Overview
IAM Service Accounts¶
Post cluster provisioning, IAM Service Accounts feature allows to specify IAM policies at pod level, enabling the users to have granular control on pods. Each pod can have different IAM policies based on the required access
Permission Boundaries for IAM¶
AWS supports permissions boundaries for IAM entities (users or roles). A permissions boundary allows to use a managed policy to set the maximum permissions that an identity-based policy can grant to an IAM entity. An entity's permissions boundary allows it to perform only the actions that are allowed by both its identity-based policies and its permissions boundaries. For more information, refer Permissions Boundaries
Create IAM Service Account¶
- Login to the controller and click Clusters
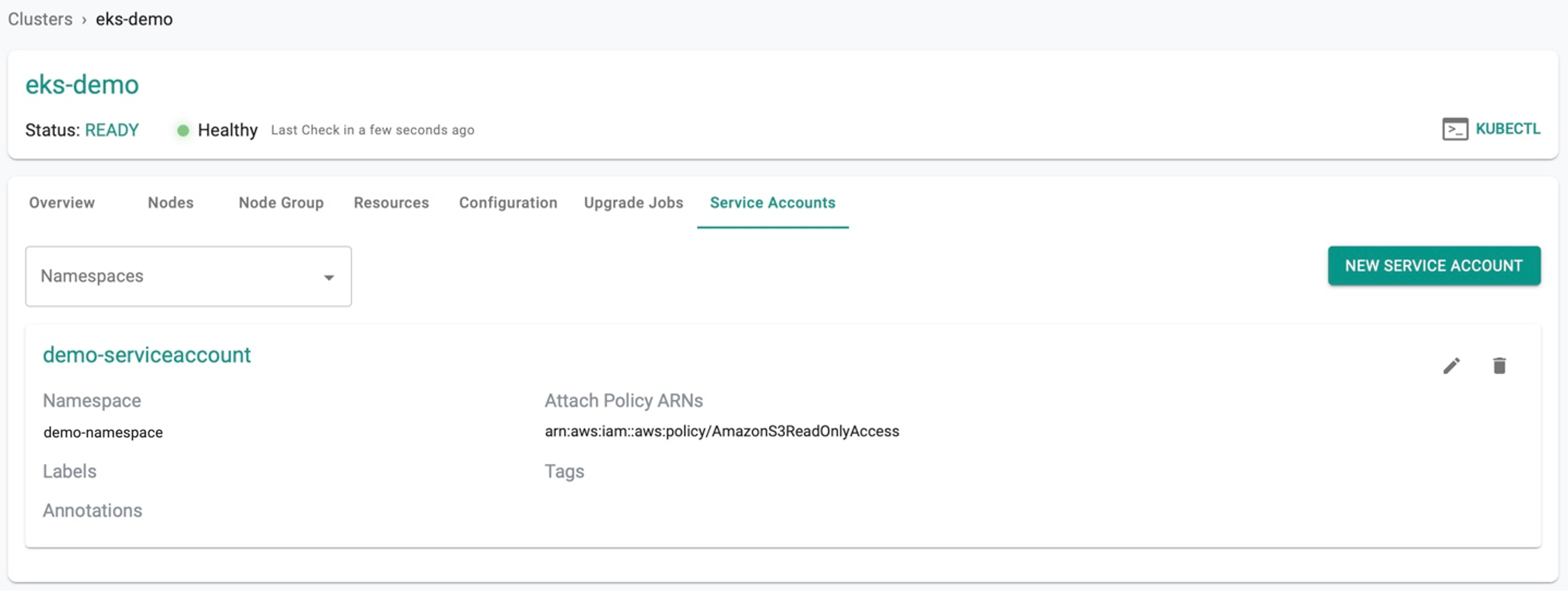
- Select the required provisioned cluster and click IAM Service Accounts tab
- Select a namespace from the drop-down to view all the service accounts associated with the selected namespace
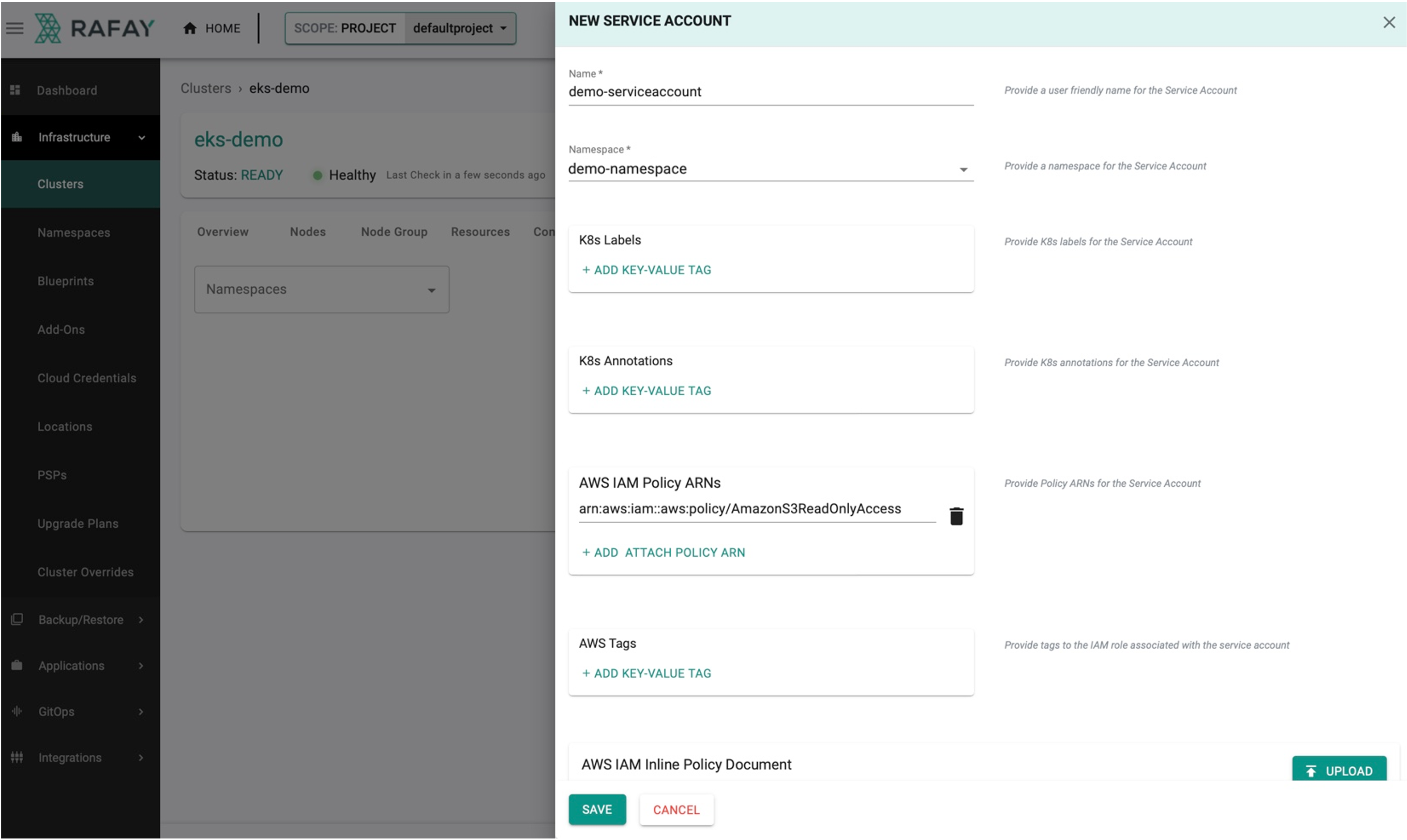
- Click New IAM Service Account
- Enter the Name for the new service account and select the Namespace
Note: Create a new Namespace if no namespace exist
- Add labels, annotations, and tags if required
