Mar
v1.1.24 - Terraform Provider¶
05 March, 2024
An updated version of the Terraform provider is now available.
This release includes enhancements around resources listed below:
Existing Resources
rafay_gke_cluster: Reservation affinity support has been added to this resource
Data sources are now available in the following resources, facilitating the retrieval of information from various sources and its utilization within your Terraform configuration.
- rafay_addon
- rafay_aks_cluster
- rafay_aks_cluster_v3
- rafay_blueprint
- rafay_download_kubeconfig
- rafay_eks_cluster
- rafay_gke_cluster
- rafay_group
- rafay_group
- rafay_project
- rafay_user
v2.4 - SaaS¶
1 Mar, 2024
The section below provides a brief description of the new functionality and enhancements in this release.
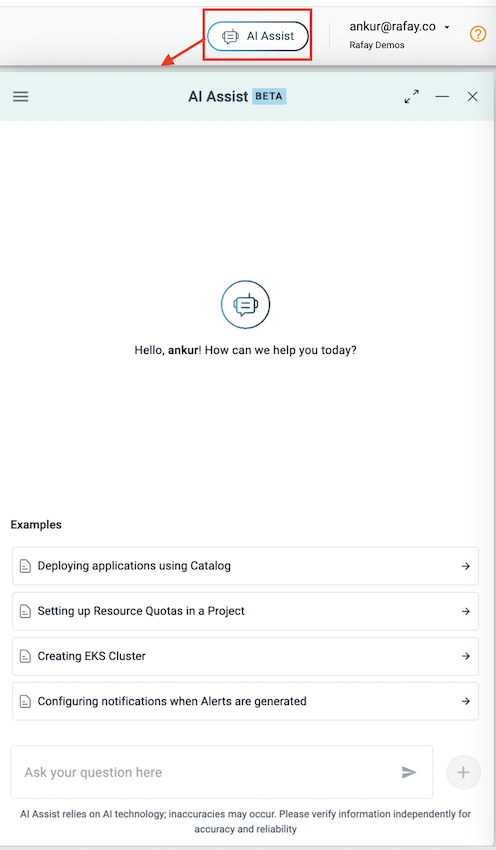
Rafay AI Assist (Beta)¶
With this release, we are introducing Rafay AI Assist, an AI chatbot. Users can leverage the assistant to ask questions around capabilities part of Rafay platform and receive responses.
Important
Limited Access - AI Assist is currently in beta and is selectively enabled for customer orgs. Please reach out to support if you want to get this enabled for your organization. For more information,please visit the AI Assist Overview page.
Amazon EKS and Azure AKS¶
Fleet Operations¶
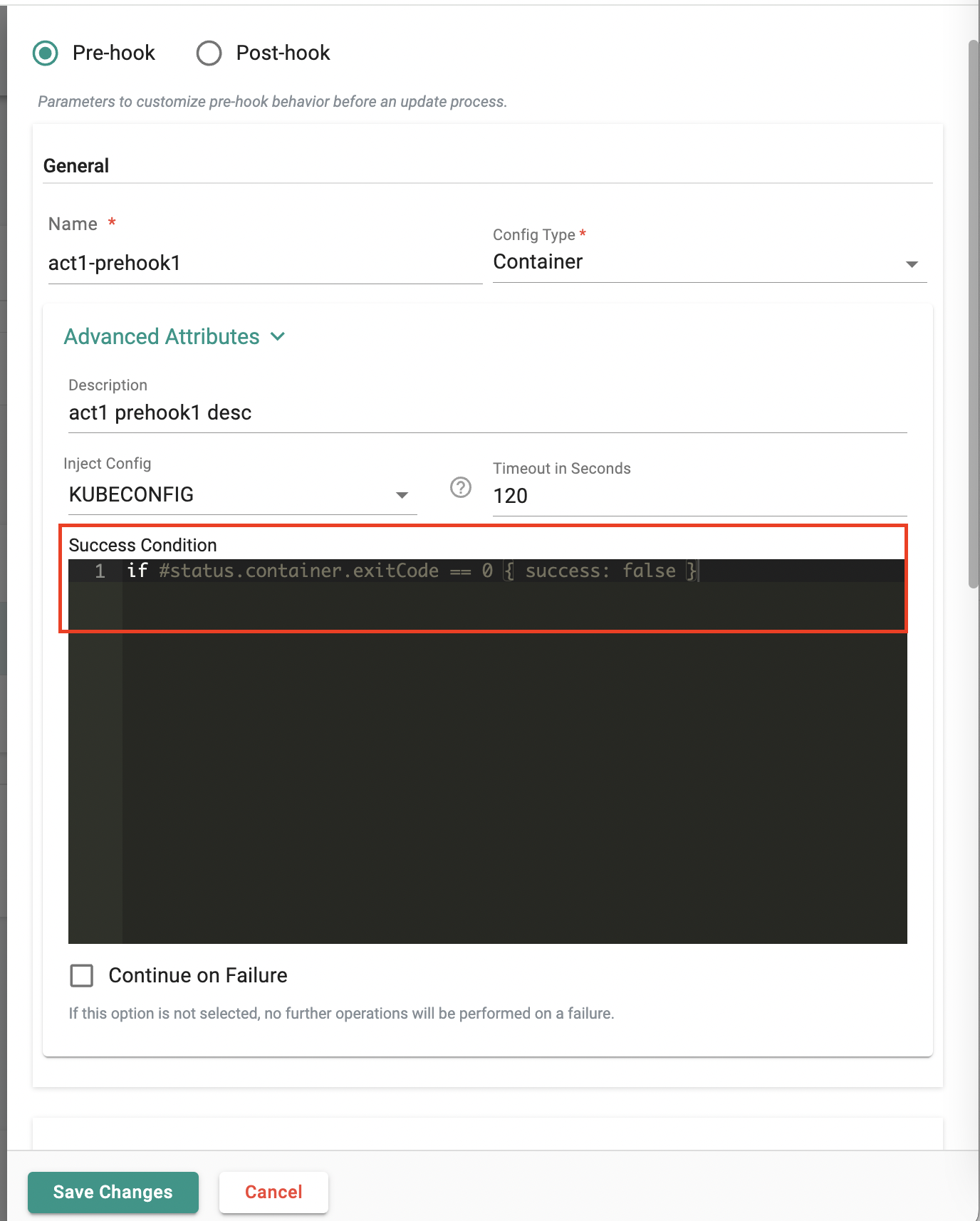
Success Condition
