RBAC based KubeCTL
The Controller supports two approaches for users to access a managed cluster's Kube API Server using tools like KubeCTL etc.
Zero Trust Access Proxy¶
The Controller implements a kube api server proxy that provides users with a zero trust access to the managed cluster's API server without the need for SSH, VPNs or Bastions.
Users can access the cluster's api server via
- Browser based KubeCTL Shell
- Download Kubeconfig and use with KubeCTL CLI
With this access model, user authentication is performed at the Rafay access proxy (local or IdP based) with authorization performed transparently based on the user's configured role or group membership.
As a result, user and role management can be centralized for all types of clusters i.e. there is no need to manage user lifecycle in AWS IAM.
Download Kubeconfig¶
Use this approach if you would like to download the Kubernetes config (kubeconfig) for the Rafay provisioned Amazon EKS Cluster and access it "directly" (instead of the access proxy)
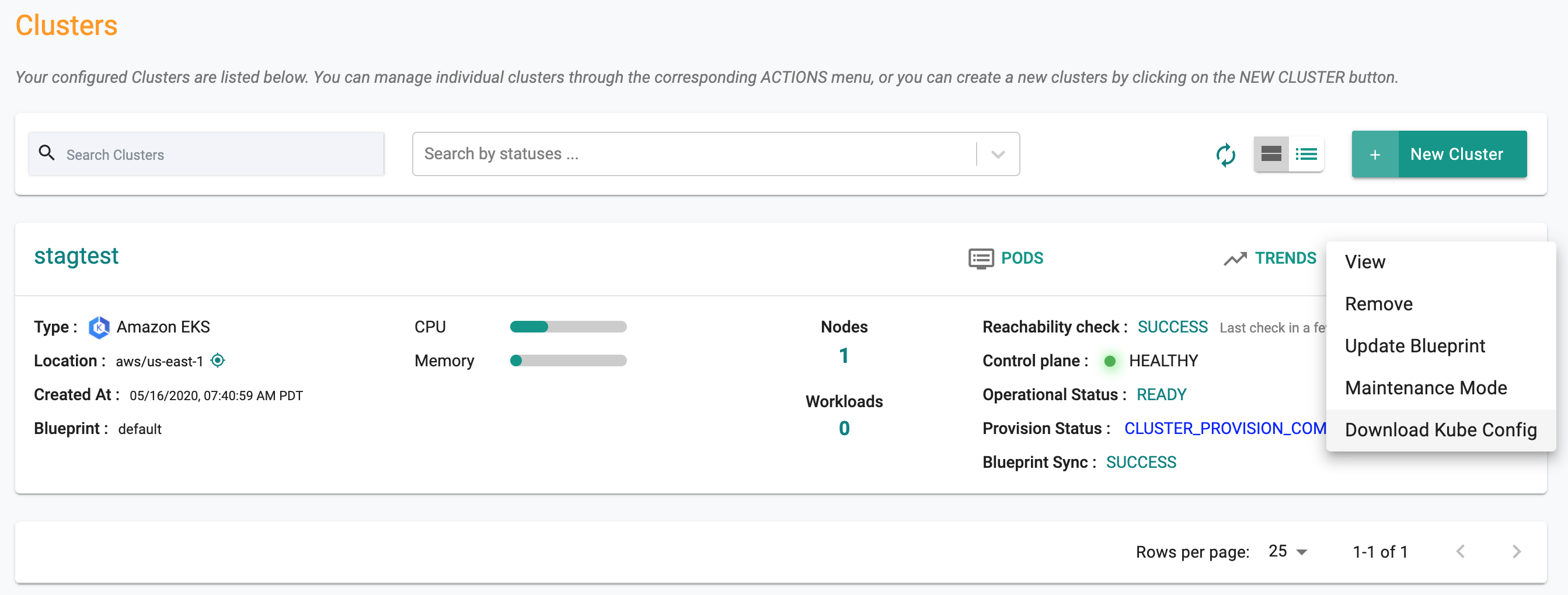
- Click on Options (gear next to the cluster)
- Select "Download Kube Config"
This provides a kubeconfig meant for cluster admins.
