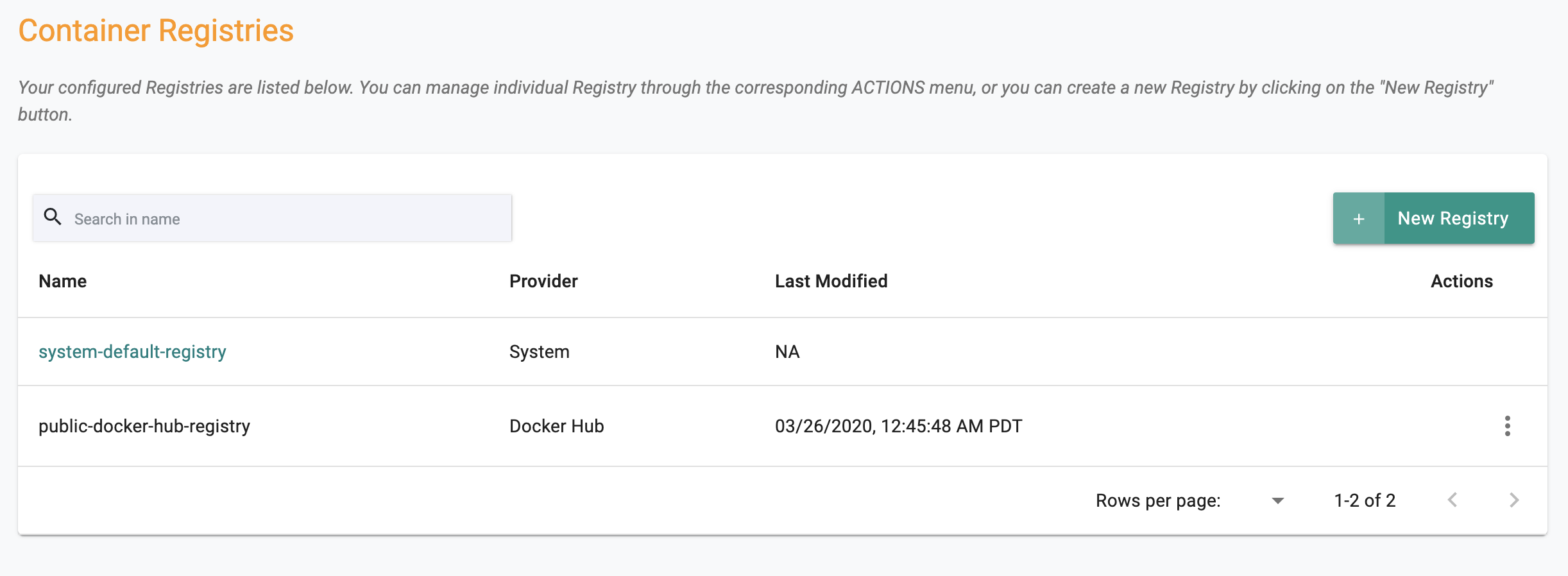
Container Registry
Overview¶
Customers can use their existing Container Registry or the integrated Container Registry on the Controller.
Workloads based on the "workload wizard" can be configured to securely access enterprise container registries. The following Container Registry Providers have been tested for compatibility.
- Docker Hub (Public)
- Docker Hub (Private)
- AWS ECR
- GCP GCR
- Quay by RedHat
- Nexus by Sonatype
- JFrog Artifactory
- Microsoft MCR
- System Container Registry
- Any Docker Compatible Registry
Registry Integrations¶
The Controller provides deep integrations with 3rd party container registry providers to help streamline and secure access to it.
Credential Configuration¶
Users can securely configure and use registry provider specific access credentials.
Image Pull Secret Injection¶
When a workload is published on a managed cluster, the Controller will ensure that the necessary "image pull secrets" are automatically injected into the underlying Kubernetes "secrets" resources.
Kubernetes handles the pulling and running of the image once the pod is configured with appropriate imagePullSecrets.
Docker Hub¶
Docker Hub is a service provided by Docker for finding and sharing container images. In addition to public repositories, organizations can also create private (credential protected) repositories. Docker Hub is also one of the locations where ISVs publish their official images.
Public Repositories¶
The Controller provides out of box support for "public repositories" in Docker Hub. No special configuration is required to access images from DockerHub's public repositories.
