Create
In this part, you will
- Configure and provision an Amazon EKS Cluster
- Create Secrets Store CSI Driver and ASCP addon.
- Create a custom cluster blueprint with the newly created addons.
- Apply the custom cluster blueprint to your EKS cluster.
Step 1: Configure RCTL¶
This step is a one-time task. In this step, you will download the RCTL CLI so that you can interact with your Org programmatically and embed all operations in your existing automation platform.
- Login into your Org and click on My Tools
- Download the RCTL CLI binary for your operating system and install it on a node from which you can perform Kubectl operations to your EKS-A cluster.
- Download the CLI config and initialize the RCTL CLI with the config file
./rctl config init <full path to config file>
Optionally, check if RCTL is properly configured and can interact with your Org. You should see an output similar to the example below.
./rctl get projects
NAME
defaultproject
Step 2: Provision EKS cluster¶
This step assumes the following:
- You have already created "cloud credentials" in the "default project".
- You have configured the RCTL CLI to interact with "default project".
In the example below, you will provision an Amazon EKS cluster in the "default project" with "one managed nodegroup" using the cluster specification provided below.
| Type | Description |
|---|---|
| Cluster Name | aws-sm-demo |
| Project | default |
| Blueprint | default |
| k8s Version | 1.20 |
| AWS Region | us-west-1 |
