Installation Profiles
Installation Profiles allows the users to pass the installation parameters for OPA Gatekeeper. The Installation Profiles page shows custom and default profiles. A default installation profile is provided that can be leveraged out of box. In cases where installation profiles need to be customized, a custom installation profile can be created.
Create a Custom Installation Profile¶
Perform the below steps to create a custom installation profile:
- Login to the Controller and select Installation Profiles under OPA Gatekeeper
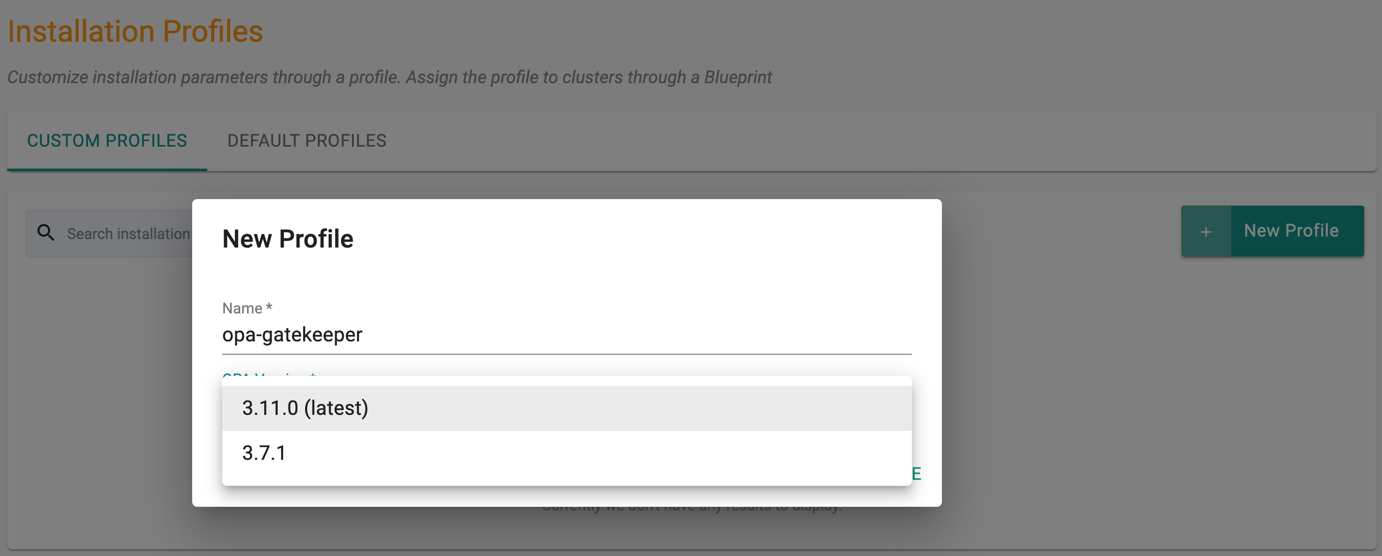
- Under the Custom Profiles tab, click New Profile
- Provide a name for the profile
- Select an OPA Version (latest version 3.16.3)
- Click Create
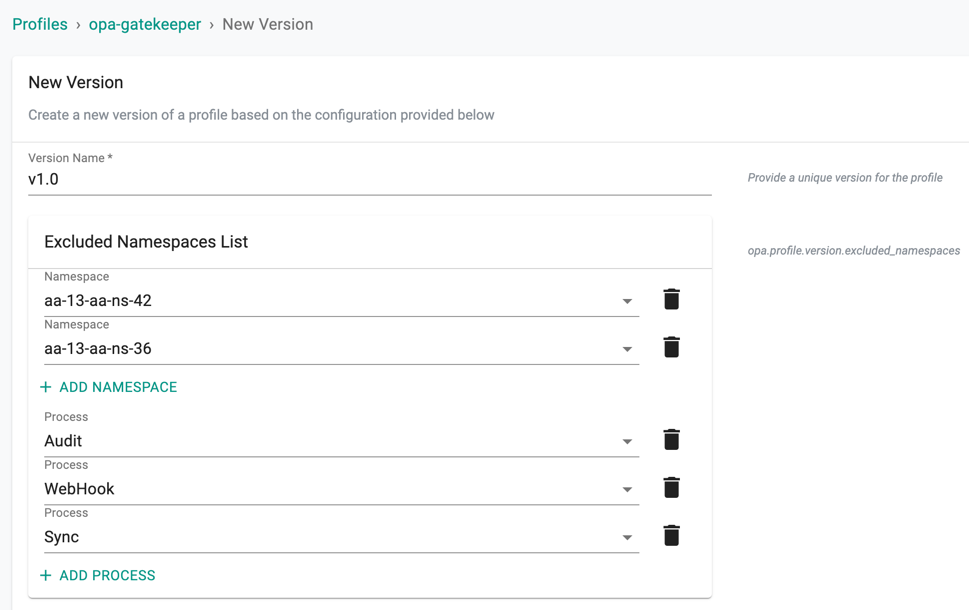
- Provide a version name
Excluded Namespaces and Process
Users are allowed to exclude the namespace(s) and process associated with the selected namespace from evaluation
- Click Add Namespace to exclude one or more namespace(s) from evaluation
- Click Add Process to exclude one or more process(s). Audit process exclusion will exclude resources from specified namespace(s) in audit results. WebHook process exclusion will exclude resources from specified namespace(s) from the admission webhook. Sync process exclusion will exclude resources from specified namespace(s) from being synced into OPA. All would include all of the process exclusions
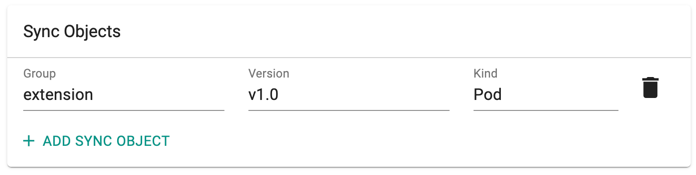
Sync Objects
Sync Objects allows to sync data into OPA. Kubernetes data can be replicated into OPA via the sync config resource.