Private Repositories¶
For Private Repositories on Docker Hub, create a new Registry Profile
- Click on New Registry
- Provide a name and access credentials
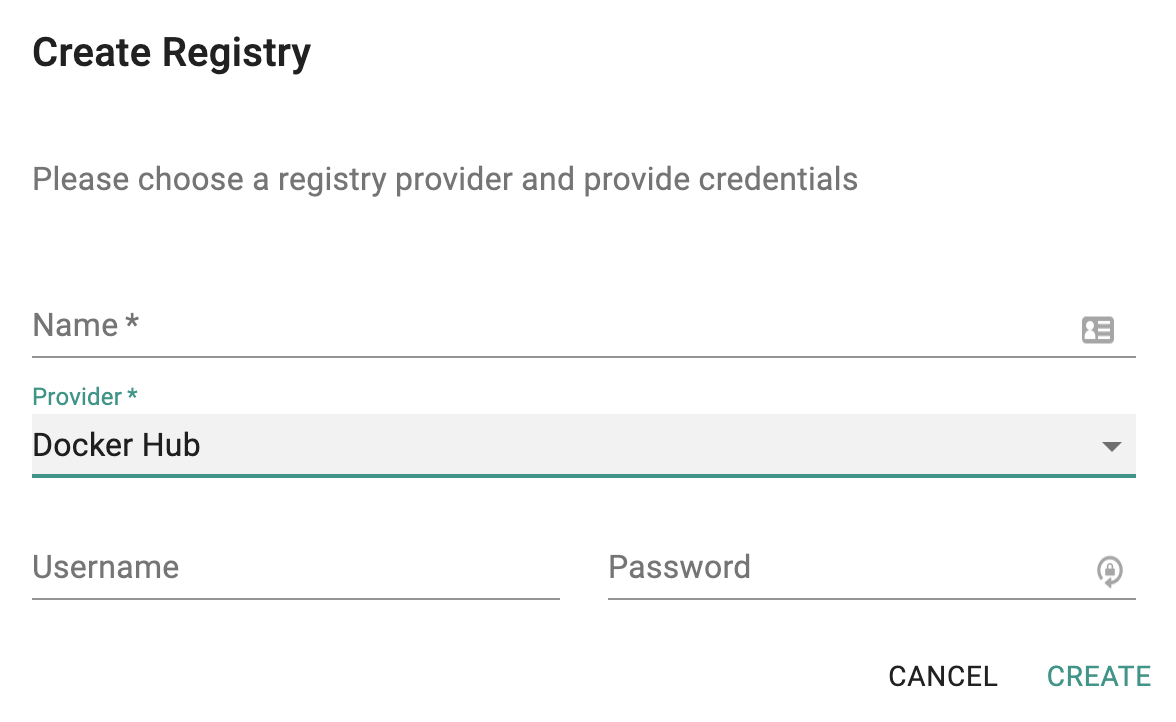
The Controller will automatically perform validation of the access credentials to ensure that downstream clusters will have access to the private repo to pull the required container images.
Once the registry profile has been created, users can provide the repository name, image and tag directly in the container configuration page.
AWS ECR¶
AWS's Elastic Container Registry aka ECR is a fully-managed Docker container registry that makes it easy for developers to store, manage, and deploy Docker container images.
- ECR eliminates the need to operate your own container repositories or worry about scaling the underlying infrastructure.
-
ECR hosts your images in a highly available and scalable architecture, allowing you to reliably deploy containers for your applications.
