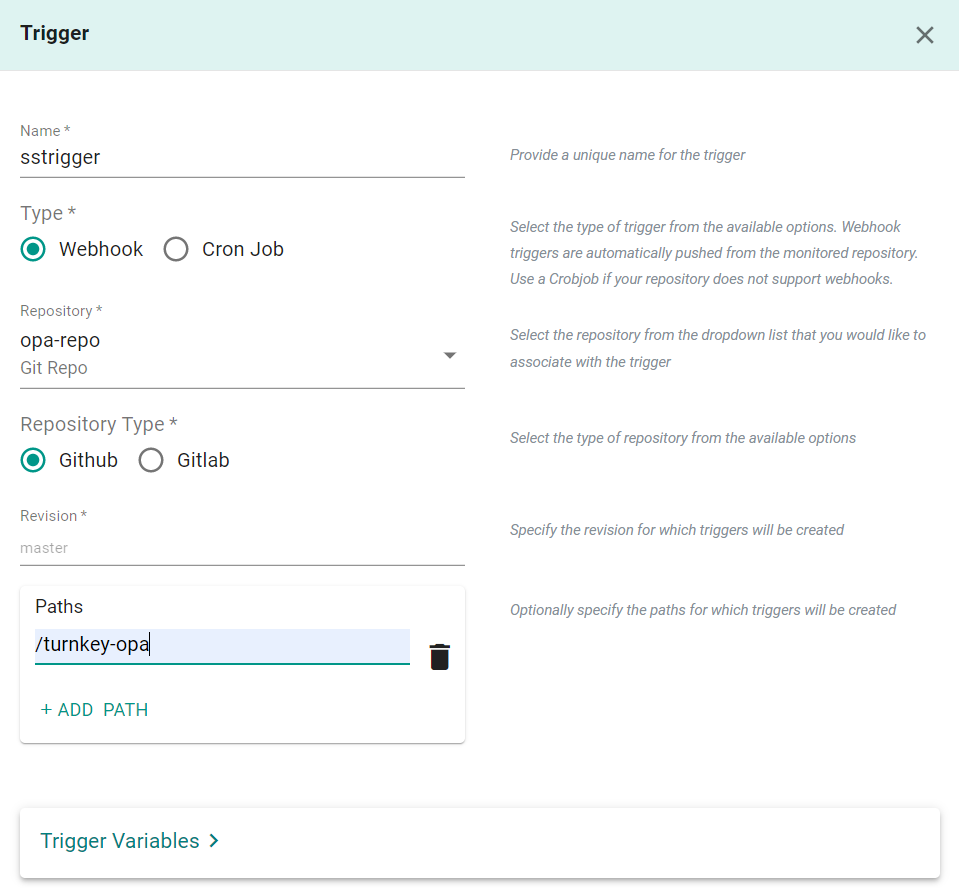
- Provide a name for the trigger
- Select "Webhook" for type
- Select the repository that we created previously
- Select "Github" for Repository Type
- Enter "main" for revision
- Click "Add Path"
- Enter "/turnkey-opa" for the path
- Click "Save"
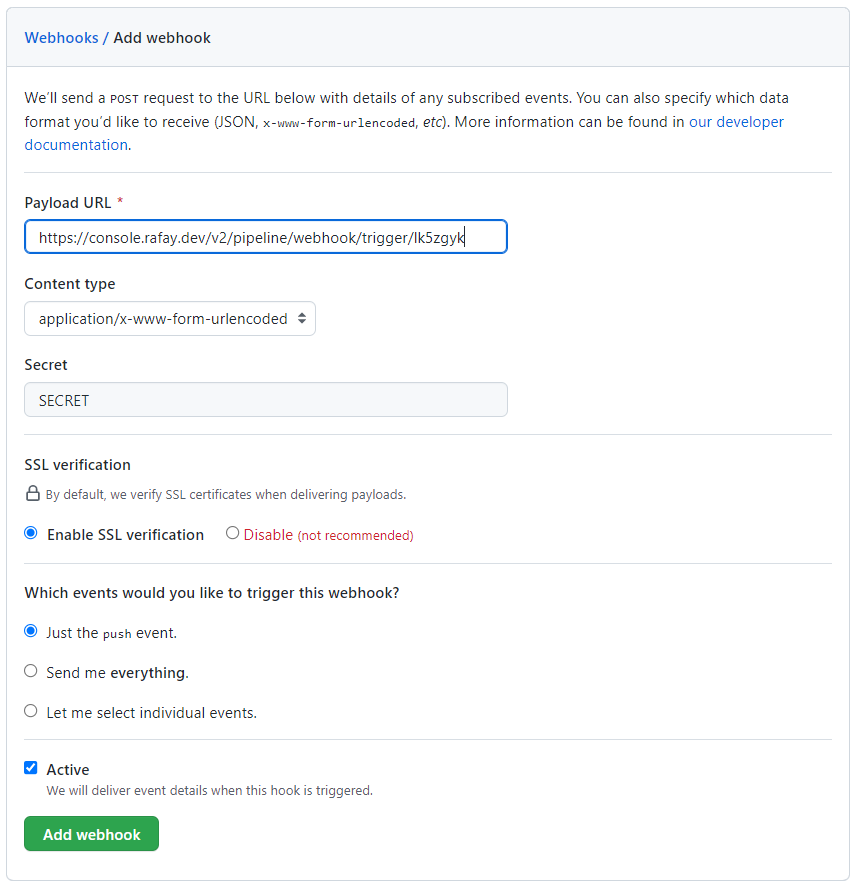
You will now be presented with the webhook configuration details that you need to copy/paste to your GitHub repository. Once you complete this step, the GitOps pipeline will be configured to receive webhook notifications whenever the repository is updated in Git.
Webhook in GitHub¶
- Navigate to your GitHub repository -> Settings -> Webhooks
- Click "Add webhook"
- Copy and Paste the "Payload URL" and "Secret" from the previous step
