Part 2: Apply
This is Part 2 of a multi-part, self-paced quick start exercise.
What Will You Do¶
In part 2, you will create a custom blueprint that contains one of the turnkey OPA Gatekeeper policies and apply the blueprint to a cluster.
Step 1: Create Blueprint¶
First, we will create a custom cluster blueprint which will enable OPA Gatekeeper and contain one of the newly created custom OPA policies.
- Navigate to Infrastructure -> Blueprints
- Click "New Blueprint"
- Provide a name for the blueprint
- Click "Save"
Next, we will need to create a version for the blueprint.
- Provide a name for the blueprint version
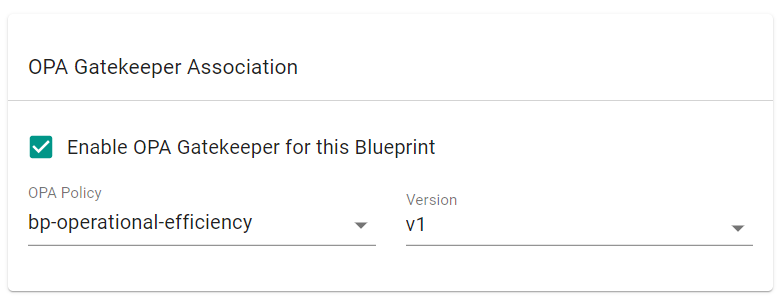
- Select "Enable OPA Gatekeeper for this Blueprint"
- Select the "bp-operational-efficiency" policy
- Select "v1" for the OPA policy version
- Click "Save Changes"
Step 2: Apply Blueprint¶
We will now apply the custom blueprint to the cluster to enable OPA Gatekeeper and the "bp-operational-efficiency" policy
- Navigate to Infrastructure -> Clusters
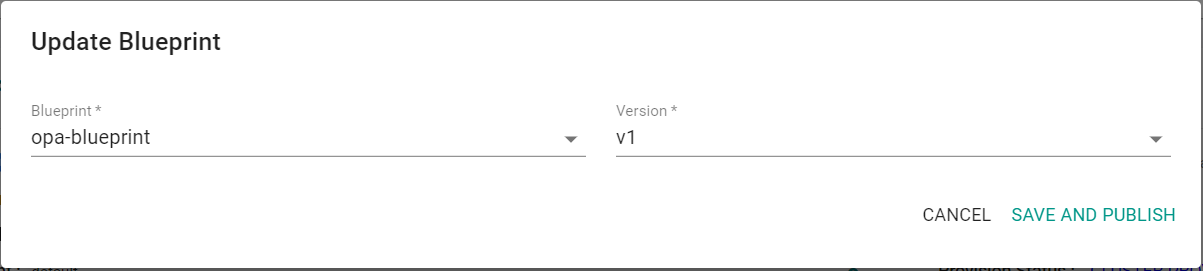