| Worker Nodes | 2 |
| Node Group Type | Managed |
kind: Cluster
metadata:
name: aws-sm-demo
project: defaultproject
spec:
type: eks
cloudprovider: demo-aws-full-role
blueprint: default
---
apiVersion: rafay.io/v1alpha5
kind: ClusterConfig
metadata:
name: aws-sm-demo
region: us-west-1
version: "1.20"
managedNodeGroups:
- name: managed-ng1
instanceType: t3.large
desiredCapacity: 2
- Copy the cluster specification and save it to a YAML file (e.g "aws-sm-demo.yaml")
- Use the RCTL CLI to provision the EKS cluster in your project
./rctl apply -f "aws-sm-demo.yaml"
This will start the provisioning of an EKS cluster in the project. This step can take ~10-15 minutes to complete. Once provisioning is successful, you should be able to interact with your EKS cluster in your Project.
Step 3: Cluster Blueprint¶
In this step, you will:
- Create and configure a a repository to dynamically pull the desired version of the Secrets Store CSI Driver Helm chart.
- Create a Secrets Store CSI Driver addon allowing you to make secrets stored in AWS Secrets Manager appear as files mounted in K8s pods. Additional functionality such as secret sync and secret rotation has recently been added.
- Create a Secrets Manager and Config Provider(ASCP) addon which allows organizations that are utilizing AWS Secrets Manager to have their secrets appear as files mounted in K8s pods.
- Create a custom cluster blueprint with the Secrets Store CSI Driver and ASCP addon.
Add Secrets Store CSI Driver Repo¶
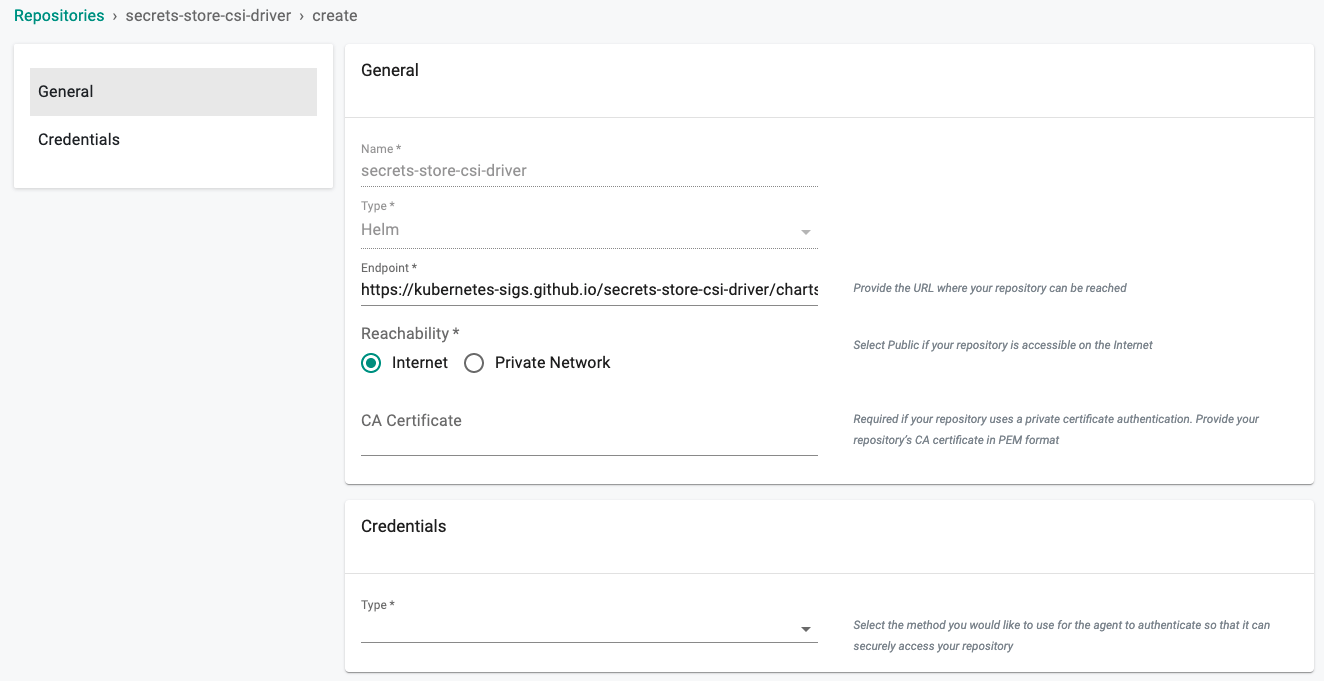
