Challenges of Container Vulnerability Management¶
In the dynamic landscape of modern application development, containers have emerged as the cornerstone of microservices, revolutionizing the way software is deployed and managed. However, as we celebrate the agility and efficiency brought by containers, a critical concern looms large in the background — the chaotic state of vulnerability management within the container ecosystem. Several noteworthy challenges persist :
-
Current-generation container vulnerability scanners lack contextual considerations and actionable suggestions, posing difficulties in effectively addressing and resolving vulnerabilities.
-
Security teams, accustomed to traditional methods, face challenges in adapting to container security, where the absence of clear context and mitigation measures complicates the resolution of issues.
-
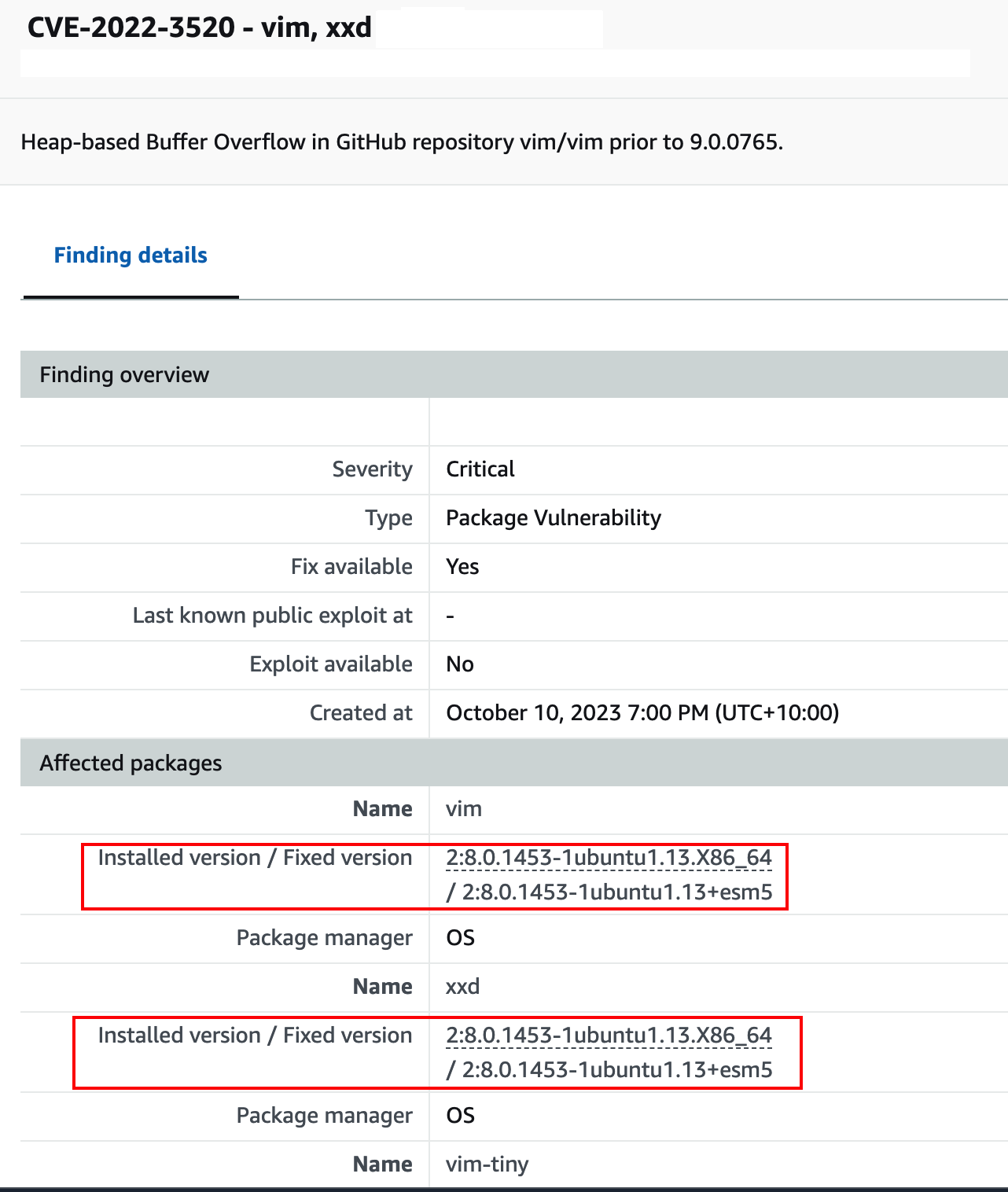
Open source container projects exhibit inconsistent practices in disclosing vulnerabilities and providing information about fixed versions, further complicating the task of maintaining a secure environment.