- Add the existing AWS IAM Policy ARNs or create a new policy in AWS portal based on the requirements
- Click Save
Below is an example of creating a IAM service account for a pod with Amazon S3 Read-Only Access authorization
AWS IAM Policy ARN
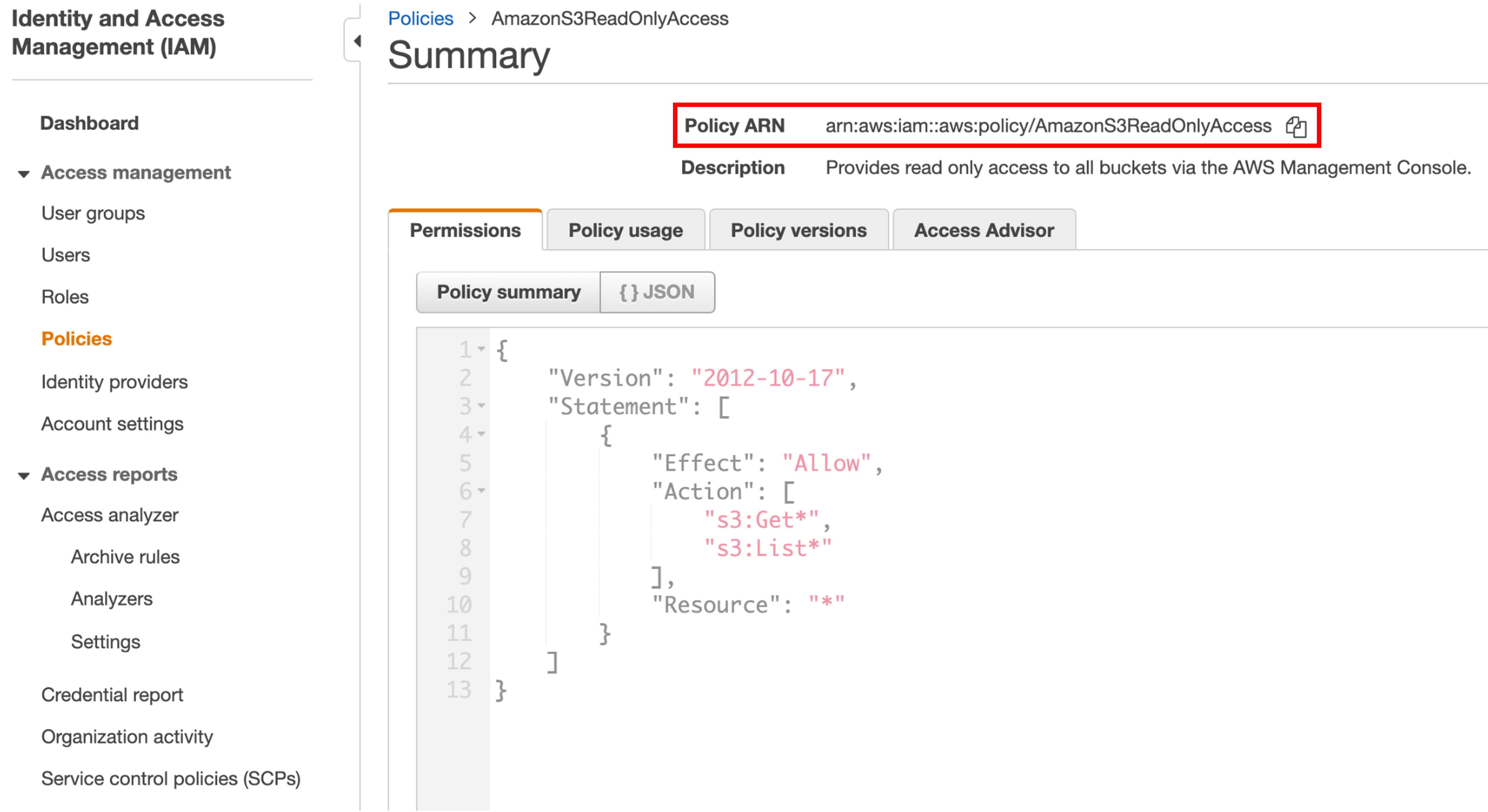
To get the AWS IAM Policy ARN from AWS Console, perform the below steps:
- Login to AWS portal and select Policies under IAM
- Select the required policy and copy the Policy ARN to create a service account (or) use the existing JSON config details of this policy
Below is an example of Amazon SE Read-Only Access policy that allows only the actions Get and List
