Use Cert-Manager
What Will You Do¶
In this exercise,
- You will create and publish a workload to a cluster that has a custom blueprint with the managed Ingress Controller and a cert-manager addon.
- The workload will leverage the cert-manager addon for certificate operations with Let's Encrypt.
Assumptions¶
- You have already provisioned or imported a Kubernetes cluster using the controller.
- You have successfully published a cert-manager addon based cluster blueprint to your cluster.
- You own a domain which we will use for certificate issuance.
For this example, we will use a simple container image called "http-echo". This is a in-memory web server that echoes back arguments provided to it.
Step 1: Configure DNS¶
Ensure that you configure DNS for your workload's ingress domain with your DNS provider. In our example, the workload will be accessible to users at "https://echo.infra.gorafay.net". We can verify that DNS is configured properly by using the "dig" utility.
dig echo.infra.gorafay.net
; <<>> DiG 9.10.6 <<>> echo.infra.gorafay.net
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 54549
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;echo.infra.gorafay.net. IN A
;; ANSWER SECTION:
echo.infra.gorafay.net. 300 IN A 52.250.10.71
echo.infra.gorafay.net. 300 IN A 52.250.15.222
;; Query time: 55 msec
;; SERVER: 2001:558:feed::1#53(2001:558:feed::1)
;; WHEN: Tue Aug 11 19:43:56 PDT 2020
;; MSG SIZE rcvd: 83
Step 2: Configure k8s Ingress¶
To leverage cert-manager, we will add an annotation for cert-manager to the Ingress object. In the example below, the Cluster Issuer points to what we created in the cluster blueprint.
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: echo-ingress
annotations:
kubernetes.io/ingress.class: "nginx"