Configure the repo endpoint so that the controller can automatically retrieve the required Helm chart directly from the Internet facing repository.
- Click on Integrations -> Repository.
- Create New Repository -> Provide a name such as "secrets-store-csi-driver" and Select "Helm" for Type.
- Enter "https://kubernetes-sigs.github.io/secrets-store-csi-driver/charts" for Endpoint and Select "Internet Facing" for Reachability.
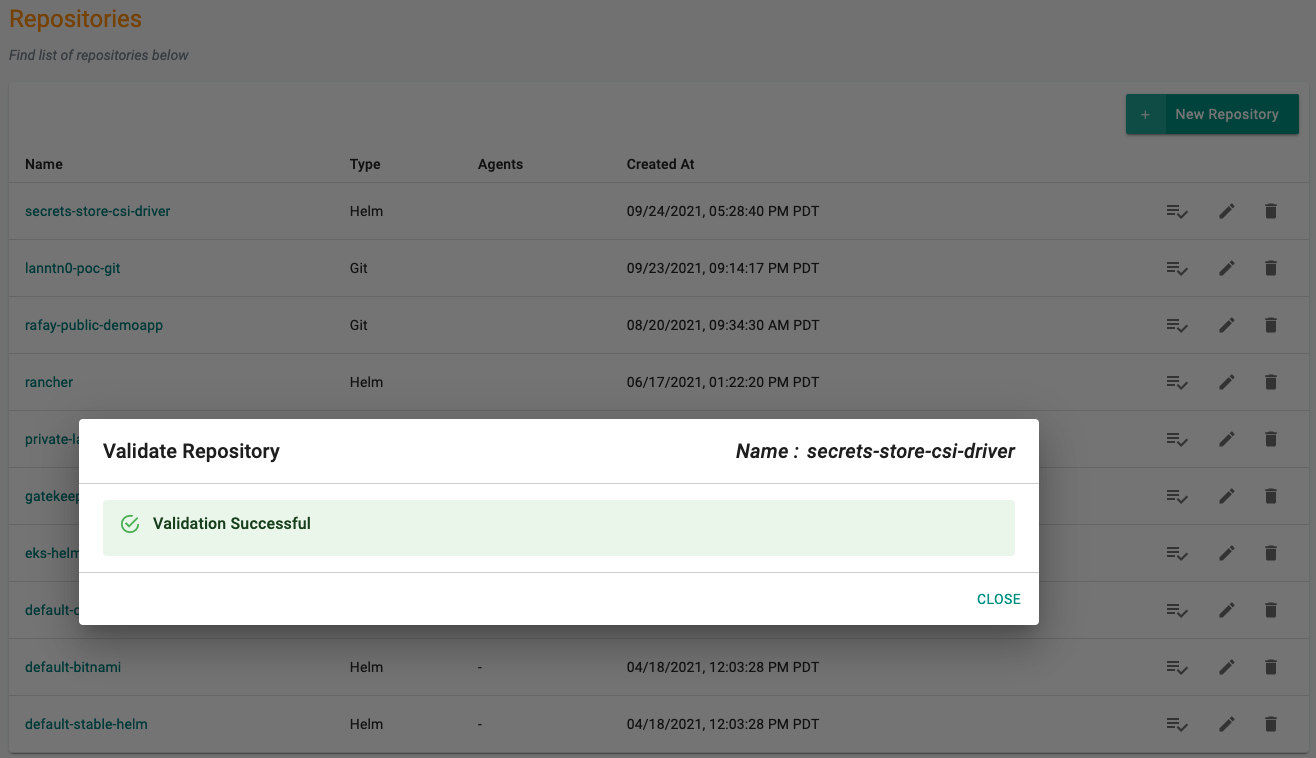
- Optionally, you can validate the correct configuration of the repository by clicking on the validate option.
Create Namespace¶
- Click on Infrastructure -> Namespaces
- Click New Namespace
- Enter "kube-system" in the "Name" section
- For "Type" Select "Wizard" from the dropdown
- Click "SAVE"
Create Secrets Store CSI Driver Addon¶
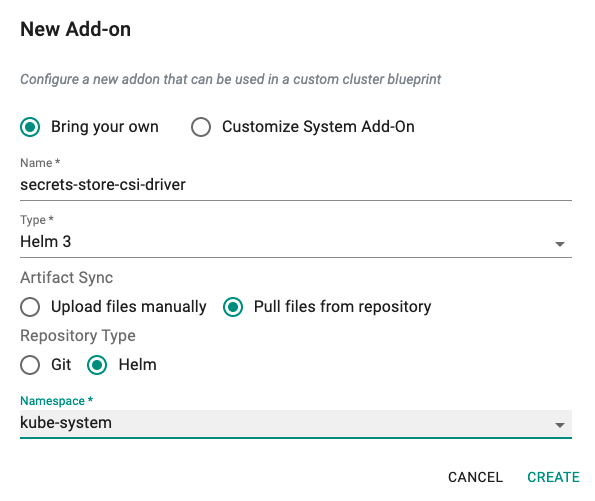
- Click on Infrastructure -> Addons.
- Click on Create New Addon with the name "secrets-store-csi-driver".
- Select "Helm3" for addon type.
- Select "Pull files from repository" for Artifact Sync.
- Select repository type as "helm".
- Select the "kube-system" namespace from the dropdown.
Custom Values¶
The Secrets Store CSI Driver supports many functions such as support for secret rotation and K8s secret sync that can be enabled in an overrides file. To enable secret sync the following parameter should be set in the override file and uploaded to the addon. Save the following override in a "secrets-store-csi-driver-values.yaml" file.