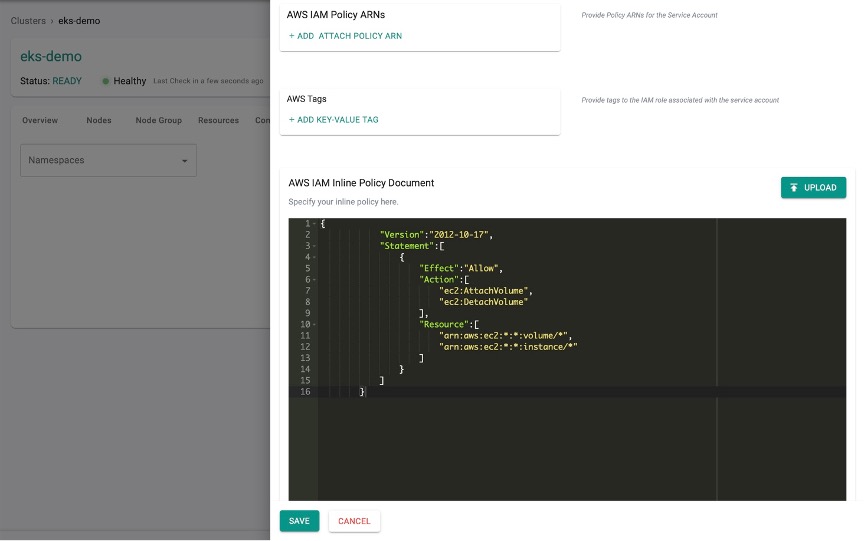
AWS IAM Inline Policy Document¶
- Users who prefer to use the customized configuration for this service account, either manually provide the config details or click Upload to upload an AWS IAM Inline Policy Documents
- Click Save
Important
Either provide AWS IAM Policy ARNs (or) upload an AWS IAM Inline Policy Document (any one is mandatory). This is to infuse the customized policies to the service accounts
A message indicates the IAM Service Account creation is in progress
View IAM Service Account status¶
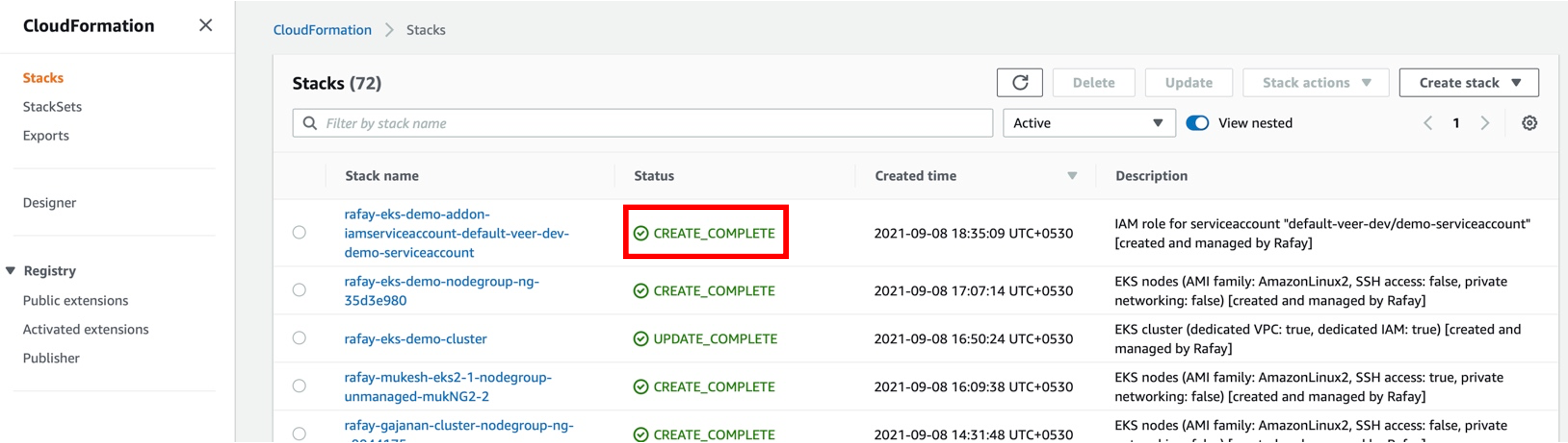