User ARN¶
For Amazon EKS Clusters provisioned using a delegated IAM Role, an additional step is required before "end users" are allowed Kubectl access to the EKS clusters.
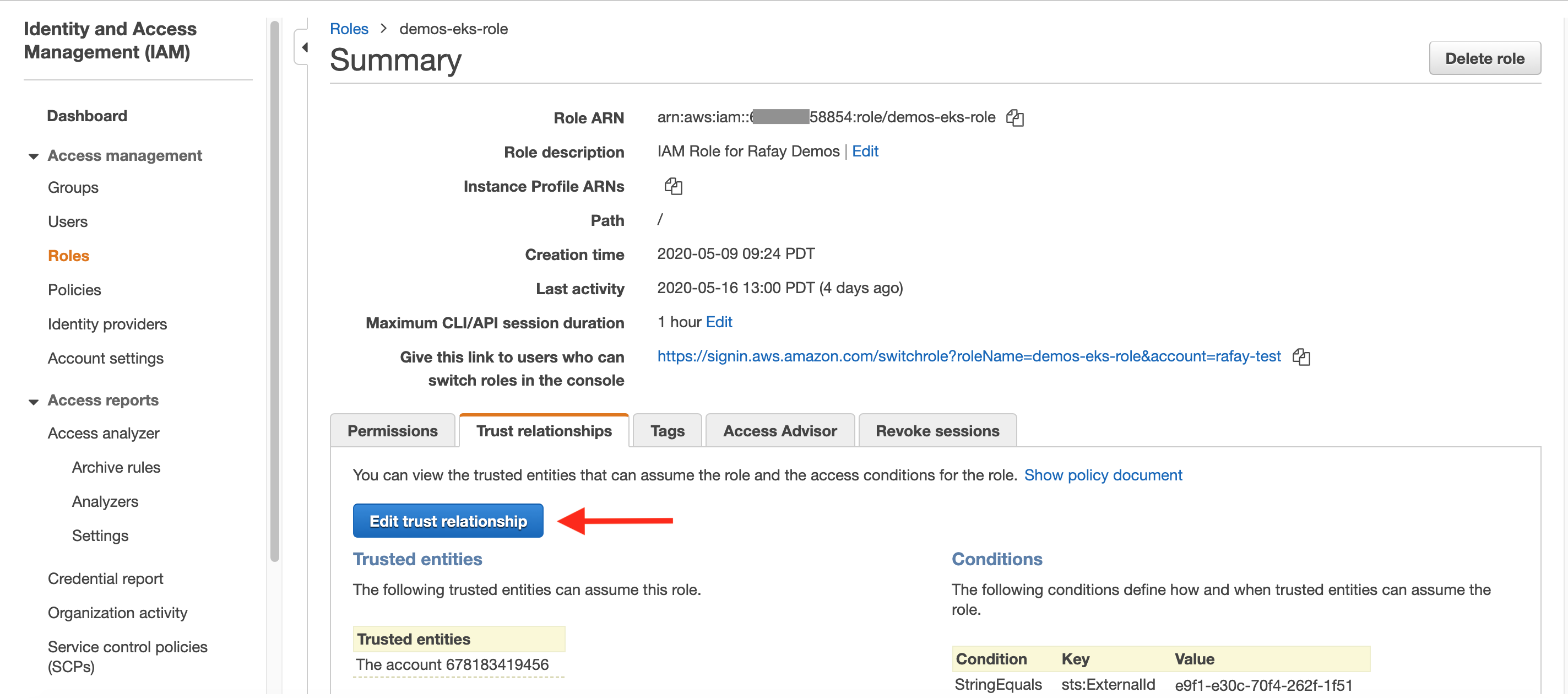
- Select the IAM Role used to provision the cluster
- Click on "Edit Trust Relationship