-
ECR is AWS region specific
- The registry endpoint is of the form aws_account_id.dkr.ecr.region.amazonaws.com
- Cross account access is supported by ECR which is controlled by Amazon ECR Repository Policies
Step 1: AWS Permissions¶
The ECR registry service allows users to provide fine-grained permissions that are tied into Amazon’s IAM service. Configure the minimum permissions required to pull images from ECR.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ecr:GetAuthorizationToken",
"ecr:BatchCheckLayerAvailability",
"ecr:GetDownloadUrlForLayer",
"ecr:GetRepositoryPolicy",
"ecr:DescribeRepositories",
"ecr:ListImages",
"ecr:DescribeImages",
"ecr:BatchGetImage"
],
"Resource": "*"
}
]
}
Step 2: Registry Profile¶
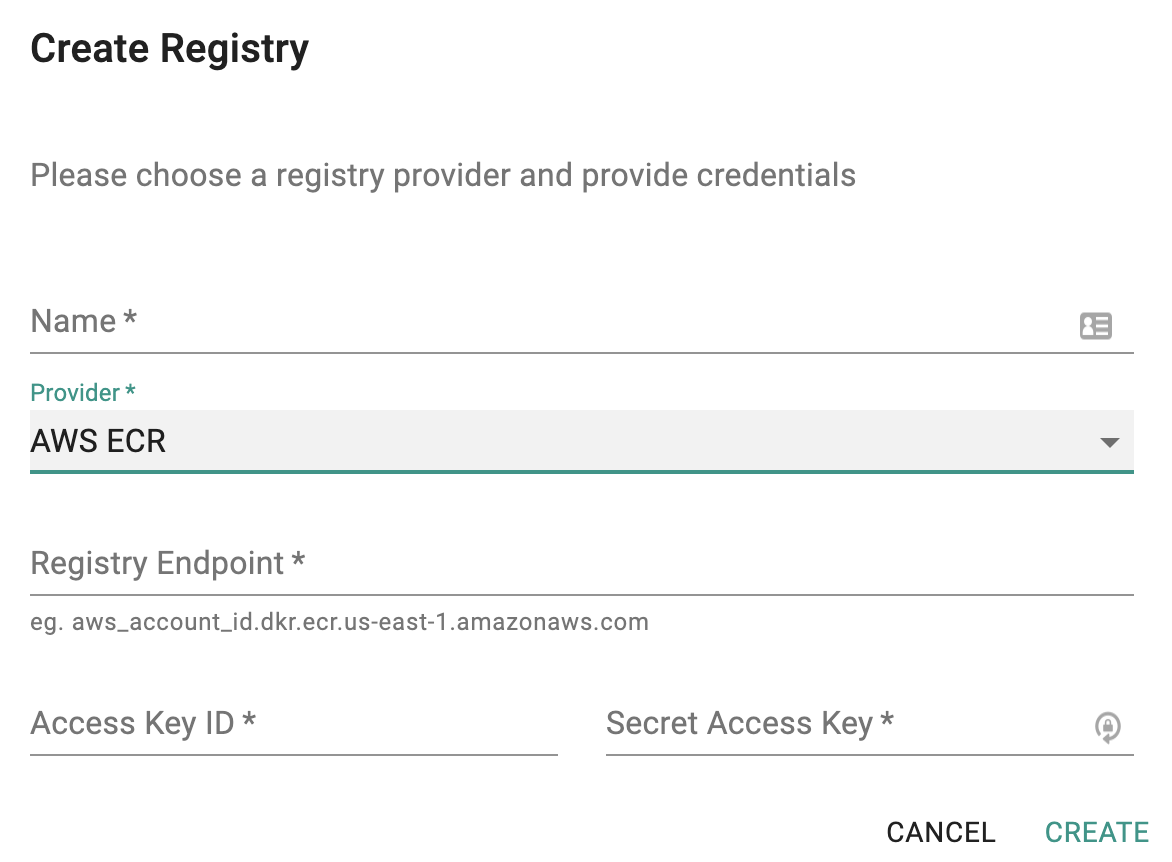
In the Web Console, Select Registry
- Click on New Registry
- Provide the registry endpoint information (An example of an ECR Endpoint is "6391436758854.dkr.ecr.us-west-1.amazonaws.com")
- Provide access credentials for programmatic access to AWS
Authentication
Access to ECR is controlled by AWS IAM. AWS requires an IAM user to request a temporary credential to access the registry. Once issued, this temporary credential is valid for 12 hours. The in-cluster K8s management operator will automatically refresh the credentials before they expire to ensure that managed clusters never lose access to container images in ECR.
Step 3: Use Image from ECR¶
Once the registry profile for AWS ECR has been created, you can use it directly in the container configuration
- In the registry dropdown, select the ECR registry profile
- Provide the "repository" and "tag information
Before the workload is published, the Rafay platform will "validate" whether the repository and image exists and is accesible using the credentials. This proactive check ensures that an "image pull" failure does not occur at the managed clusters.