syncSecret:
enabled: true
New Secrets Store CSI Driver Addon Version¶
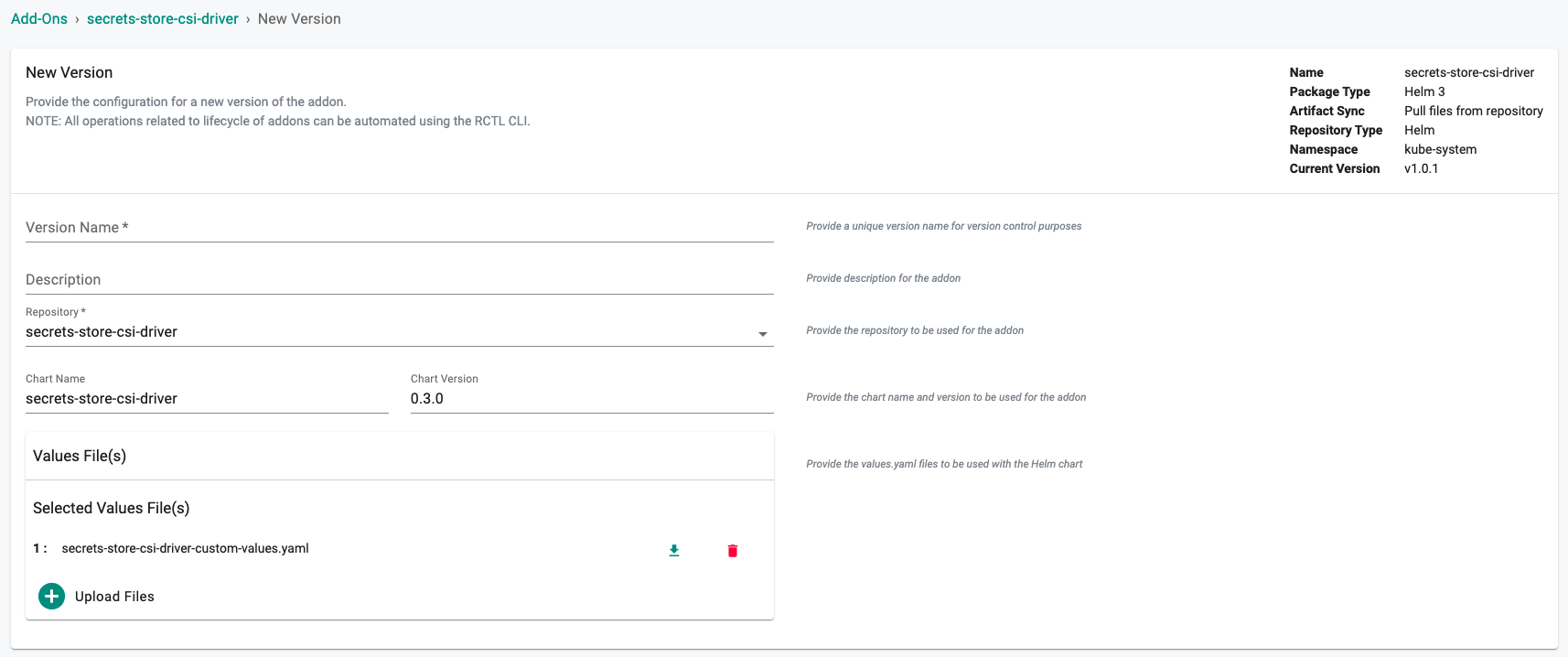
- Click on "New Version" to create a new version of the secrets store csi driver addon.
- Provide a version (e.g. v1).
- Select the "secrets-store-csi-driver" repository.
- Enter "secrets-store-csi-driver" for the Chart Name.
- Enter "0.3.0" for the version number.
- Select "Upload Files" and select the file created above if the plan is to sync secrets pulled from AWS Secrets Manager to Kubernetes Secrets or enabling support for additional functionality.
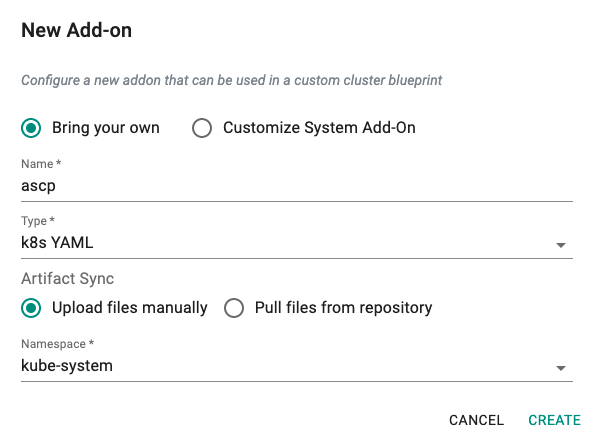
Create ASCP Addon¶
- Download the K8S YAML manifest from the Git repo.
wget https://raw.githubusercontent.com/aws/secrets-store-csi-driver-provider-aws/main/deployment/aws-provider-installer.yaml
- Click on Infrastructure -> Addons.