By default. certain conditions indicate the success or failure of a hook operation. As an example, HTTP response with a status code of 200 and a container exit code of 0 indicates success. Any other outcome indicates a failure.
With this release, users can specify criteria (by defining Success Conditions) that will indicate success or failure of a hook operation.
The screenshot below shows an override can be configured for exitCode == 0 (which by default indicates success) to indicate a failure using the Success condition expression.
As an example, if you see the screenshot, the exitCode == 0 implies that we are simply attempting to override the default true success state to false using Success condition expression.
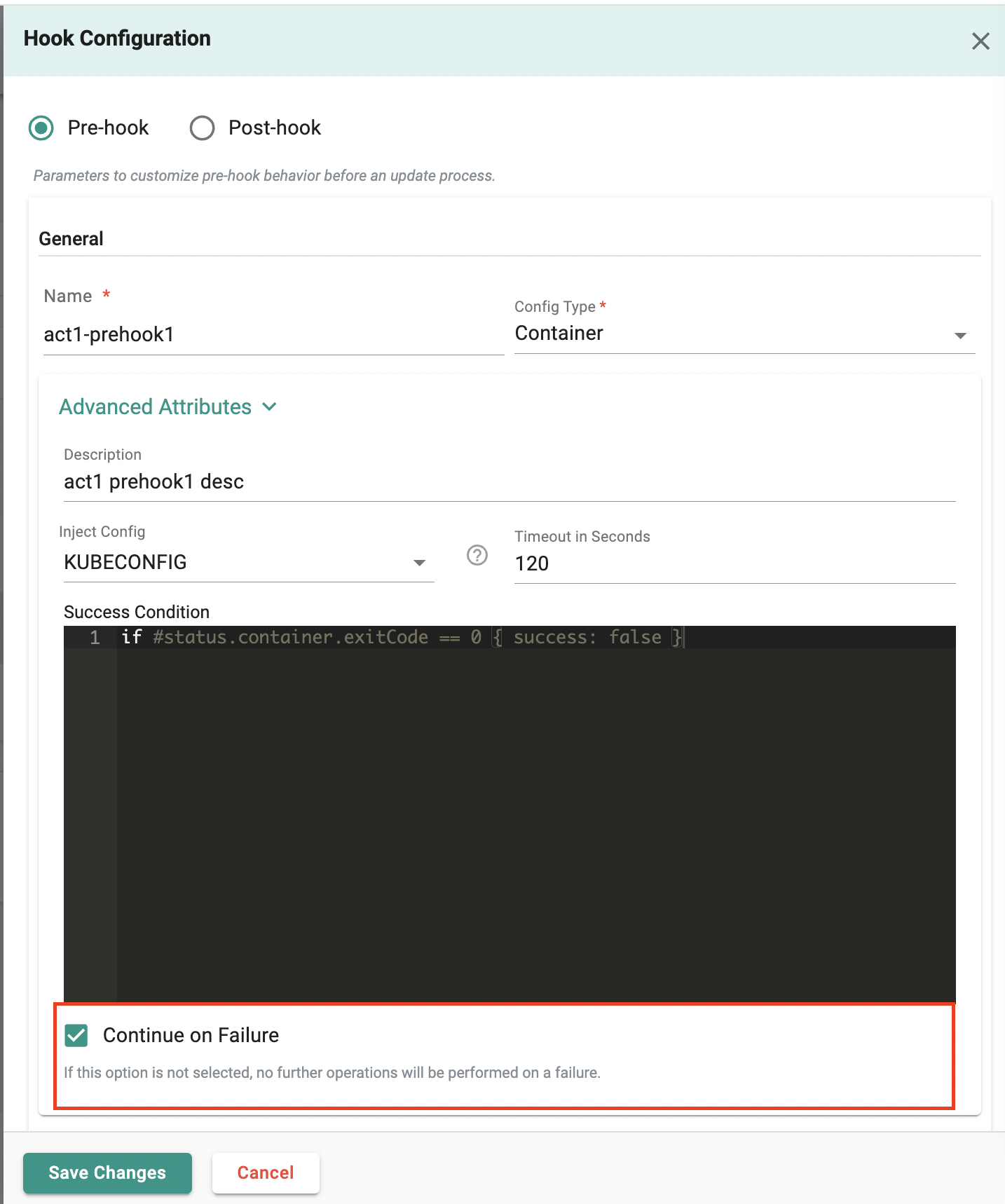
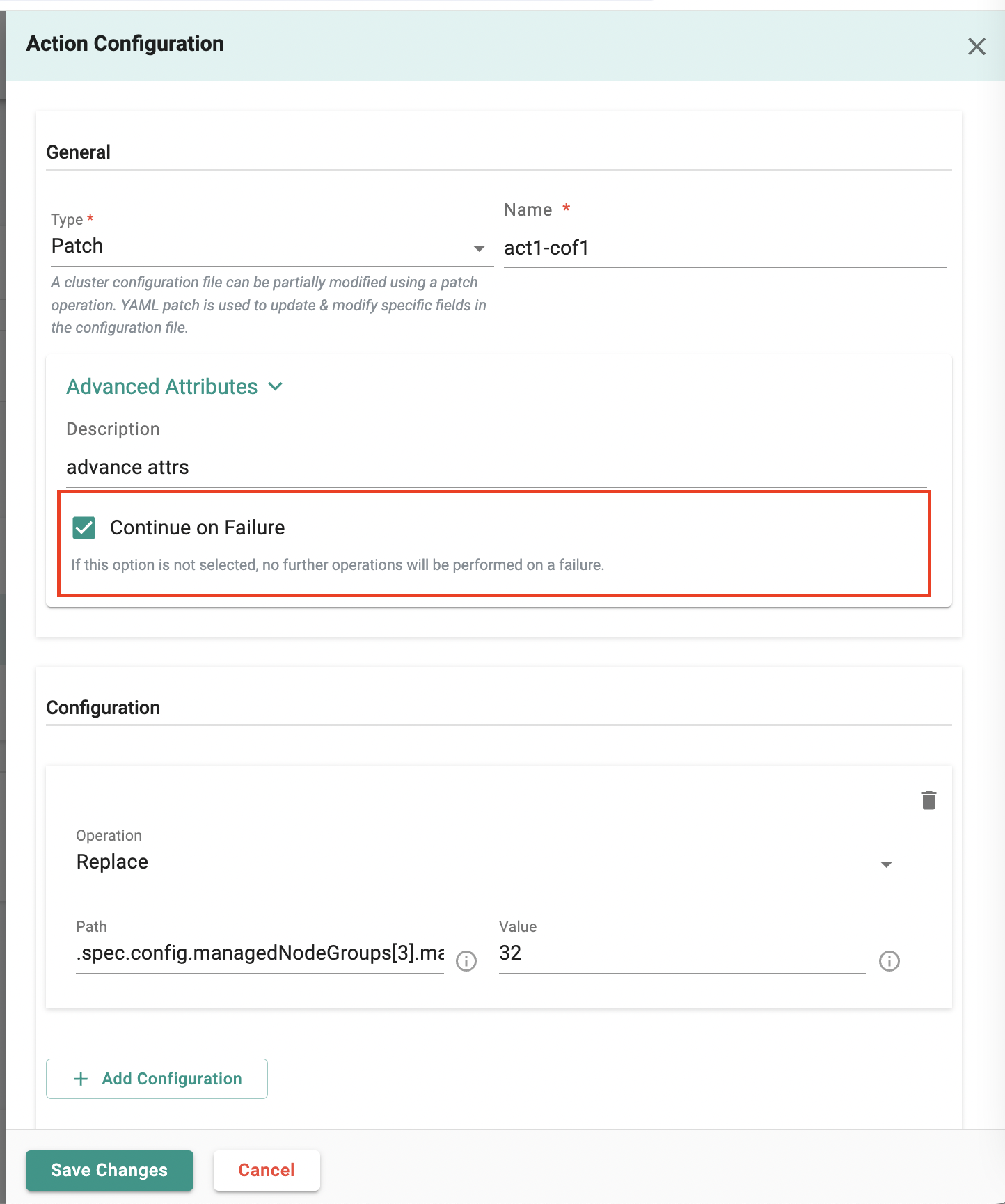
Continue on Failure
If any hook or action failed, the fleet plan would stop and fail previously. With this release, users are provided an option to continue even if there is a failure by checking the continue on failure option. If this option isn't selected, no more actions will be taken if there's a failure (this is the default behavior).
Hook Config
Action Config
Amazon EKS¶
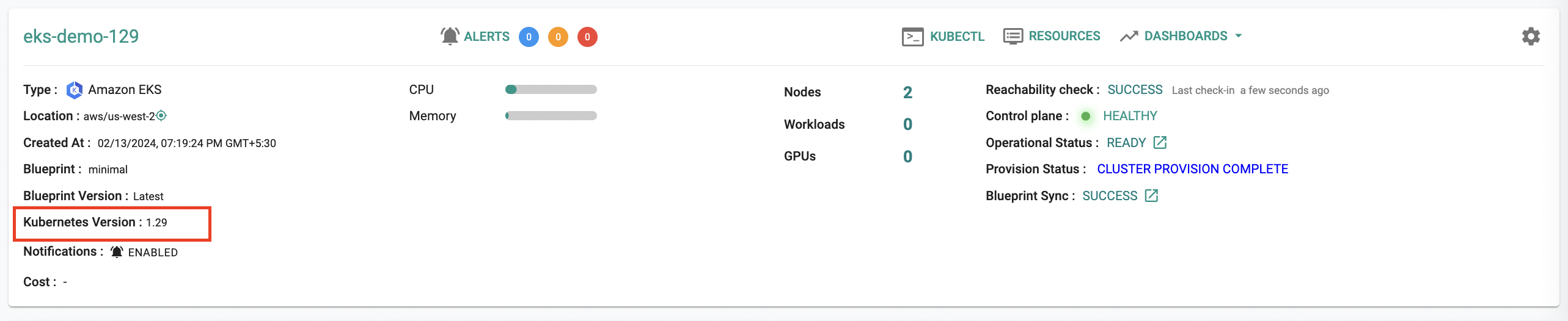
Kubernetes v1.29¶
New EKS clusters can now be provisioned based on Kubernetes v1.29. Existing clusters managed by the controller can be upgraded "in-place" to Kubernetes v1.29.