GCP GCR¶
The controller enables customers to deploy containers from their GCR repos. GCP has multiple registry endpoints
- gcr.io currently hosts the images in the United States
- us.gcr.io hosts the image in the United States, in a separate storage bucket from images hosted by gcr.io
- eu.gcr.io hosts the images in the European Union
- asia.gcr.io hosts the images in Asia
Users can create different registry profiles if they need to use images from different registry endpoints.
Step 1: GCP Permissions¶
Set the following permissions for the "service account" you intend to use. This is required to pull images from the GCR repos.
- storage.objects.get
- storage.objects.list
Step 2: Registry Profile¶
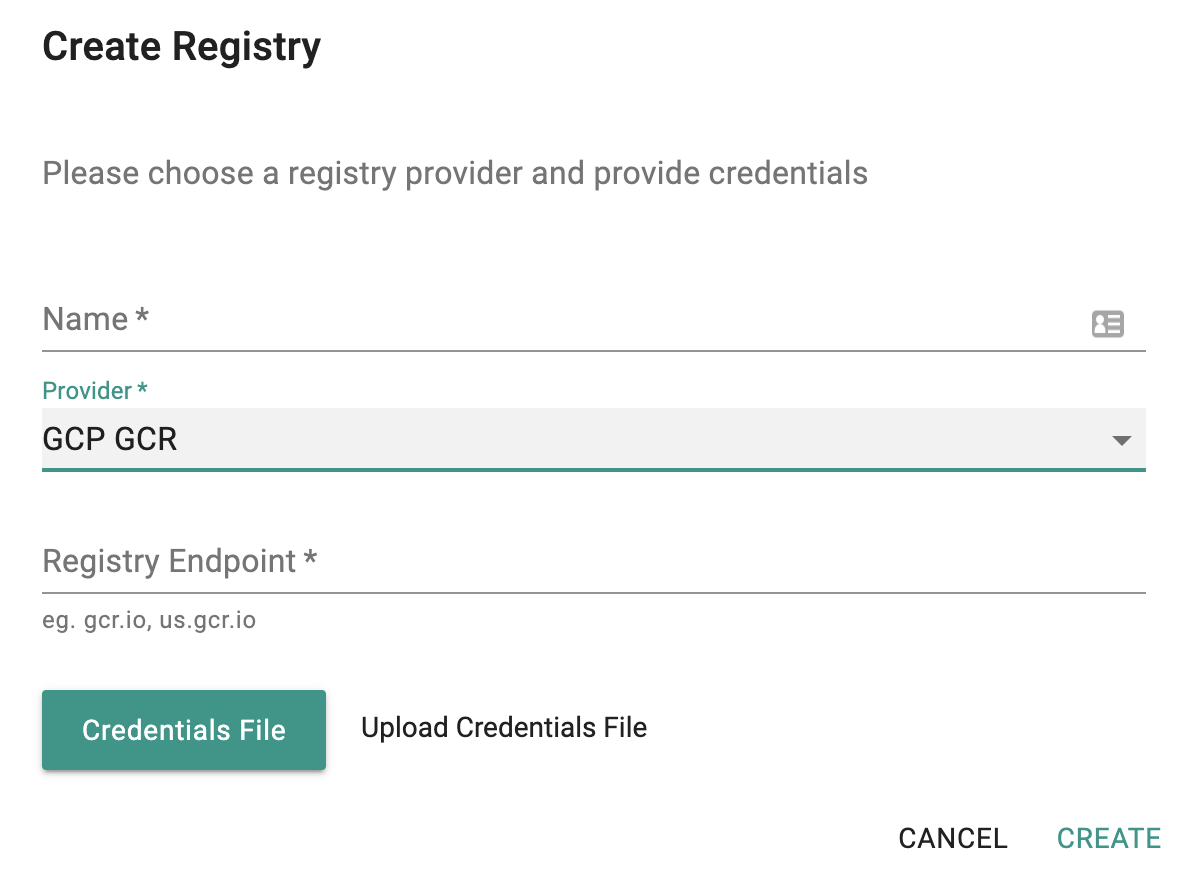
In the Web Console, Select Registry
- Click on New Registry
- Provide the registry endpoint information
- Provide access credentials information (service account JSON)
Unlike AWS ECR, the credentials are long-lived and do not require refreshes unless they are explicitly rotated. A GCR Repository URI is of the form [HOSTNAME]/[PROJECT-ID]/[IMAGE].
