Policies
Policies can contain one or more constraint(s) and are deployed to clusters through a blueprint. Multiple policies can be created with different constraints as required.
Important
Org Admin or Infra Admin role is required to create and assign OPA Gatekeeper policies
Create New Policy¶
Perform the below steps to create a new policy:
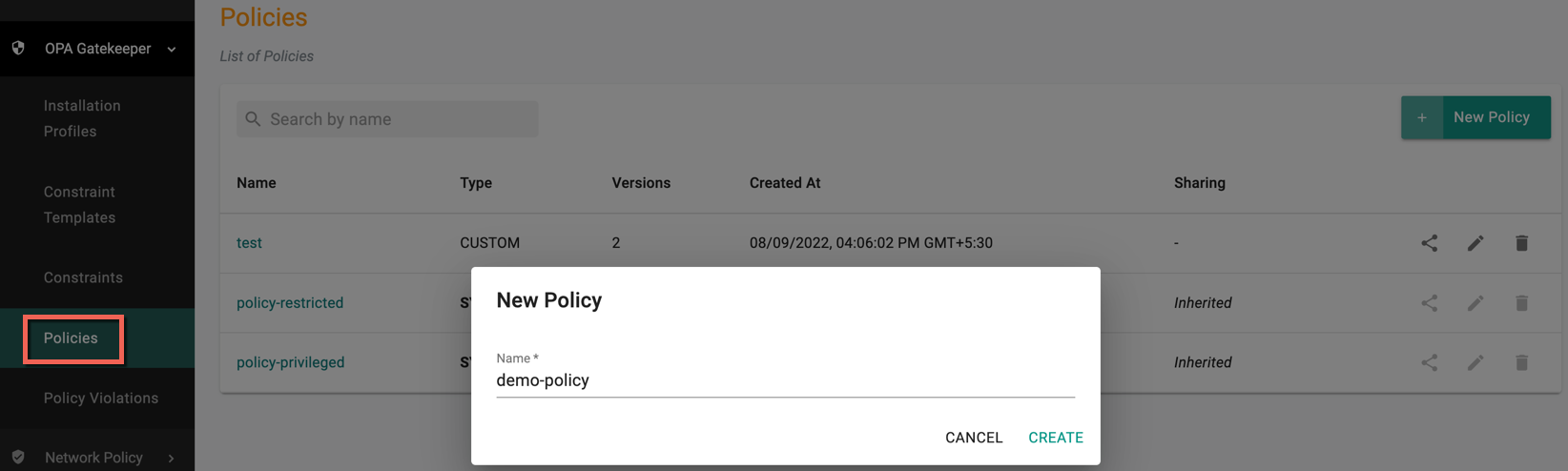
- Login to the Controller and select Policies under the OPA Gatekeeper. Users can view the list of existing policies on the Policies main page
- Click New Policy
- Provide a name for the policy and click Create
Policy New Version¶
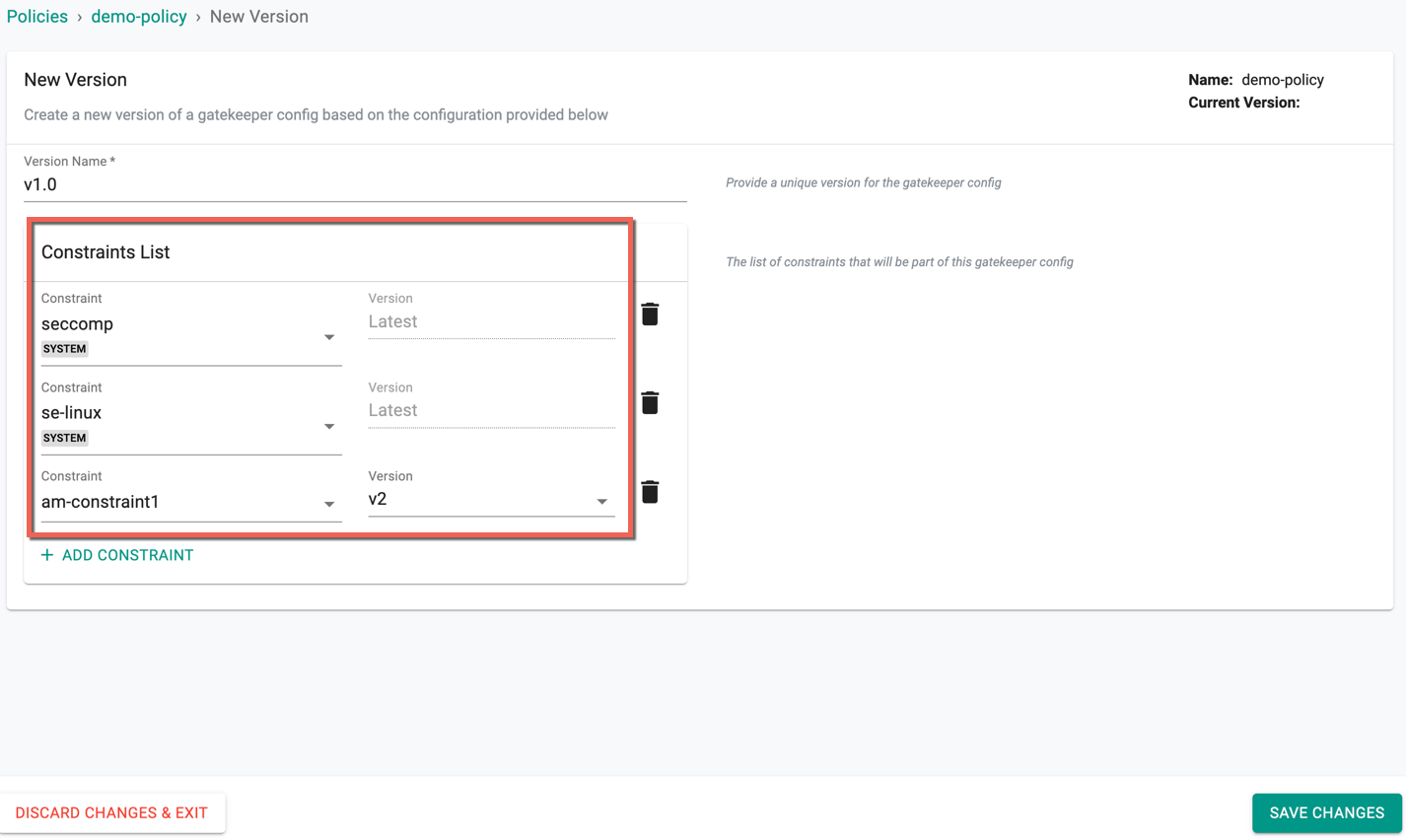
Perform the below steps in the New Version page
- Provide a version name
Constraints List
-
Click Add Constraint to add one or more constraints to this policy
-
On selecting a system constraint, the version is always the latest
- On selecting a custom constraint, user can select the required version from the drop-down