- Click on Create New Addon with the name "ascp".
- Select "K8s YAML" for addon type.
- Select "Upload files manually" for Artifact Sync.
- Select the "kube-system" namespace from the dropdown.
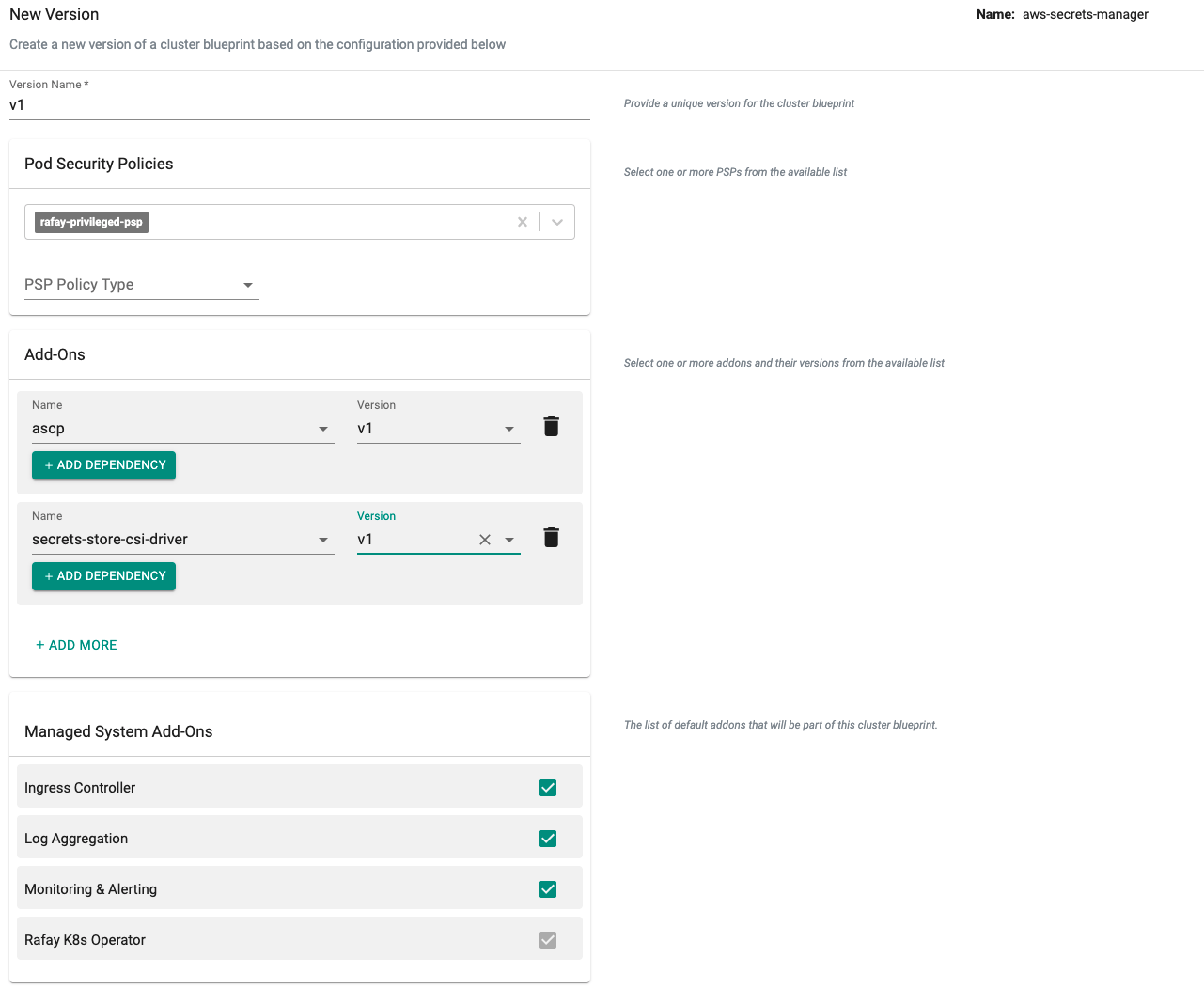
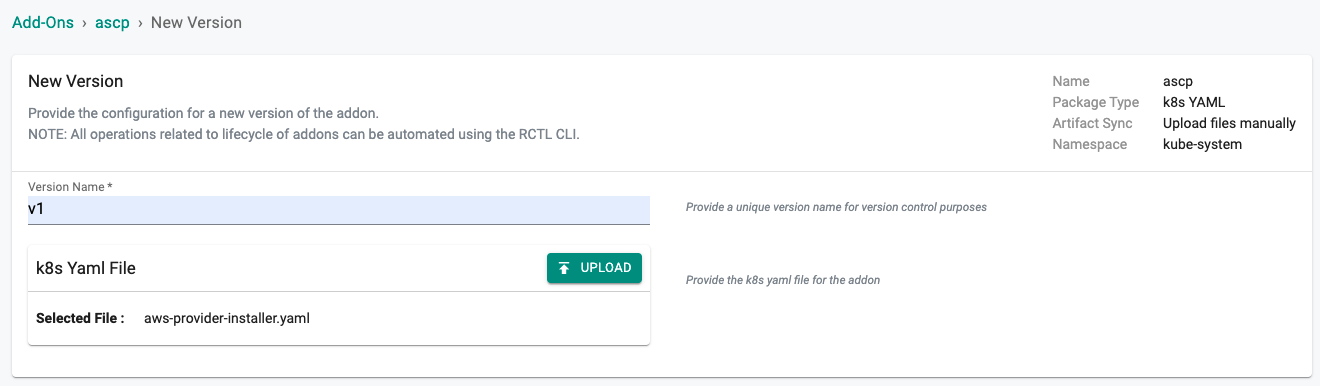
New ASCP Addon Version¶
- Click on "New Version" to create a new version of the ascp addon.
- Provide a version (e.g. v1).
- Select the file "aws-provider-installer.yaml" downloaded in the previous step.
 ¶
¶
New Blueprint¶