Step 3: Use Image from GCR¶
Once the registry profile for GCR has been created, you can use it directly in the container configuration
- In the registry dropdown, select the GCR registry profile
- Provide the "repository" and "tag information
Before the workload is published, the Rafay platform will "validate" whether the repository and image exists and is accesible using the credentials. This proactive check ensures that an "image pull" failure does not occur at the managed clusters.
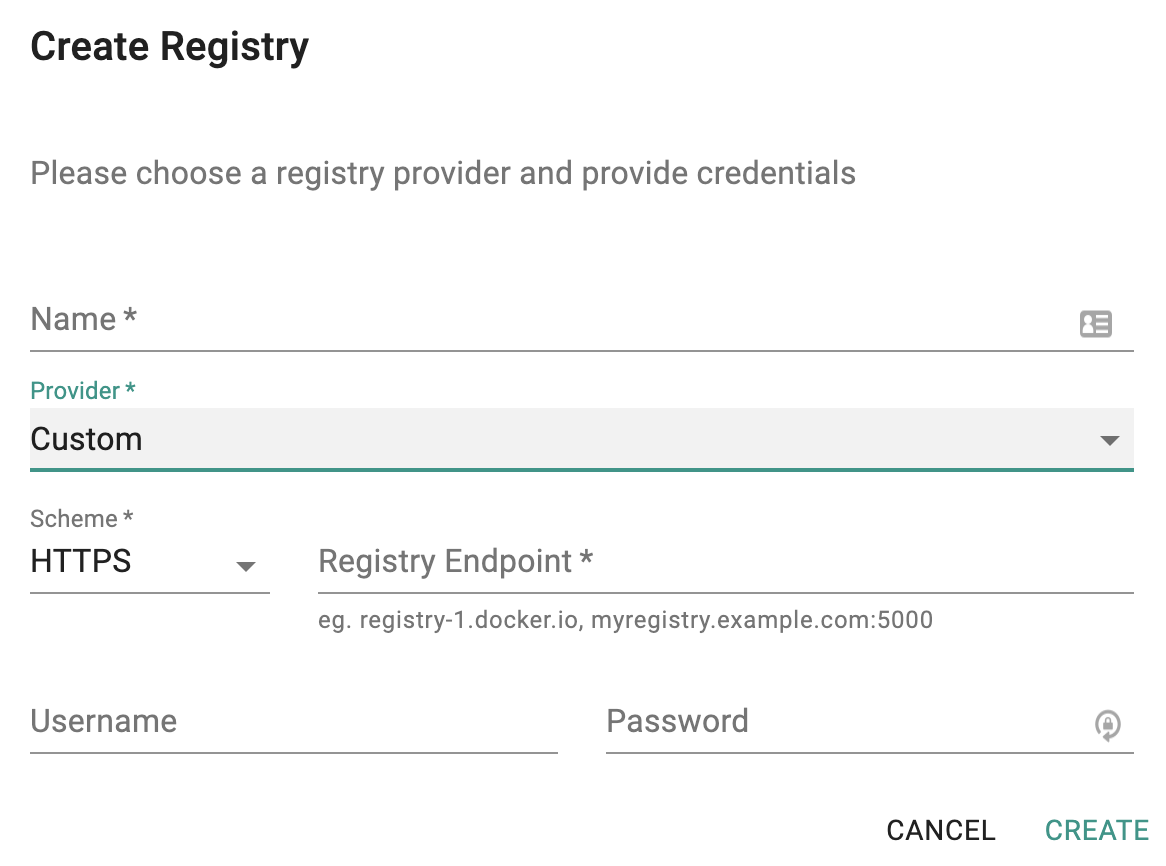
Custom Registry¶
Use the "Custom Registry" option for access to any Docker Compatible Registry. For access to repositories on JFrog, Nexus and Quay can be quickly configured using this option.
