Upcoming
Important
This page will be periodically updated with features that are scheduled to roll into Rafay's Preview environment as part of upcoming releases. Learn more about Previews. Learn about our recent releases.
Navigate to our public roadmap for details on what we are working on for future releases.
Blogs for New Features in Release¶
| # | Description |
|---|---|
| 1 | Draft Versions for Blueprints |
| 2 | Support for Parallel Execution with Rafay's Integrated GitOps Pipeline |
Blueprint & Add-on Management¶
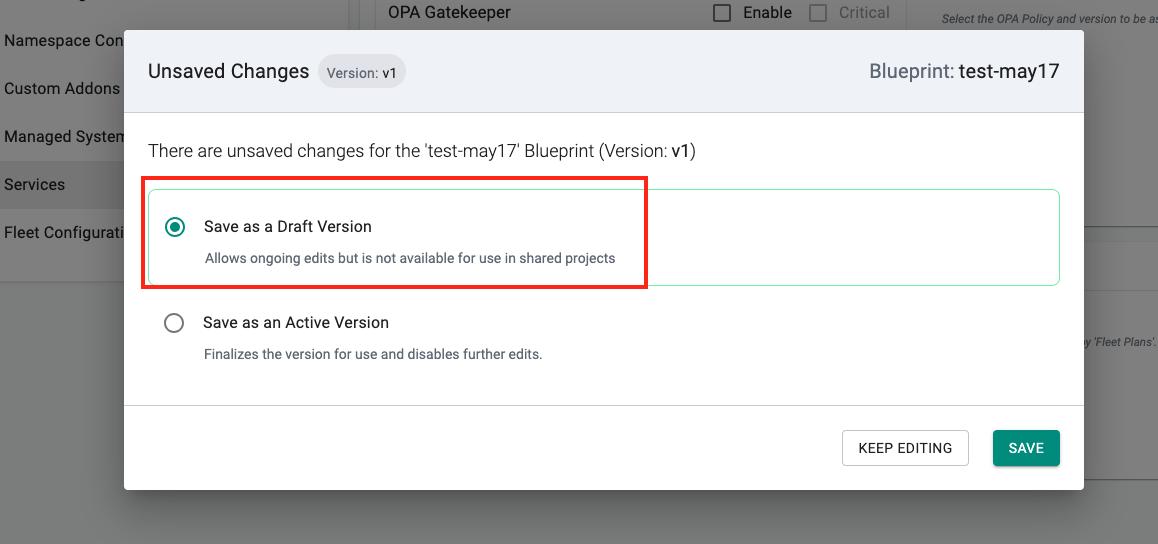
Support for Draft Versions¶
Previously, draft version support for Blueprints and Add-ons was available only via non-UI interfaces. This enhancement brings the same capability to the UI, allowing users to configure and visualize draft versions directly through the console.
Note
For more details on draft version support and recommendations on how to use this feature at scale, refer to our blog post.
Parallel execution of Pipeline Stages¶
By default, stages within a configured pipeline are executed sequentially. However, in many cases, these stages are independent and do not require sequential execution. This enhancement introduces support for parallel execution of such stages, allowing users to design workflows such as deploying multiple independent workloads that run simultaneously. This results in reduced overall deployment time and greater automation efficiency.