Part 3: Namespaces
What Will You Do¶
In this section you will
- Configure a Kubernetes namespace spec in your project
- Publish this namespace on the OpenShift Cluster
Step 1: Create Namespace¶
- In your project, navigate to Infrastructure -> Namespaces
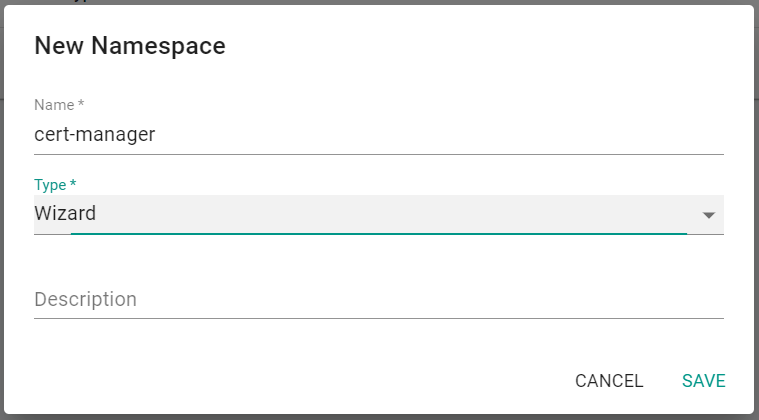
- Click on New Namespace
- Enter cert-manager for name
- Select Wizard for type
- Click Save
Note
In addition to the Namespace wizard, users can also provide the k8s YAML spec for the namespace either by uploading it or point the controller to a Git repo where it can retrieve it.