- Select blueprints and create a new blueprint (e.g. aws-secrets-manager).
- Click on "New version" (e.g. v1).
- Select the "ascp" and "secrets-store-csi-driver" addon and "version" from the list of custom addons.
- Save blueprint.
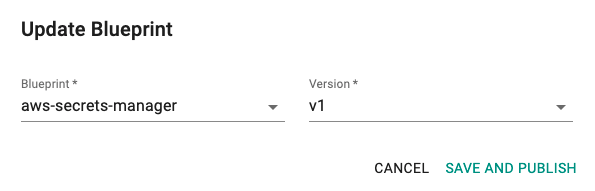
Step 4: Apply Blueprint¶
Now, we are ready to apply the newly created, custom blueprint to our EKS cluster.
- Select Infrastructure -> Clusters.
- Click on the gear icon on the far right of the EKS cluster.
- Update blueprint and select the new blueprint and version.
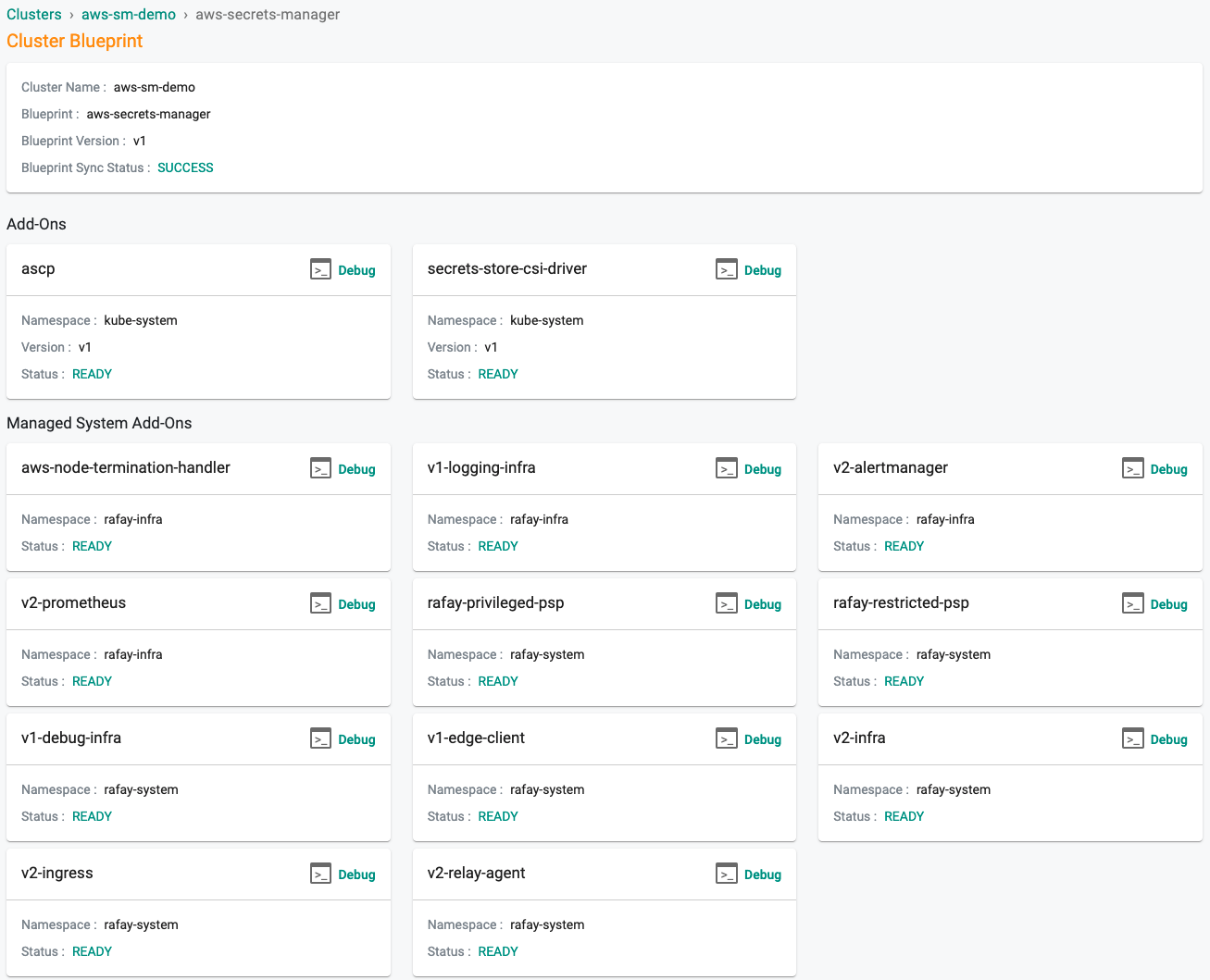
In a few minutes, all the k8s resources matching the custom cluster blueprint will become operational on the cluster.
Notice that the cluster's blueprint name and version match what you created in the prior step.
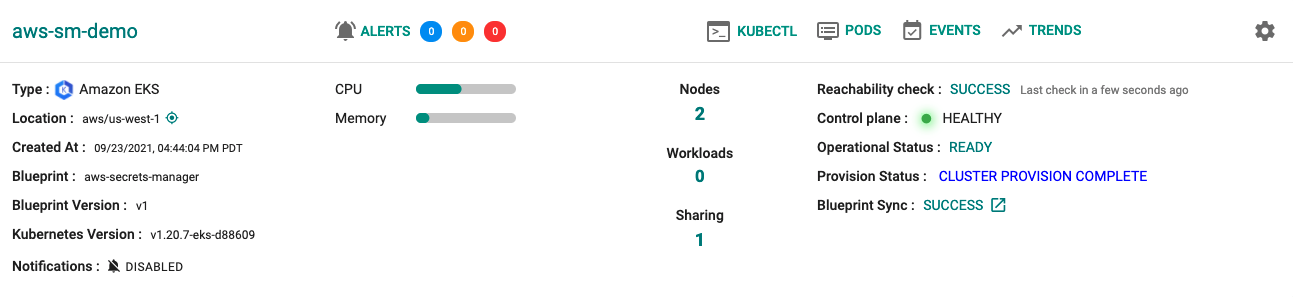
Step 5: Verify Setup¶
Optionally, to verify if the Secrets Store CSI Driver and ASCP addon have been properly deployed you can do the following:
- Click on the EKS cluster.