cert-manager.io/cluster-issuer: "letsencrypt-http"
spec:
tls:
- hosts:
- echo.infra.gorafay.net
secretName: echo-tls
rules:
- host: echo.infra.gorafay.net
http:
paths:
- backend:
serviceName: echo
servicePort: 80
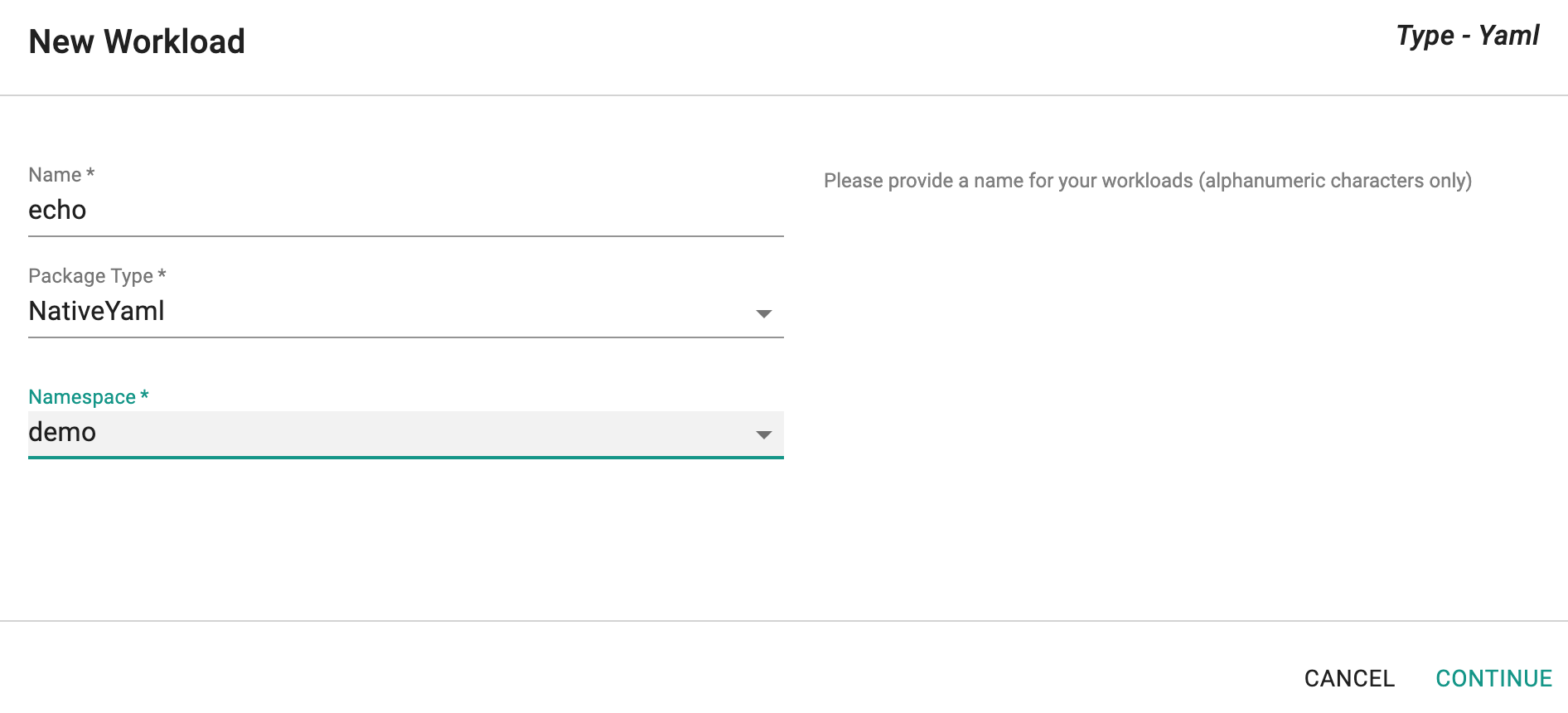
Step 3: Create Workload¶
- Copy the yaml below, update the Ingress object from the previous step
- Create a workload (type: k8s yaml), select a cluster and publish it
apiVersion: v1
kind: Service
metadata:
name: echo
spec:
ports:
- port: 80
targetPort: 5678
selector:
app: echo
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: echo
spec:
selector:
matchLabels:
app: echo
replicas: 1
template:
metadata:
labels:
app: echo
spec:
containers:
- name: echo
image: hashicorp/http-echo
args:
- "-text=This is a Let's Encrypt Test. Check the Certificate Details !!!"
ports:
- containerPort: 5678
---
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: echo-ingress
annotations:
kubernetes.io/ingress.class: "nginx"
cert-manager.io/cluster-issuer: "letsencrypt-http"
spec:
tls:
- hosts:
- echo.infra.gorafay.net
secretName: echo-tls
rules:
- host: echo.infra.gorafay.net
http:
paths:
- backend:
serviceName: echo
servicePort: 80
Once the workload is published, you should see something like the illustrative screenshot below
Step 4: Verification¶
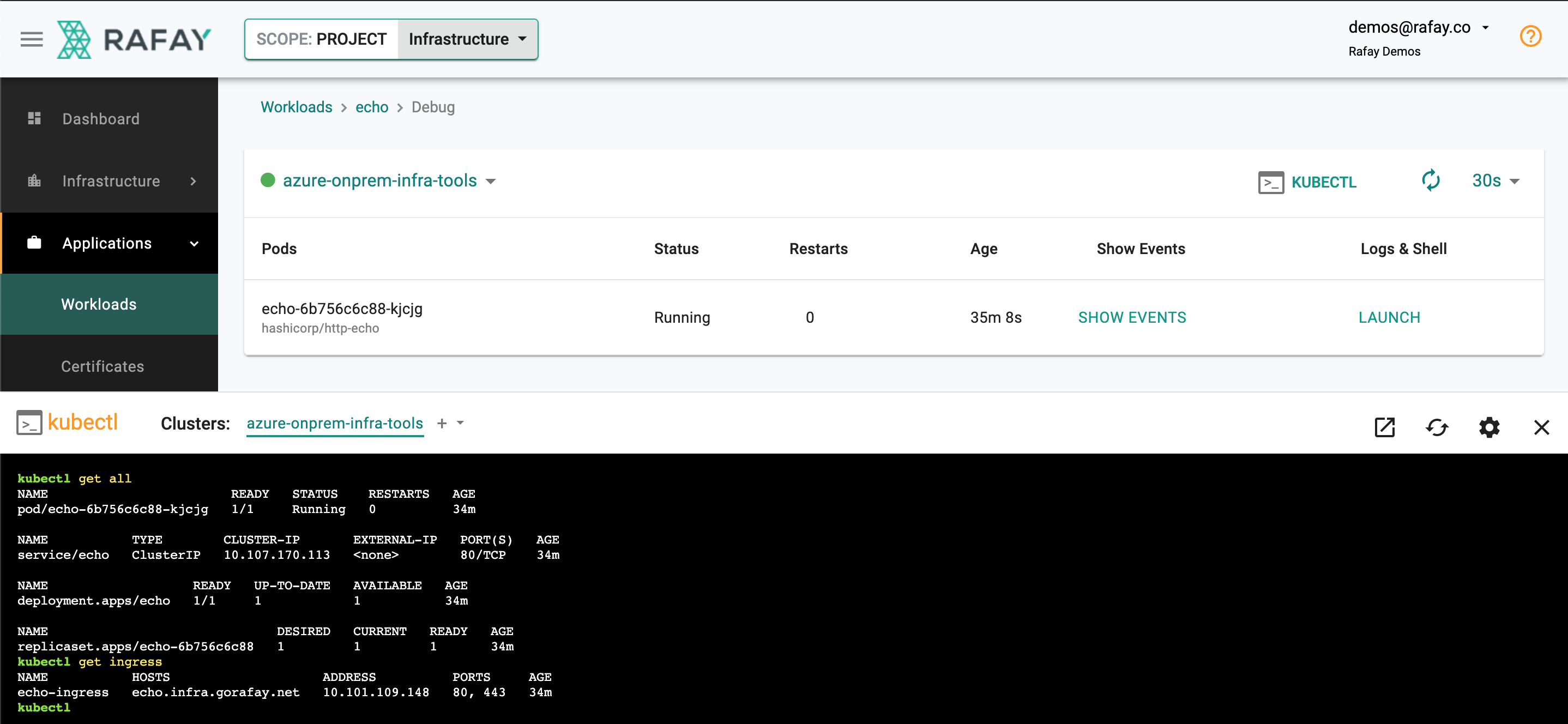
- Click on Debug and the KubeCTL button
- First, let's verify that the required resources are deployed and healthy
kubectl get all
NAME READY STATUS RESTARTS AGE
pod/echo-6b756c6c88-kjcjg 1/1 Running 0 53m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/echo ClusterIP 10.107.170.113 <none> 80/TCP 53m
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/echo 1/1 1 1 53m
NAME DESIRED CURRENT READY AGE
replicaset.apps/echo-6b756c6c88 1 1 1 53m