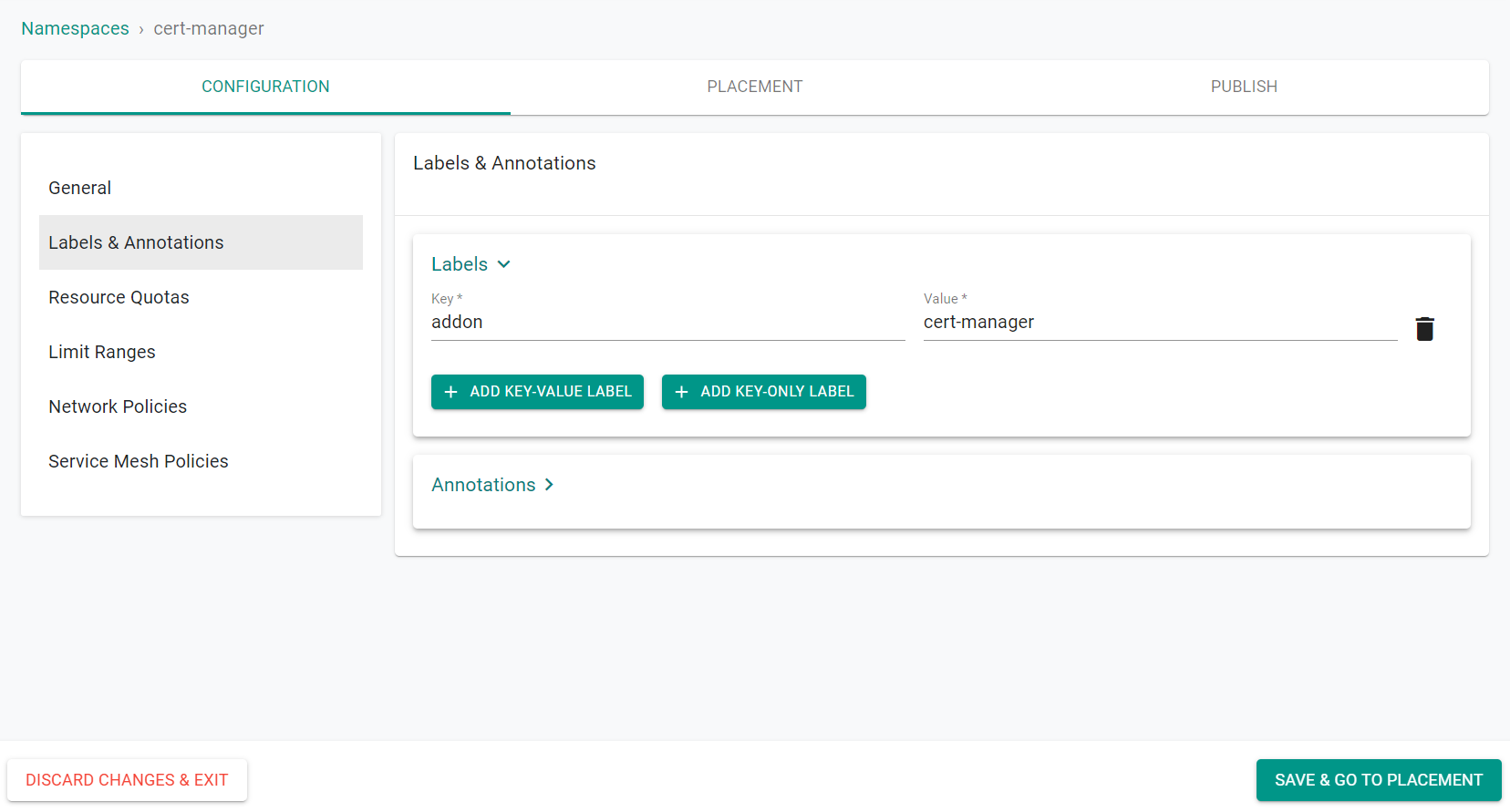
You will be presented with an intuitive wizard that you can use to configure your namespace's requirements. In our case, we want to add labels to our namespace.
- Click Labels & Annotations
- Click Labels
- Click Add Key-Value Label
- Enter addon for the key
- Enter cert-manager for the value
- Click Save & Go To Placement
In the example below, we have entered "key=addon" and "value=cert-manager"