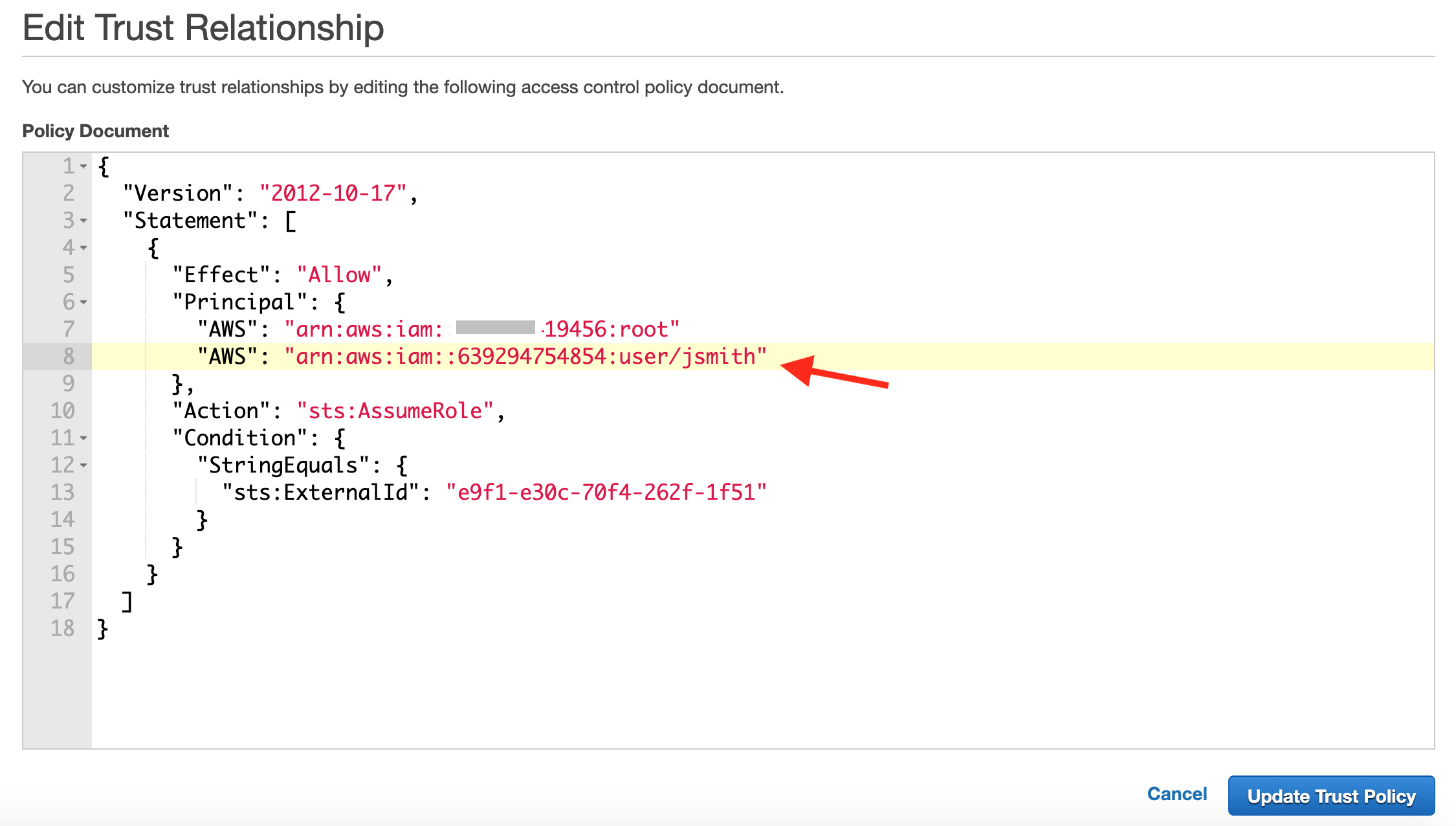
- In the Policy Document, update the "Principal" section with the IAM user's ARN details for the user that needs access to the cluster. In the example below, we have added the ARN for the AWS IAM User "jsmith" details to the Principal.