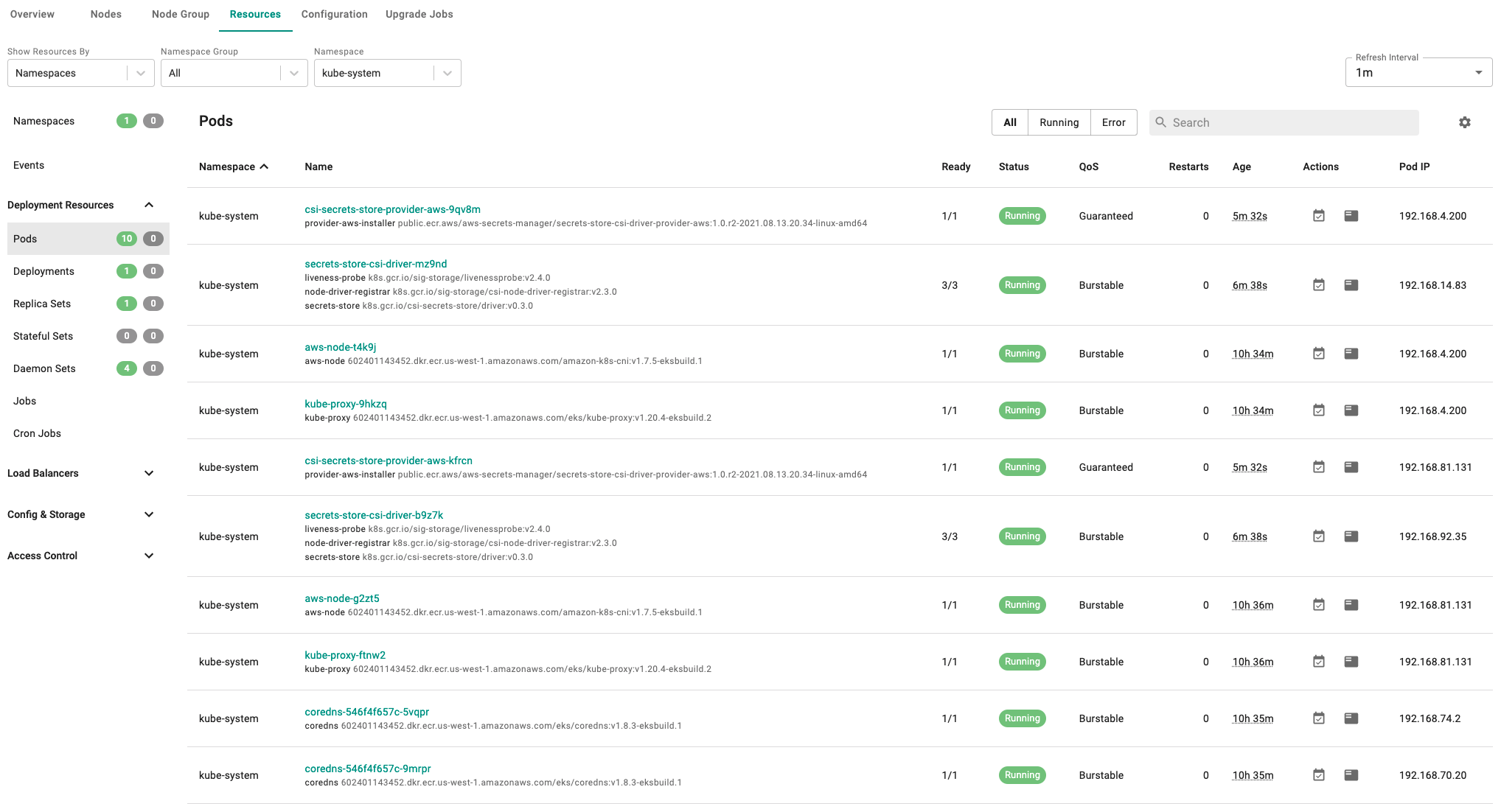
- Select Resources to view the integrated k8s dashboard.
- Select "pods" from the resource selector and filter by the "kube-system" namespace.
- Verify all pods are in a running state.
Next Steps¶
You are now ready to move on to the second part of the recipe.