Once the IAM Service Account creation process is initiated, Cloud Formation template will be created to provision the required resources in AWS. To view the status of the service account, perform the below steps:
- Login to AWS portal and select Cloud Formation under Services. A list appears showing the status of all the stacks
- The initial status is CREATE_IN_PROGRESS and on successful completion, status changes to CREATE_COMPLETE
Successful IAM Service Account¶
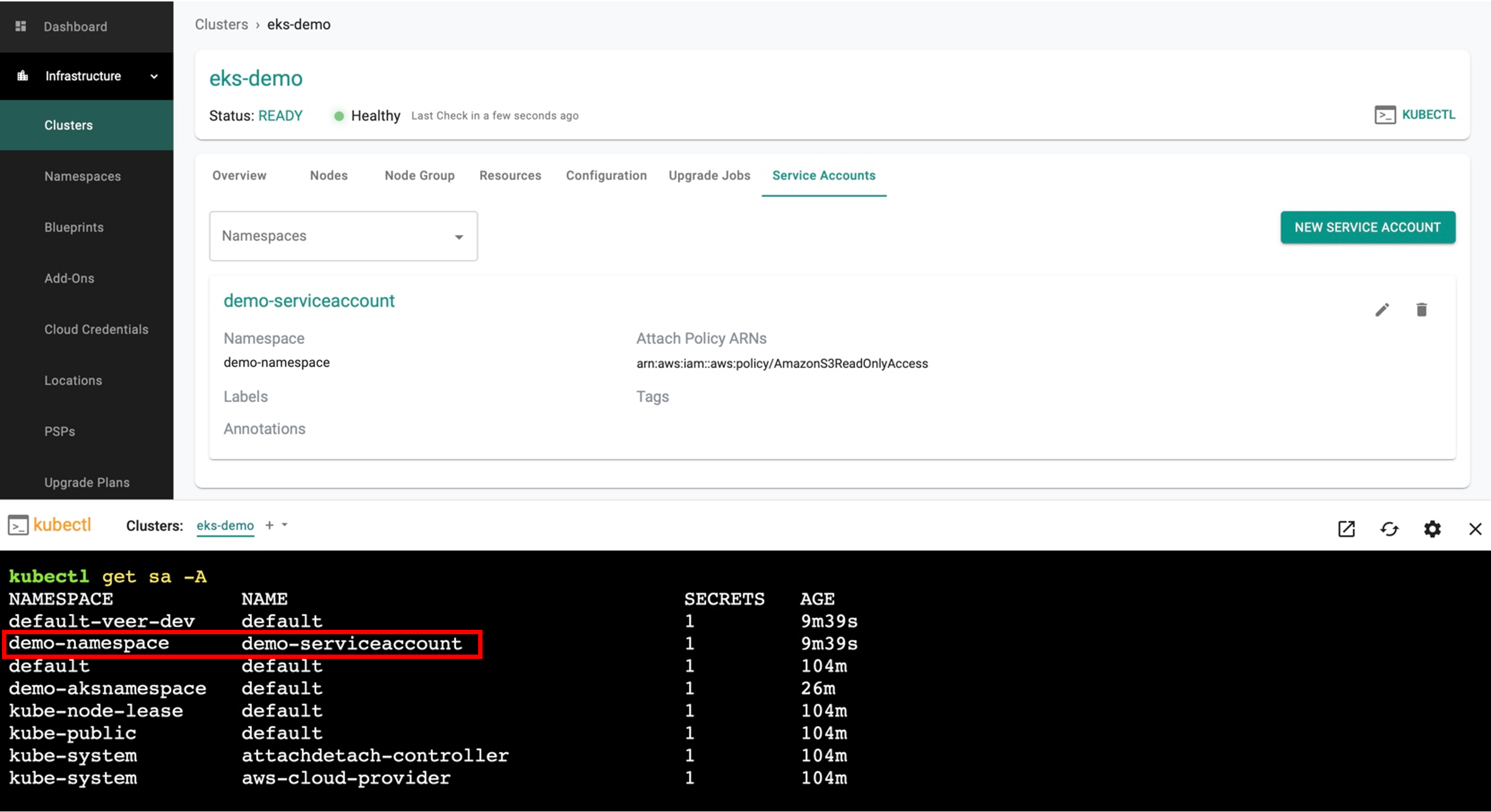
User can view the created IAM Service Account in the Controller
Provisioned Service Accounts¶
To view the service account created in a cluster, click KUBECTL and enter the command get sa -A**