- Provide a name for the Registry (ideally something your developers can instantly recognize)
- Select "Custom" from the dropdown
- Provide the Registry Endpoint (NOTE: Self signed certificates are not supported by the https endpoint)
- Provide authentication credentials
Microsoft Container Registry (MCR)¶
Microsoft Corporation distributes their images/samples via unauthenticated access from Microsoft Container Registry (MCR). The Microsoft Container Registry (MCR) hosts popular repositories for popular container images provided by Microsoft Corporation (For example, the .NET Core container images etc.)
To enable access to MCR,
- Create a new registry (provider) called MCR etc
- Select "Custom" for Provider
- Enter "mcr.microsoft.com" for Registry Endpoint
- Do Not enter username and password
Now you can use the MCR registry profile in your container configs.
System Container Registry¶
Users that have not yet selected a corporate Container Registry may be interested in using the Integrated Container Registry in the Controller. This supports Docker's Image Manifest v2.
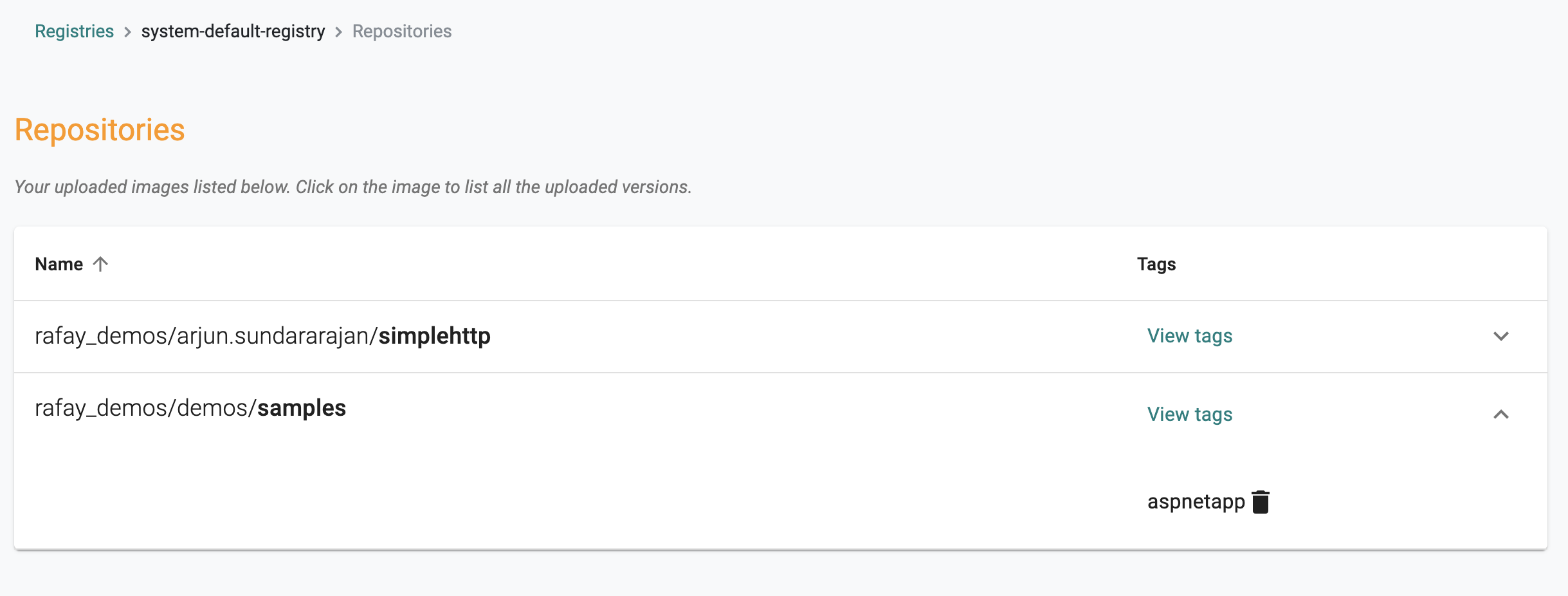
Accessing the Registry¶
- Users can use a standard Docker client to securely interact with the Integrated Container Registry.
- Users can also view/manage their images in the Integrated Container Registry via the Console.
Using the Registry¶
For workloads based on the "workload wizard",
- In the container configuration, select "System Default Registry" from the dropdown
- Select the "image name" and "tag" from the drop down list