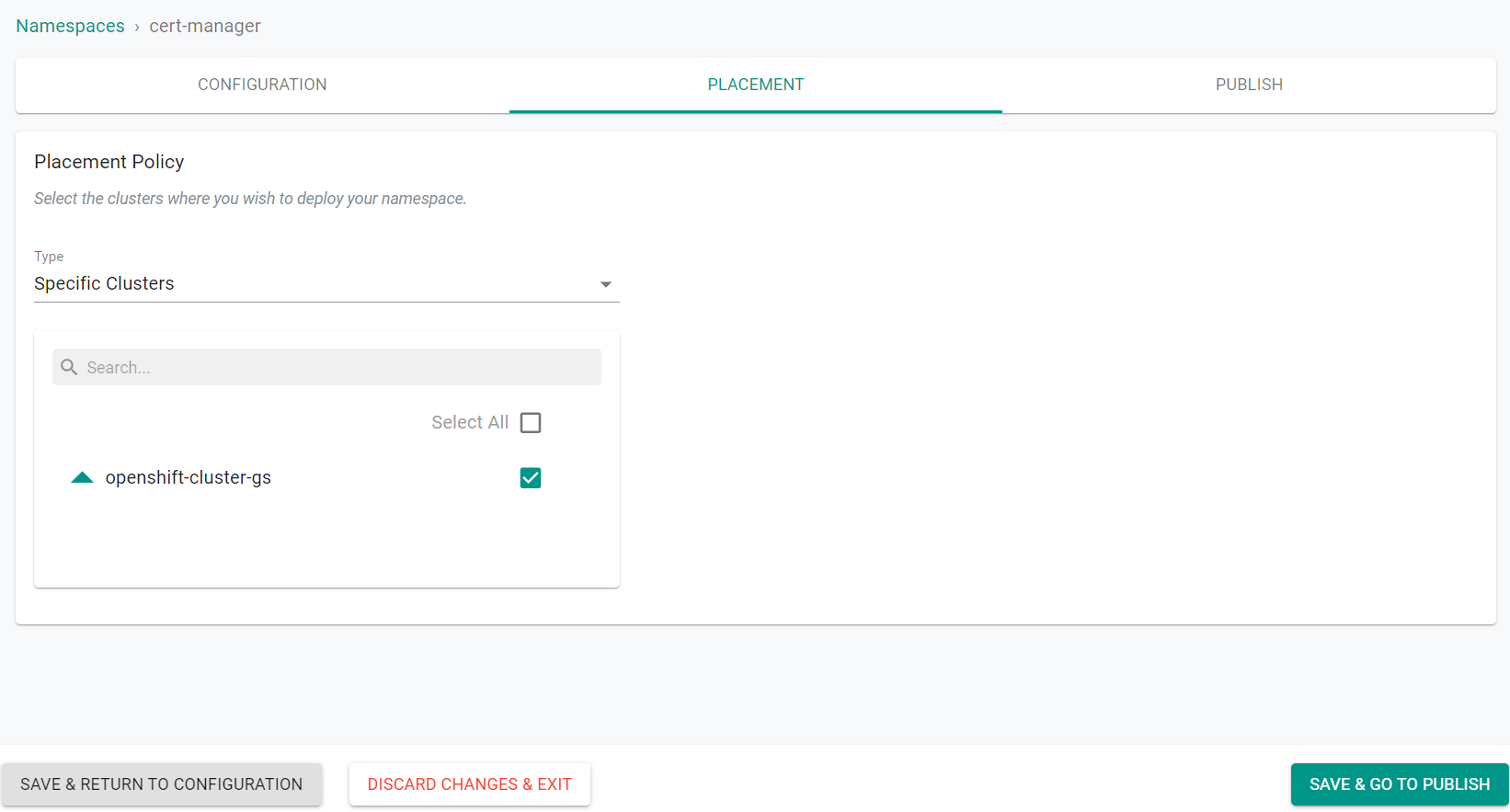
Next, we will select the clusters to deploy the namespace to. Since we only have one cluster in our project for this exercise, we cannot perform multi cluster operations.
- Select Specific Clusters for the placement policy type
- Select your cluster
- Click Save & Go To Publish
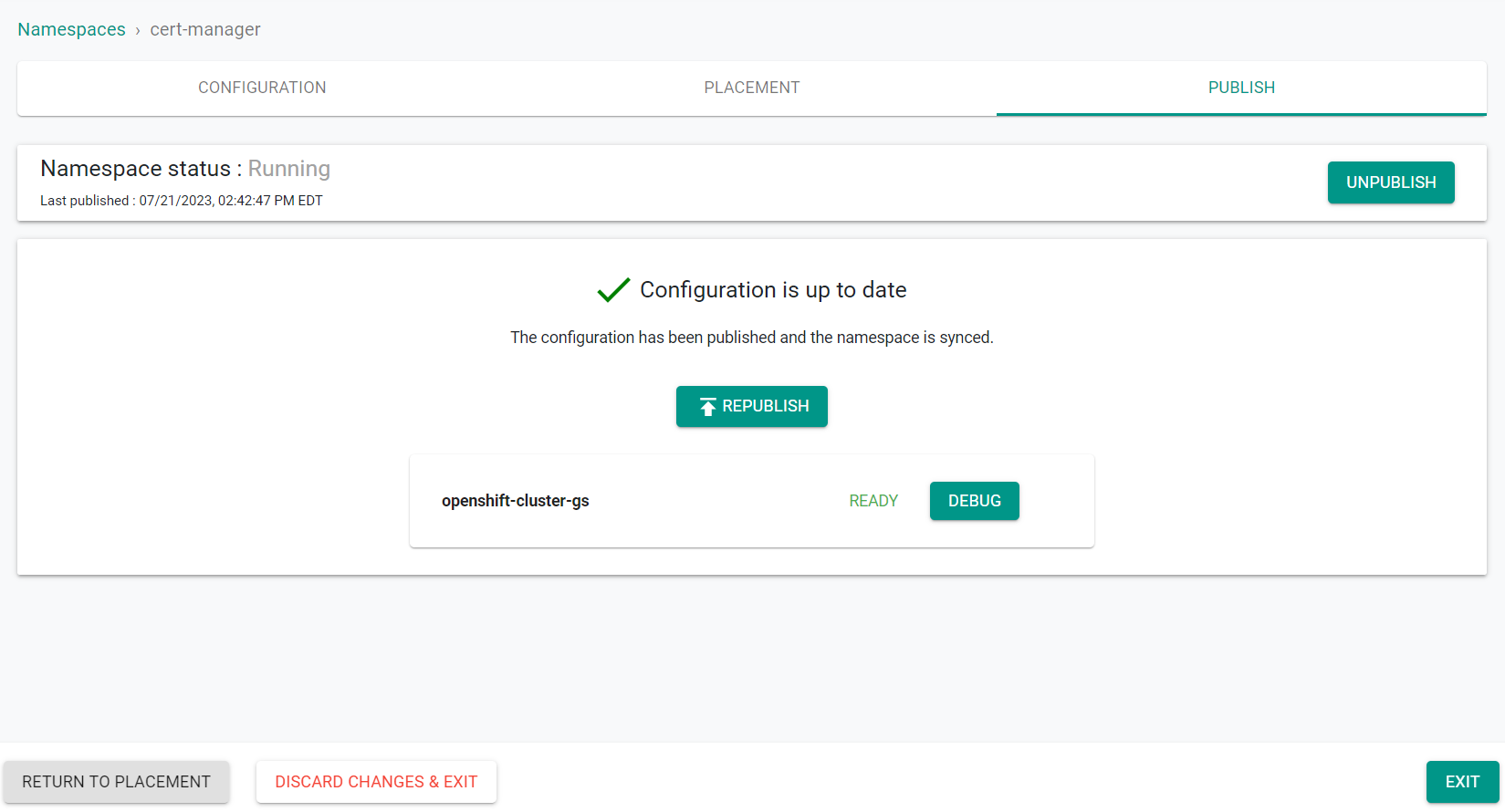
Next, you will publish the namesapace to the cluster.
- Click Publish
In a few seconds, the configured namespace will be deployed on the target cluster. Note that the target clusters can be in completely separate security domains and the controller can still manage namespace lifecyle remotely.
- Click Exit
Step 2: Verify Namespace¶
Optionally, you can verify what the published namespace looks like on your cluster.
- In your project, navigate to Infrastructure -> Clusters
- Click Kubectl on the cluster card
- Enter the following command
kubectl get ns
In the example below, you can see that the "cert-manager" namespace was created on the cluster a short while back when we published it.