Now, let's verify whether Ingress was configured properly.
kubectl get ingress
NAME HOSTS ADDRESS PORTS AGE
echo-ingress echo.infra.gorafay.net 10.101.109.148 80, 443 54m
Now, let's verify the Let's Encrypt certificate that was issued using the cert-manager addon.
kubectl get certificate
NAME READY SECRET AGE
echo-tls True echo-tls 16h
Now, let us describe the certificate that was issued from Let's Encrypt.
kubectl describe certificate echo-tls
Name: echo-tls
Namespace: demo
Labels: rep-organization=qkonnmn
rep-partner=rx28oml
rep-project=pkvzp2n
rep-workload=echo
Annotations: <none>
API Version: cert-manager.io/v1alpha2
Kind: Certificate
Metadata:
Creation Timestamp: 2020-08-12T02:06:30Z
Generation: 1
Owner References:
API Version: extensions/v1beta1
Block Owner Deletion: true
Controller: true
Kind: Ingress
Name: echo-ingress
UID: 6ffcf6cc-dc40-11ea-b8aa-000d3a6edb68
Resource Version: 26827123
Self Link: /apis/cert-manager.io/v1alpha2/namespaces/demo/certificates/echo-tls
UID: 6ffed683-dc40-11ea-b8aa-000d3a6edb68
Spec:
Dns Names:
echo.infra.gorafay.net
Issuer Ref:
Group: cert-manager.io
Kind: ClusterIssuer
Name: letsencrypt-http
Secret Name: echo-tls
Status:
Conditions:
Last Transition Time: 2020-08-12T02:06:30Z
Message: Certificate is up to date and has not expired
Reason: Ready
Status: True
Type: Ready
Not After: 2020-11-10T00:35:56Z
Events: <none>
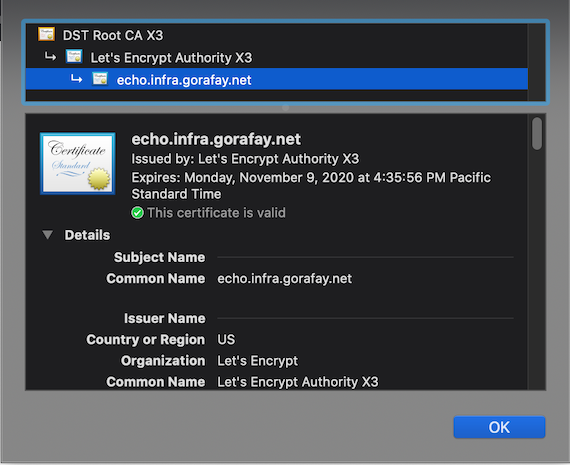
Now, open a web browser and access the domain where your workload is deployed. You should see that the page is accessible over "https" and is secured with a TLS Certificate issued by Let's Encrypt.
Recap¶
Congratulations! You deployed a workload to a Kubernetes cluster leveraging cert-manager that was deployed as part of a cluster blueprint.