- Click Add Sync Object to add group, version and kind
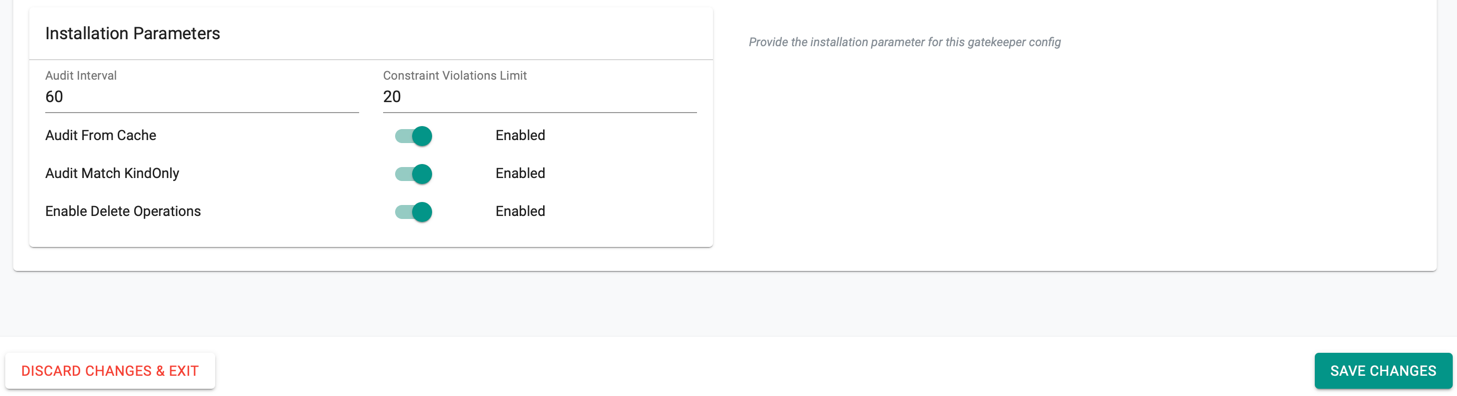
Installation Parameters
-
Set the Audit interval and Constraint Violation Limit. This audit functionality enables periodic evaluations of resources to detect pre-existing misconfigurations. The default value of Audit Interval is 60 seconds and Constraint Violations Limit is 20.
-
Enable Audit from Cache to rely on OPA cache as the source-of-truth for audit queries
Note: This requires replication of Kubernetes resources into OPA before they can be evaluated against the enforced policies
-
If all of the constraints match against specific kinds (example: match only pods), enable Audit Match KindOnly to speed up audit runs. This will only check resources of the kinds specified in the constraints associated with the policy
-
A few non-compliant deletes may happen despite the policy. Enable Enable Delete Operations to audit the non-compliant deletes performed through Gatekeeper's admission webhook
- Click Save Changes
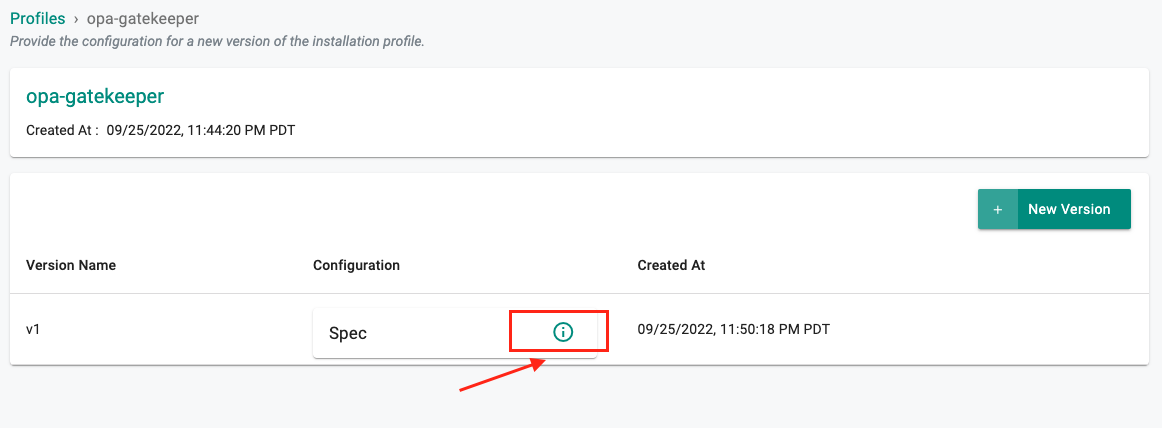
New versions of the profile can be created by clicking New Version and going through the same workflow as above. Parameters for the installation profile can be viewed by clicking the info button under Configuration next to Spec.