- Click "Add webhook"
Activate Pipeline¶
By default, newly created pipelines start life in a deactivated state.
- Click "Activate" to activate pipeline
Step 5: Create OPA Resources¶
In this step, we will update the OPA spec files as needed in the Git repository, commit the change and then witness the OPA resources being created automatically in the system.
- Navigate to "turnkey-opa/opapolicies/bp-all.yaml" in your Git Repo
- Edit the file
- Add the following comment to the bottom of the file
### This is a comment
- Commit the change to the file once the comment has been added
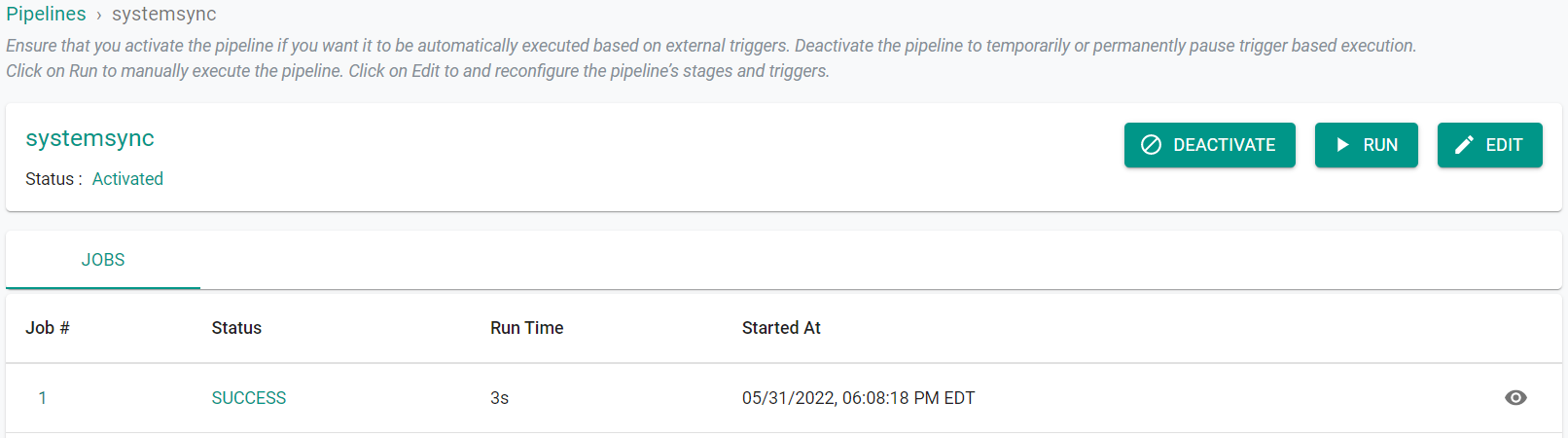
The commit will trigger the GitOps pipeline and it will automatically create the OPA resources defined in the Git repository.