Google GKE¶
Dry Run¶
Prior release supported "dry run" functionality for Amazon EKS, Azure AKS, and Imported cluster types.
This release extends this functionality to include the GKE cluster type as well. Dry run can be used to obtain information about the operations that will be performed during cluster provisioning. By executing the dry run command, you can preview the operations that would take place without actually applying them.
rctl apply -f cluster_spec.yaml --dry-run
For example, if you are using the same cluster name that exists in your project in your cluster configuration file again , as part of a dry run check using the above command, the output will be similar to the following:
{
"operations": [
{
"operation": "Cluster Create",
"resourceName": "my-cluster-name",
"comment": "Cluster does not exist. New cluster will be created"
}
]
}
Cluster Label Management¶
With this release, we have added support for cluster label management for GKE clusters on day 0 and day 2. Users can now add, edit, and remove labels, allowing for efficient management by enabling orchestration of workflows via cluster labels (e.g. configuration of workload placement, cluster overrides)
Upstream Kubernetes for Bare Metal and VMs¶
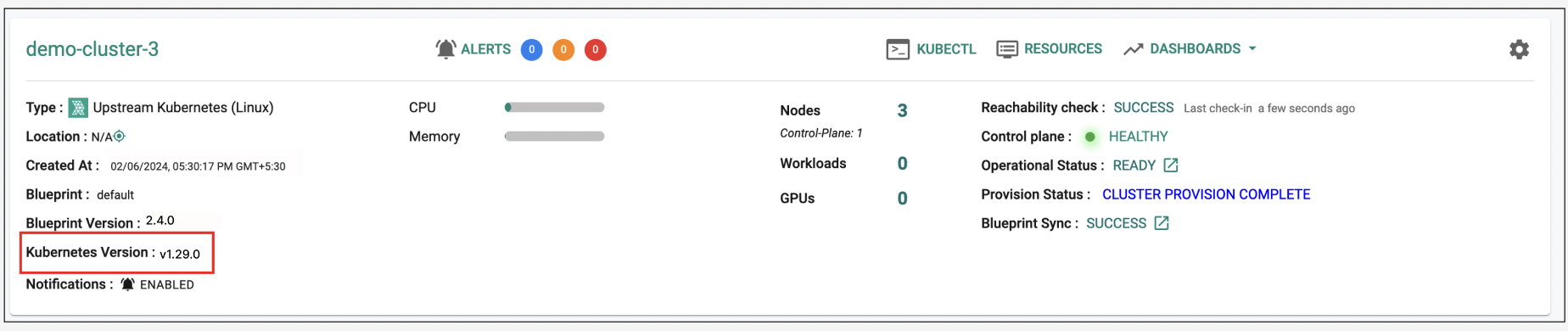
Kubernetes v1.29¶
New upstream clusters can be provisioned based on Kubernetes v1.29.x. Existing upstream Kubernetes clusters managed by the controller can be upgraded in-place to Kubernetes v1.29.
CNCF Conformance¶
Upstream Kubernetes clusters based on Kubernetes v1.29 (and prior Kubernetes versions) are fully CNCF conformant.
Blueprints¶
Golden blueprints¶
Inheritance is now supported for the following configurations:
- Webhook drift configuration
- Namespace Sync
This ensures that Custom Blueprints that use Golden BP as the base cannot override webhook and namespace sync settings configured as part of the Golden BP.