The Traditional Precision: Packages and Mitigation Steps¶
Traditionally, vulnerability management tools excelled at detecting vulnerabilities in packages, offering precise assessments and actionable mitigation steps. Contrastingly, container vulnerability scanning tools seem to be struggling to keep pace with the complexities of the containerized world, leaving security teams grappling with incomplete information and impractical solutions.
Context Matters: The Challenge in Container Vulnerability Scanning¶
Consider the conventional scenario: a vulnerability is detected in a package on an Linux system, and the scanner not only identifies the issue but also suggests a fixed version of the package. Mitigation is as simple as upgrading to the suggested package version. This level of clarity and guidance is noticeably absent when it comes to containers.
Missing Pieces: Context and Actionable Suggestions¶
Container scanners, in their current state, often fall short by merely scanning individual package layers and flagging vulnerabilities solely based on package usage within the container. The crucial missing elements here are context and actionable suggestions. What’s needed is an understanding of whether the detected vulnerability is even applicable to the container. A package might be configured or utilized in a way that renders it non-vulnerable, adding a layer of complexity that current scanners fail to address. Moreover, the absence of actionable suggestions for fixing container versions exacerbates the problem.
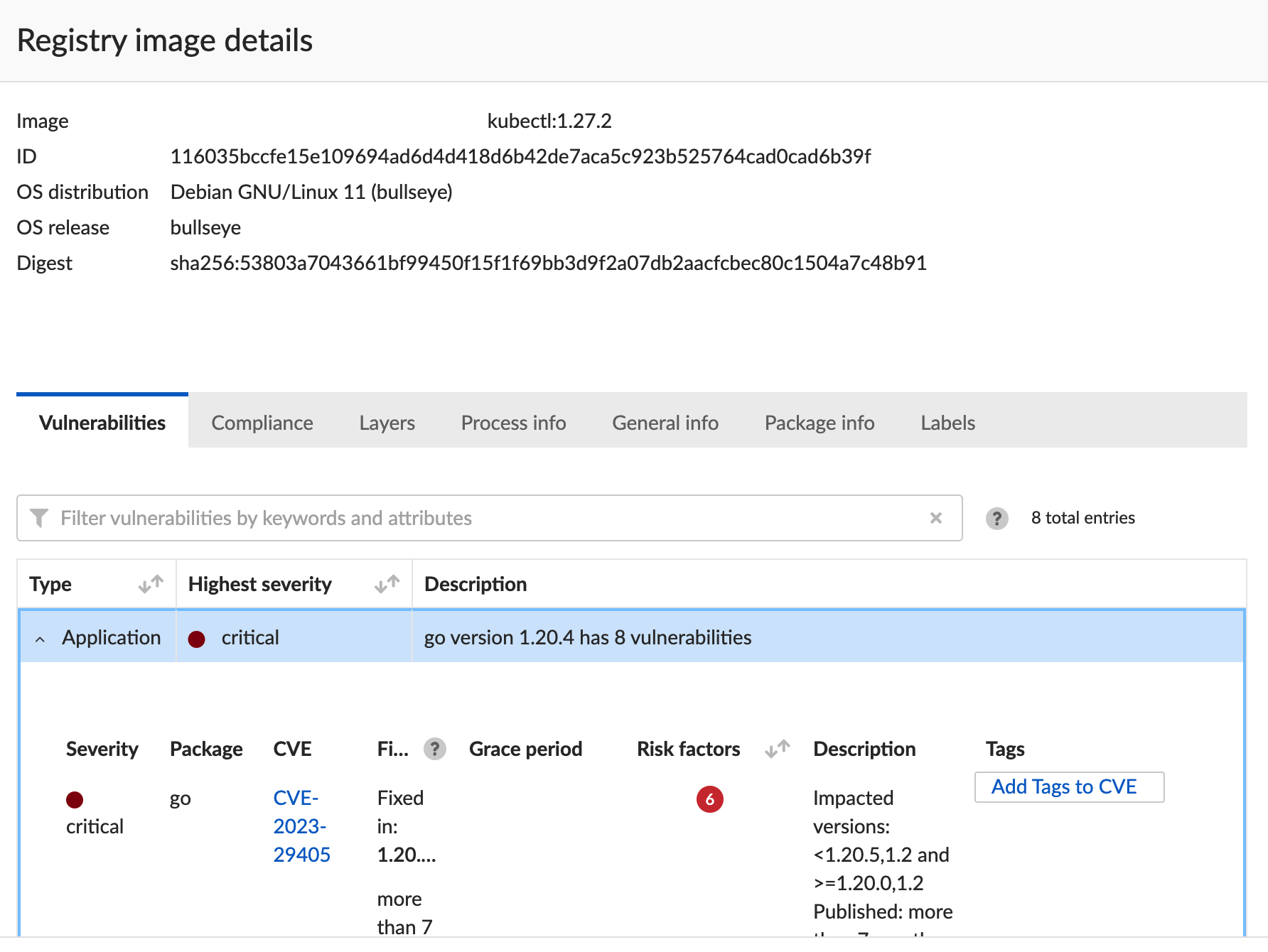
For instance, in below scanner output declares that container image kubectl:1.27.2 is vulnerable to 8 critical golang vulnerabilities. It suggests fix versions for golang. However it fails to:
-
Suggest a fix version for the container image. Without fixed container image information, there is no actionable information availaible to address the vulnerability to the end user.
-
Consider if the golang vulnerabilities are even relevant in context of the container application — kubectl. In this particular case, the golang issues raised are all build time issues related to use of cgo, which is not used at all by the kubectl application. Hence so called critical issues detected are not relevant at all.
The Hard Truth: Fixing Containers and Complications¶