Using a Custom Installation Profile¶
Custom Installation Profiles can be selected as part of enabling OPA Gatekeeper when creating or updating a blueprint.
- Go to the OPA Gatekeeper section to enable the capability
- Expand Advanced section, select the installation profile and the version
OPA Version Upgrade/Downgrade¶
The latest version of OPA Gatekeeper 3.16.3.
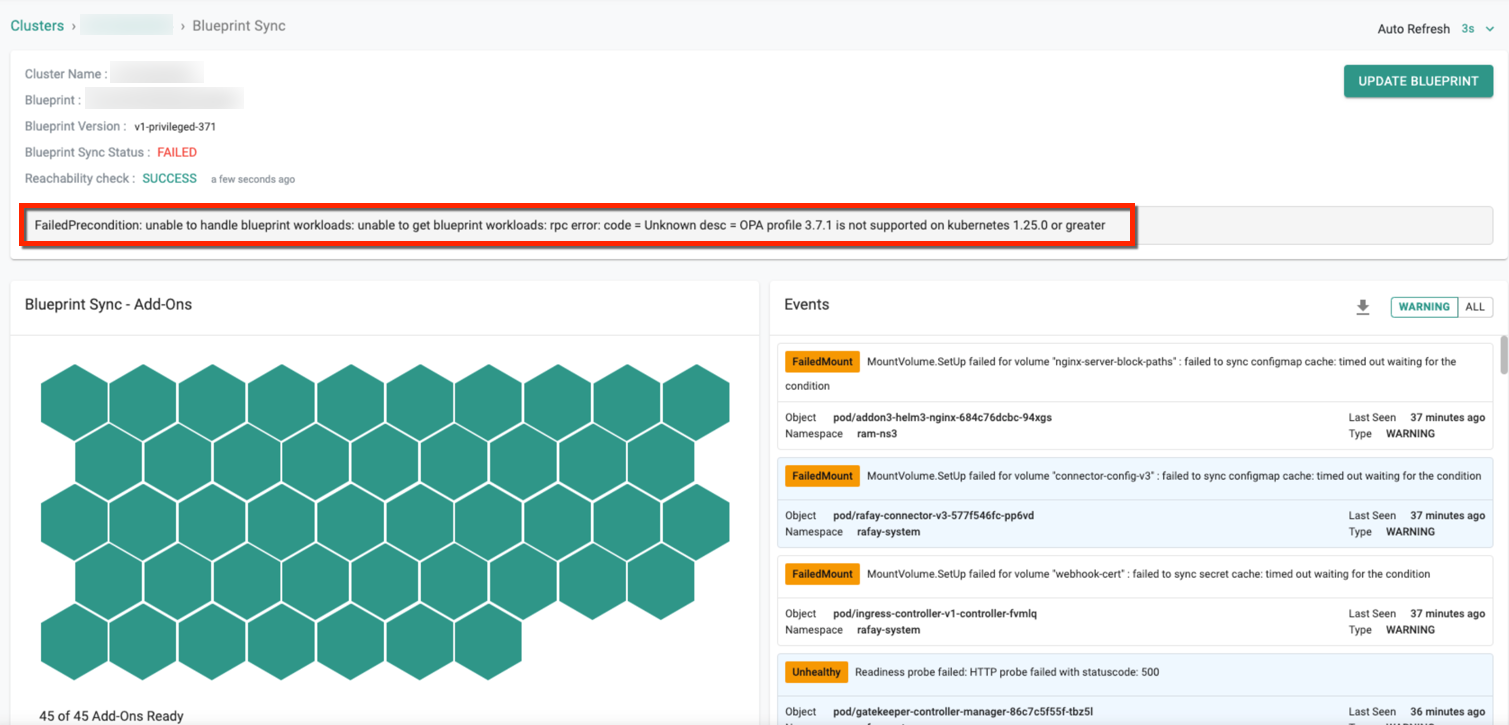
- The older OPA Gatekeeper version (3.7.1) is not supported on K8s v1.25 or later. On installing the older version 3.7.1 on K8s v1.25, the below error message is shown
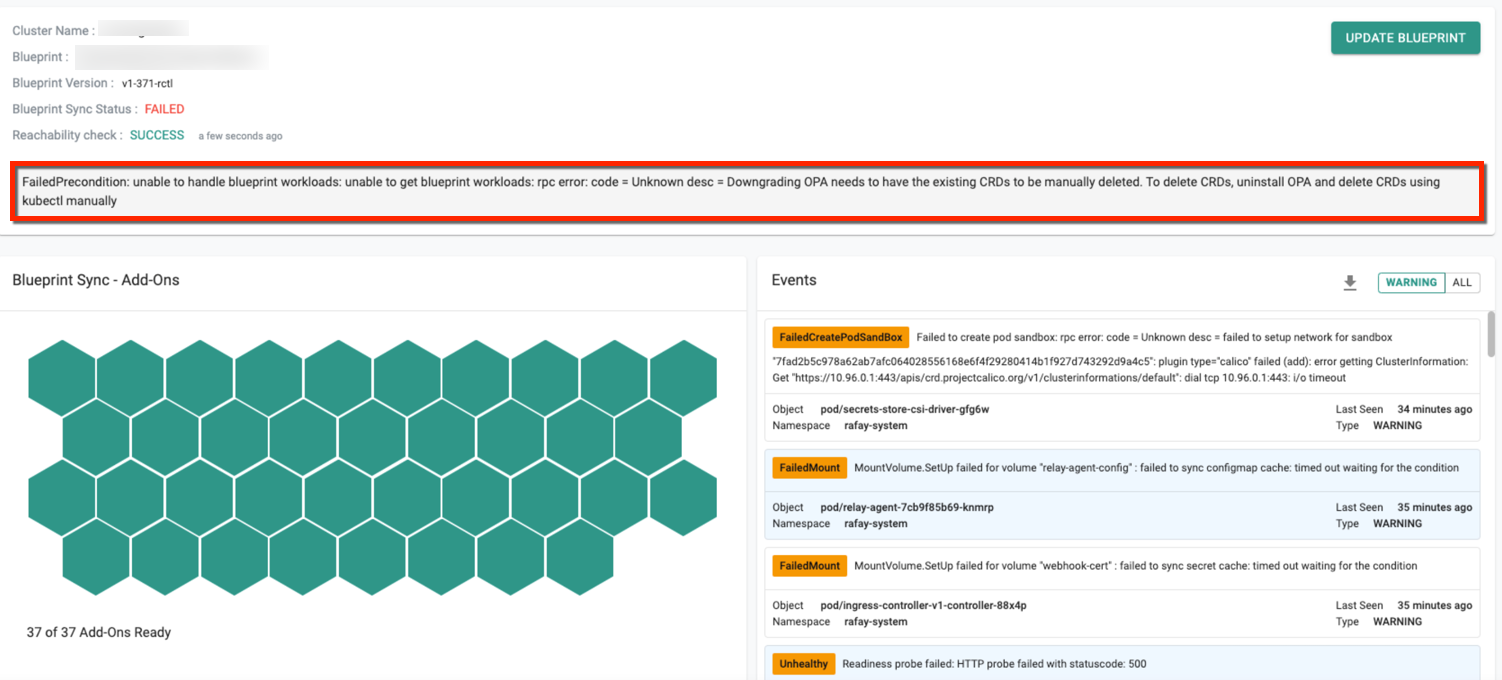
- Upgrading the OPA version from 3.7.1 to 3.11.0 on the older K8s version is supported. While downgrading the OPA version from v3.11.0 to v3.7.1 on older K8s version (lower than K8s v1.25), the below error message appears
As mentioned in the error message, uninstall OPA (remove OPA config from Blueprint), delete CRDs using Kubectl manually and again update the blueprint with OPA v3.7.1. This will successfully downgrade the OPA version
The list of CRDs to be deleted are given below:
- assign.mutations.gatekeeper.sh
- assignmetadata.mutations.gatekeeper.sh
- configs.config.gatekeeper.sh
- constraintpodstatuses.status.gatekeeper.sh
- constrainttemplatepodstatuses.status.gatekeeper.sh
- constrainttemplates.templates.gatekeeper.sh
- expansiontemplate.expansion.gatekeeper.sh
- modifyset.mutations.gatekeeper.sh
- mutatorpodstatuses.status.gatekeeper.sh
- providers.externaldata.gatekeeper.sh