- Navigate to GitOps -> Pipelines in the console to see that a second job in the pipeline was initiated. This job was triggered via a GitHub webhook when we commited the update to the YAML file.
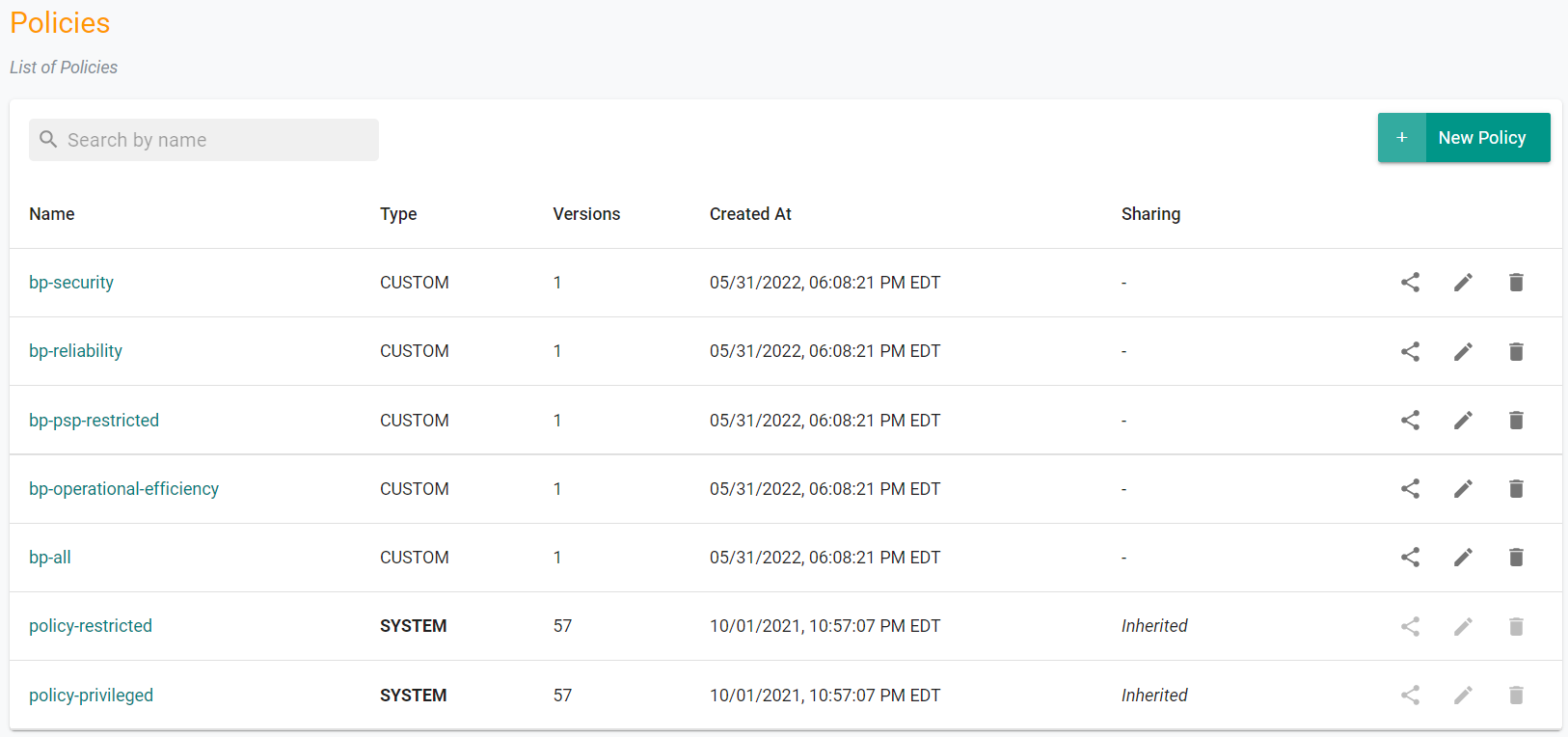
Once the pipeline job has completed, we can view the OPA policies that were created. You should see five new "Custom" policies.
- Navigate to OPA Gatekeeper -> Policies
 ¶
¶
Recap¶
In this part, you successfully configured a GitOps pipeline with Sytem Sync to create the turnkey OPA resources. You are now ready to move to subsequent parts of the exercise to use the OPA policies in blueprints and test the OPA constraints on your cluster.