NAME STATUS AGE
cert-manager Active 1m36s
default Active 3h9m
kube-node-lease Active 3h9m
kube-public Active 3h9m
kube-system Active 3h9m
openshift Active 3h4m
openshift-apiserver Active 3h6m
openshift-apiserver-operator Active 3h9m
openshift-authentication Active 3h6m
openshift-authentication-operator Active 3h9m
openshift-cloud-controller-manager Active 3h9m
openshift-cloud-controller-manager-operator Active 3h9m
openshift-cloud-credential-operator Active 3h9m
openshift-cloud-network-config-controller Active 3h9m
openshift-cluster-csi-drivers Active 3h9m
openshift-cluster-machine-approver Active 3h9m
openshift-cluster-node-tuning-operator Active 3h9m
openshift-cluster-samples-operator Active 3h9m
openshift-cluster-storage-operator Active 3h9m
openshift-cluster-version Active 3h9m
openshift-config Active 3h8m
openshift-config-managed Active 3h8m
openshift-config-operator Active 3h9m
openshift-console Active 175m
openshift-console-operator Active 175m
openshift-console-user-settings Active 175m
openshift-controller-manager Active 3h6m
openshift-controller-manager-operator Active 3h9m
openshift-dns Active 3h6m
openshift-dns-operator Active 3h9m
openshift-etcd Active 3h9m
openshift-etcd-operator Active 3h9m
openshift-host-network Active 3h7m
openshift-image-registry Active 3h9m
openshift-infra Active 3h9m
openshift-ingress Active 3h5m
openshift-ingress-canary Active 179m
openshift-ingress-operator Active 3h9m
openshift-insights Active 3h9m
openshift-kni-infra Active 3h8m
openshift-kube-apiserver Active 3h9m
openshift-kube-apiserver-operator Active 3h9m
openshift-kube-controller-manager Active 3h9m
openshift-kube-controller-manager-operator Active 3h9m
openshift-kube-scheduler Active 3h9m
openshift-kube-scheduler-operator Active 3h9m
openshift-kube-storage-version-migrator Active 3h6m
openshift-kube-storage-version-migrator-operator Active 3h8m
openshift-machine-api Active 3h8m
openshift-machine-config-operator Active 3h9m
openshift-marketplace Active 3h9m
openshift-monitoring Active 3h8m
openshift-multus Active 3h7m
openshift-network-diagnostics Active 3h7m
openshift-network-operator Active 3h9m
openshift-node Active 3h4m
openshift-nutanix-infra Active 3h8m
openshift-oauth-apiserver Active 3h6m
openshift-openstack-infra Active 3h8m
openshift-operator-lifecycle-manager Active 3h8m
openshift-operators Active 3h8m
openshift-ovirt-infra Active 3h8m
openshift-route-controller-manager Active 3h6m
openshift-sdn Active 3h7m
openshift-service-ca Active 3h6m
openshift-service-ca-operator Active 3h9m
openshift-user-workload-monitoring Active 3h8m
openshift-vsphere-infra Active 3h8m
rafay-infra Active 85m
rafay-system Active 86m
You can also look deeper into the namespace by describing it.
- Enter the following command
kubectl describe ns cert-manager
Notice that the the custom label we specified previously is part of the namespace.
Name: cert-manager
Labels: addon=cert-manager
app.kubernetes.io/managed-by=Helm
k8smgmt.io/project=defaultproject
k8smgmt.io/update-time=1689964965900650928
kubernetes.io/metadata.name=cert-manager
name=cert-manager
pod-security.kubernetes.io/audit=restricted
pod-security.kubernetes.io/audit-version=v1.24
pod-security.kubernetes.io/warn=restricted
pod-security.kubernetes.io/warn-version=v1.24
rep-cluster=299j732
rep-cluster-name=openshift-cluster-gs
rep-drift-reconcillation=enabled
rep-organization=z2473e2
rep-partner=rx28oml
rep-placement=mx4zn1j
rep-project=pkv39em
rep-project-name=defaultproject
rep-system-managed=true
rep-workload=namespace-mxj3vjk-cert-manager
rep-workloadid=kg1637k
Annotations: meta.helm.sh/release-name: namespace-mxj3vjk-cert-manager
meta.helm.sh/release-namespace: cert-manager
openshift.io/sa.scc.mcs: s0:c26,c25
openshift.io/sa.scc.supplemental-groups: 1000700000/10000
openshift.io/sa.scc.uid-range: 1000700000/10000
rafay.dev/resource-hash: 829f3553062fa47700c91ac99dad105d16f54a495e53fc80508a27a5f5f42a24
rep-drift-action: deny
Status: Active
No resource quota.
No LimitRange resource.
Recap¶
Congratulations! At this point, you have successfully configured and published a namespace to your cluster. You also verified the namespace's specification directly on the cluster using Kubectl.