Add-on dependencies¶
A number of improvements have been implemented with this release to handle add-on dependencies. They include:
- Installation of management operator and system add-ons before deployment of custom add-ons
- Honoring custom add-on dependencies when Golden BP is used as the base
Zero-Trust Access¶
Custom RBAC¶
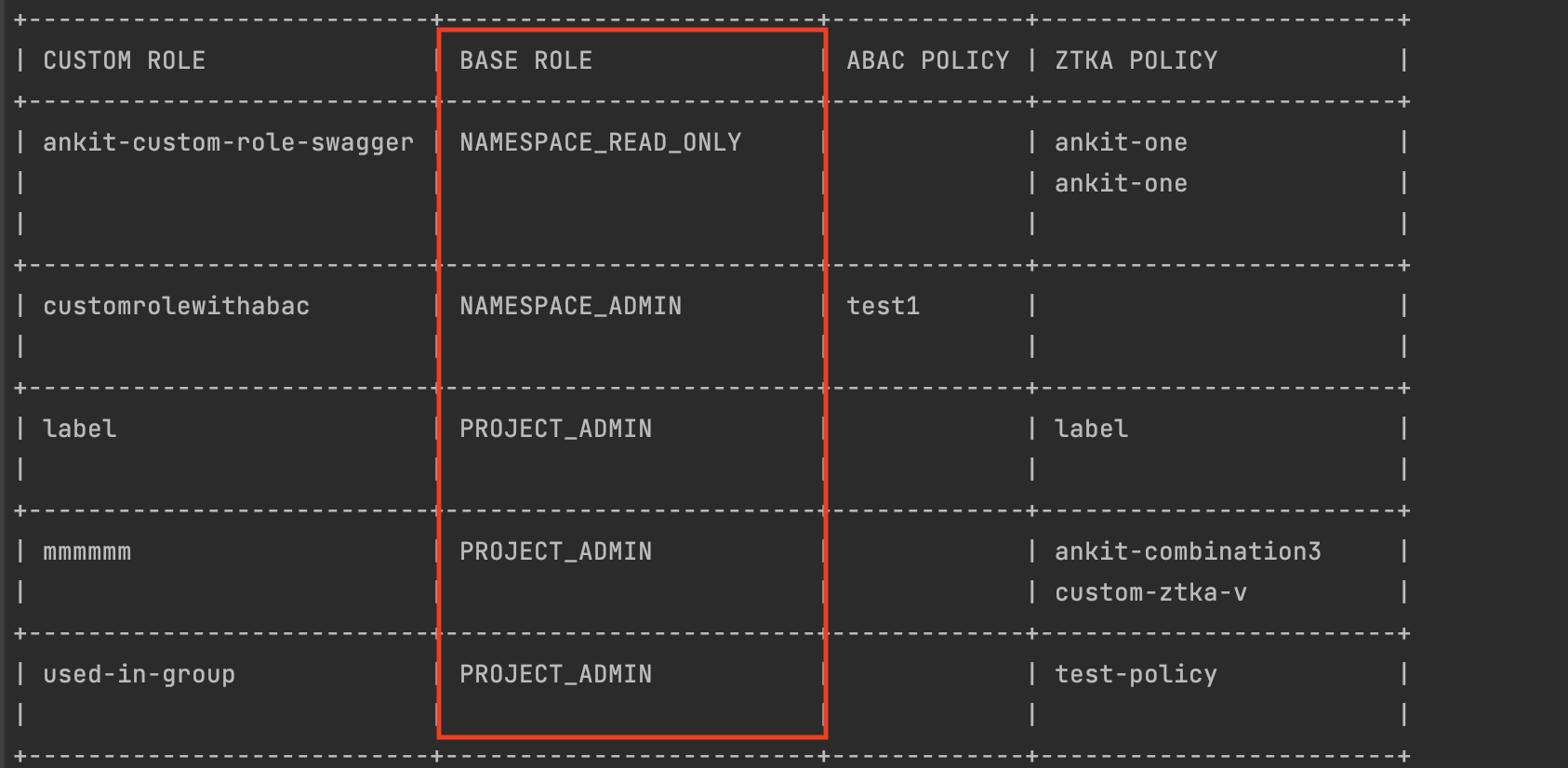
s In a previous release, we added support to configure more finely grained ZTKA access policies. This release adds several improvements to this feature including:
- Enhanced RCTL functionality to return BASE ROLE details as part of
rctl get crscommand to more easily get information on the BASE ROLE associated with the CUSTOM ROLES
- Project name validation as part of ZTKA rule version creation
- Cluster name validation as part of ZTKA rule version creation
- More intuitive error messages for a better user experience
GitOps¶
Agents¶
GitOps agent is configured with the "unless-stopped" restart policy with this release. This ensures that whenever the GitOps machine is rebooted, the agent containers automatically start.