While traditional tools suggest fixed versions for packages, container scanners leave users to grapple with the challenging task of fixing containers by applying patches to packages and recompiling — a task often beyond the capabilities of the average open-source user.
Call for Evolution: Intelligent Container Scanners¶
The crux of the issue lies in the need for container scanners to evolve into more intelligent tools. They must go beyond scanning individual package layers and consider the broader context in which packages are used within containers. Instead of merely suggesting fixed versions for packages, scanners should search upstream and recommend fixed container versions, providing security teams with practical and implementable solutions.
Navigating Unfamiliar Territory: Security Teams and Container Security¶
Compounding this challenge is the fact that many security teams, well-versed in traditional vulnerability management, find themselves at a loss when dealing with container security. Applying the same zero-tolerance approach for critical and high issues in packages across all containers is often unnecessary and irrelevant.
Beyond Blanket Approaches: Contextual Understanding¶
The lack of contextual understanding can lead to misguided efforts, as seen in cases where vulnerabilities in a Golang binary do not automatically translate to vulnerabilities in containers using that binary. The absence of a threat vector makes blanket recommendations ineffective and potentially detrimental to overall security.
The Silent Challenge: Lack of Open Source Project Transparency¶
Adding another layer of complexity is the often-overlooked issue of open source projects associated with containerized applications. Many of these projects do not consistently publish vulnerabilities and fixed versions, creating a significant hurdle in determining the appropriate remediation actions.
Conclusion: The Imperative Shift for Container Security¶
In conclusion, the current state of container vulnerability management demands a paradigm shift. Container scanners must transcend their current limitations, providing security teams with nuanced insights into true vulnerabilities. This entails considering contextual factors and suggesting actionable results — such as upgrading to specific container versions — rather than leaving security teams to decipher the intricacies and navigate the mess on their own. The evolution of container security tools is not just a necessity; it is an imperative step towards securing the future of modern application development.