- Click the gear icon for the cluster and select "Update Blueprint"
- Select the previously created blueprint and blueprint version
- Click "Save and Publish"
You will now see the blueprint being applied to the cluster
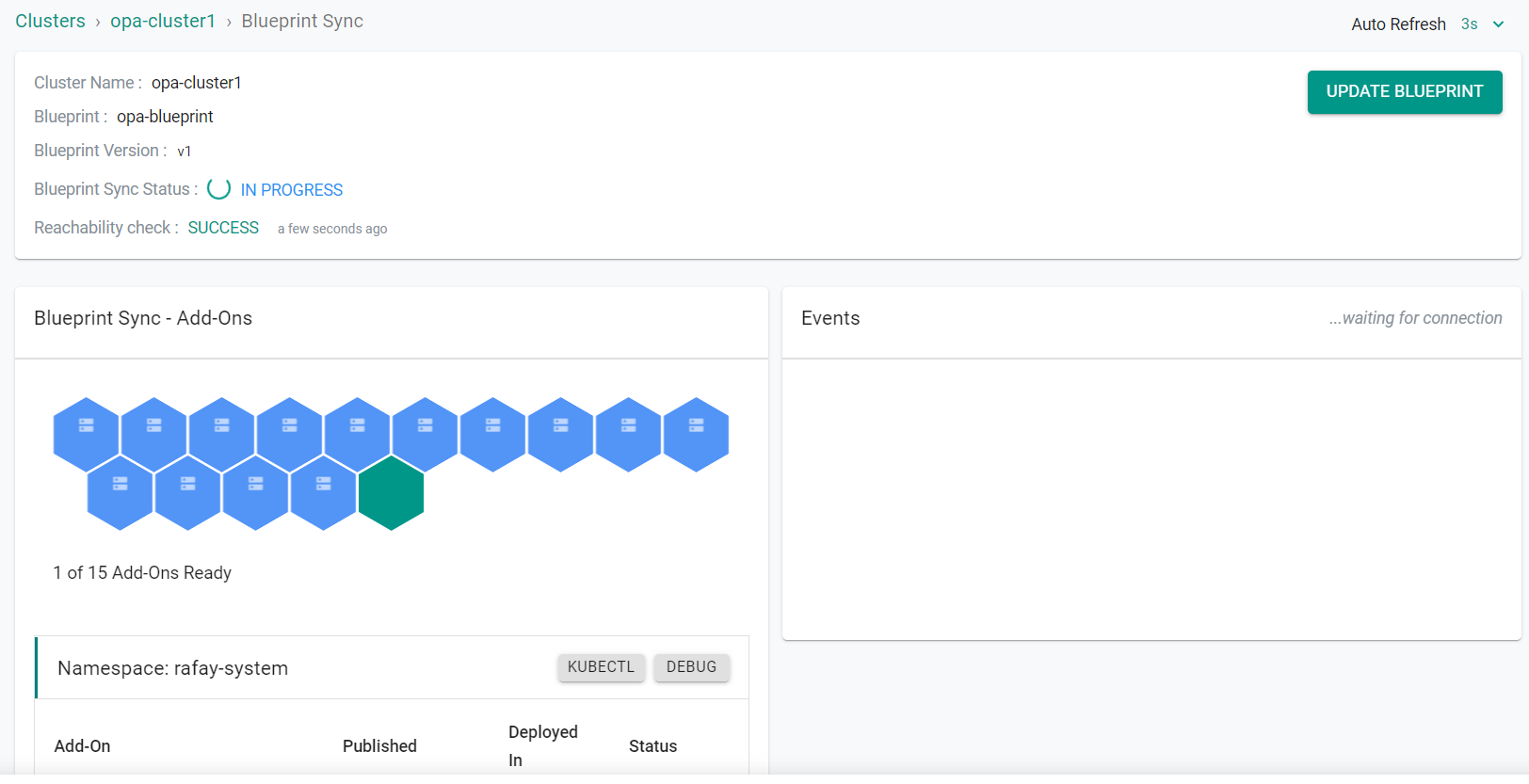 ¶
¶
Step 3: Verify OPA Gatekeeper Resources¶
Now, we will verify that OPA Gatekeeper is running on the cluster with the constraints in our OPA policy
- Navigate to Infrastructure -> Clusters
- Click on "KUBECTL" for your cluster
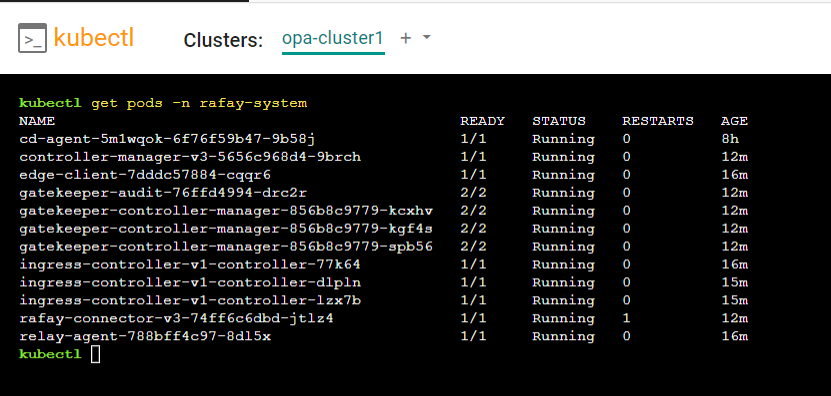
- Type the below command
kubectl get pods -n rafay-system
You will see the "gatekeeper" pods running
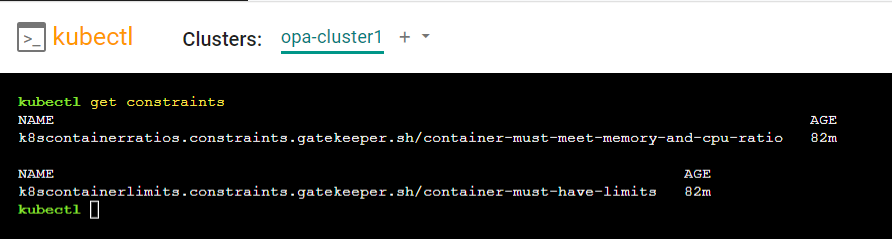
- Type the below command
kubectl get constraints
You will see all of the OPA contraints currently being enforced on the cluster. This list will contain the contraints in the applied OPA policy.
Recap¶
In this part, you applied a turnkey OPA policy to a cluster using a custom cluster blueprint. You then validated OPA gatekeeper was running and the OPA policy contraints were active on the cluster using Kubectl.