Integrations¶
Repository¶
RCTL functionality has now been extended to support validation of repositories. This was previously only supported via the UI interface. More information can be found here
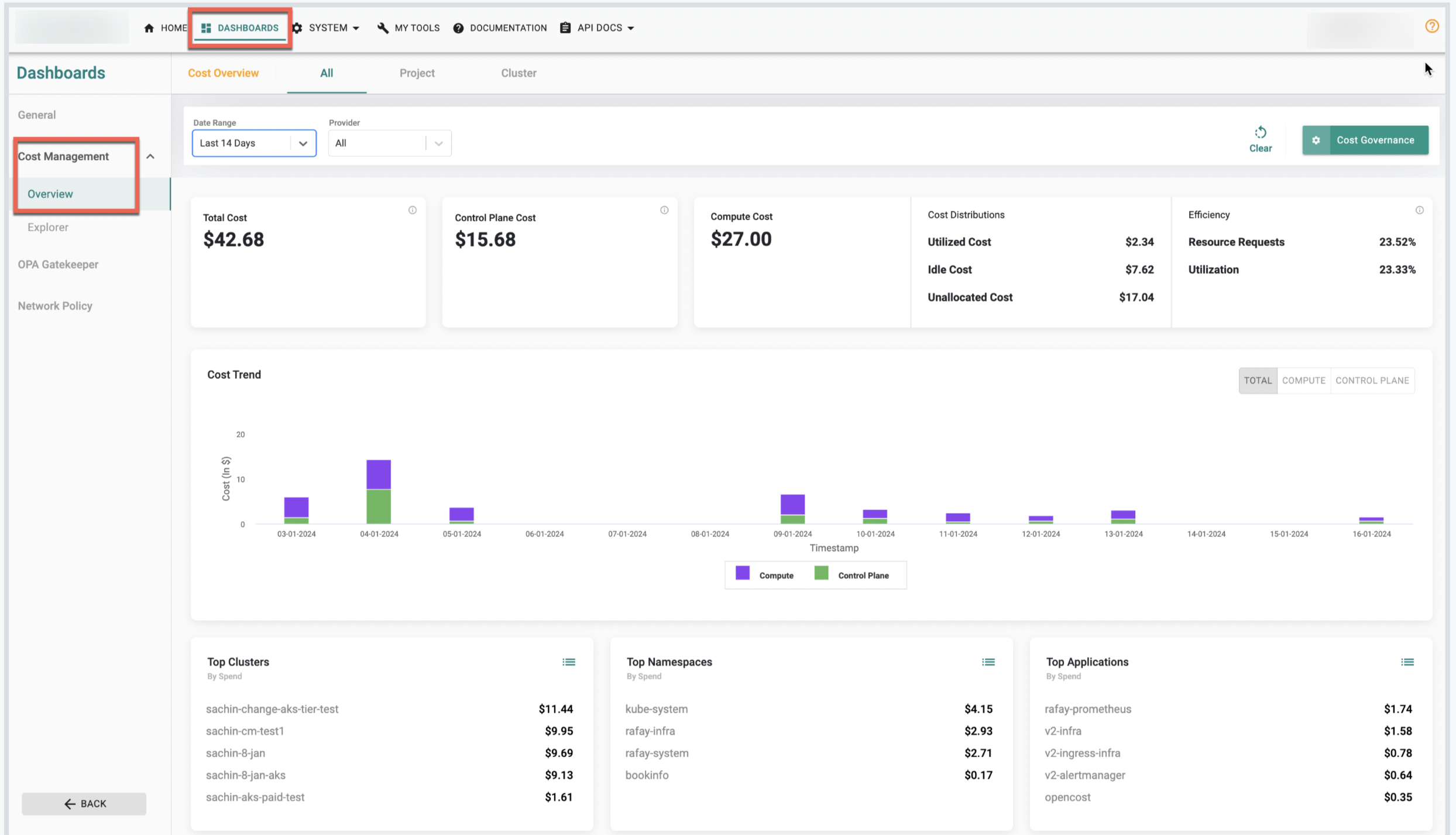
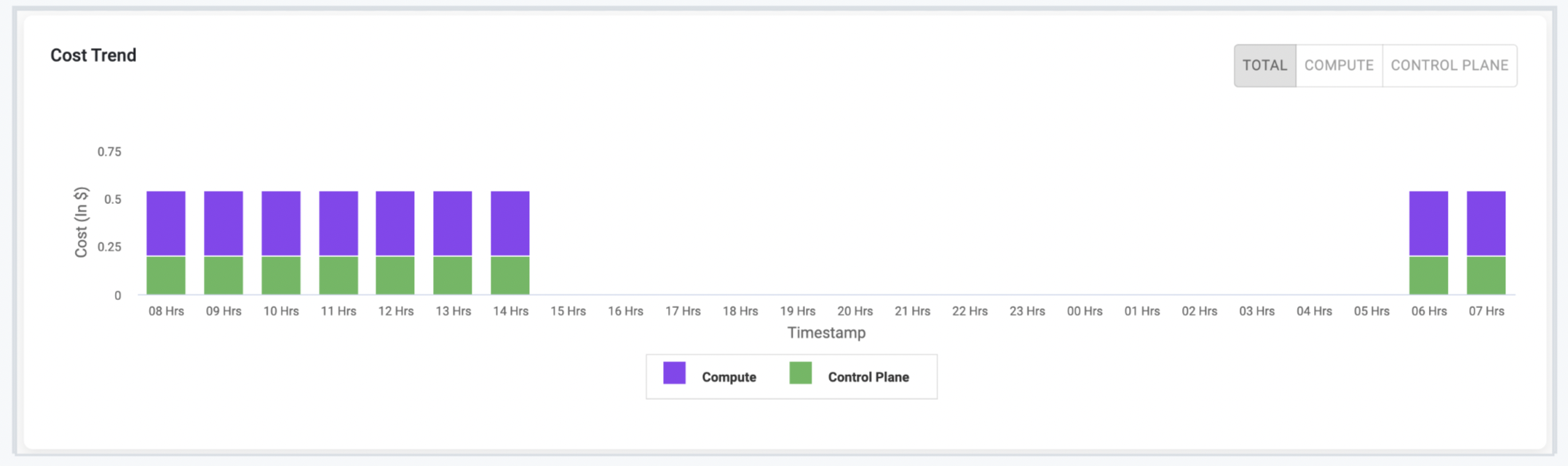
Cost Management¶
Control Plane Cost¶
As part of this release, the Cost Overview dashboard has been enhanced to show the cluster management cost (Control Plane Cost) for EKS/AKS clusters . Additionally, these costs are included as part of Showback/Chargeback Costs.
Cost Management Dashboard
Cost Trend
Zero-Trust Access¶
Access Proxy¶
With this release, use of FIPS compliant libraries is mandatorily enforced with Rafay's Kube API Access Proxy.
Terraform Provider¶
Caching¶
There are certain scenarios where diff is shown even when there are no changes. A caching mechanism has been implemented for TF schema to alleviate this issue for the following resources:
- Blueprints
- Add-ons
- Projects
Important
Limited Access - This capability is selectively enabled for customer orgs. Please reach out to support if you want to get this enabled for your organization. Support for more resources will be added with future releases.
v2.4 Bug Fixes¶
| Bug ID | Description |
|---|---|
| RC-32240 | AKS: Unable to provision cluster using AKS template when nodepool related configurations are changed |
| RC-32656 | RBAC : Modifying/adding namespace to existing Roles in a group results in duplicate namespace association |
| RC-32438 | Add-on creation fails when creating a new version with no values_paths block |
| RC-31816 | EKS: Cluster provisioning with Ubuntu AMI 20.04 fails when Role based Credential is used |
| RC-32523 | EKS: Node instance Role ARN is not being detected during "convert to managed" operation |
| RC-32585 | Fixed this issue that made revoked kubeconfig files work in an unexpected way. |