- Click Save Changes to proceed or Discard Changes & Exit to abort the process
Important
Prior to introduction of Installation Profiles, configuration of installation related parameters was through a Policy. Any existing policies (that include installation parameters) will be separated out into a policy and a corresponding installation profile (with a prefix of initial in the profile name)
Assigning Policies¶
OPA Gatekeeper Policies are applied to clusters via blueprint.
Adding/Removing Policies To/From Blueprints¶
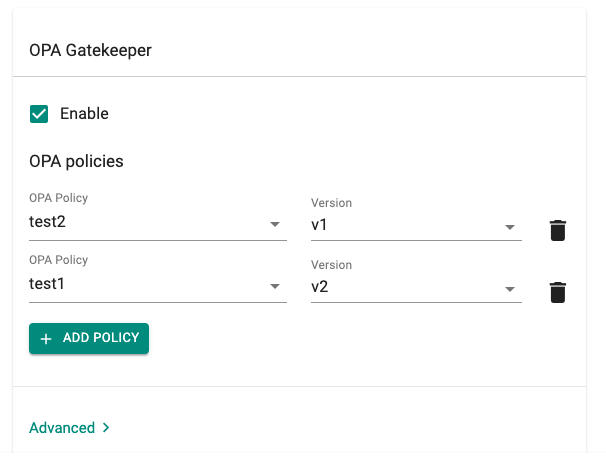
- Under Infrastructure, navigate to Blueprints.
- Navigate to the OPA Gatekeeper section and enable it
- Click Add Policy and add OPA Gatekeeper policies with the corresponding version, multiple OPA Gatekeeper policies can be added to a blueprint
- Click Save Changes
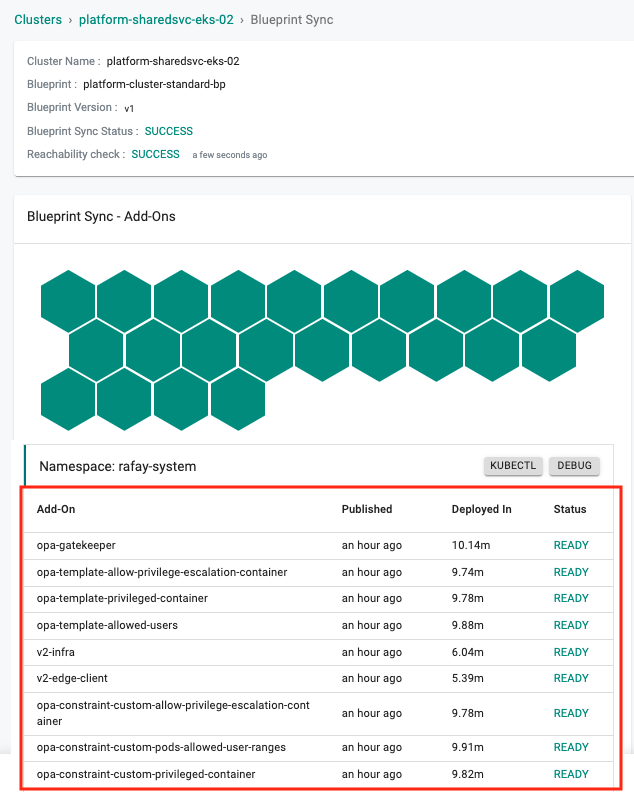
Blueprint sync¶
On a blueprint sync operation, Constraint Templates/Constraints (based on configured policies) and the necessary OPA Gatekeeper components are deployed to the cluster.